21 nails in Exim mail server: Vulnerabilities enable ‘full remote unauthenticated code execution’, millions of boxes at risk
Researchers at security biz Qualys discovered 21 vulnerabilities in Exim, a popular mail server, which can be chained to obtain “a full remote unauthenticated code execution and gain root privileges on the Exim Server.”
Exim is a mail transfer agent (MTA), responsible for receiving and forwarding email messages. It runs primarily on Unix or Linux and is the default MTA on Debian – though Ubuntu and Red Hat Enterprise Linux use Postfix by default.
Some hosting companies use Exim to provide email services to their customers, and it was also popular in universities and other educational institutions (it was initially developed at the University of Cambridge in 1995) though many of these have transitioned to Office 365 or Google email, not least Cambridge itself.
According to one recent survey nearly 60 per cent of mail servers visible on the internet use Exim, followed by Postfix at 34 per cent. Qualys said a Shodan search revealed nearly 4 million Exim servers exposed to the internet.
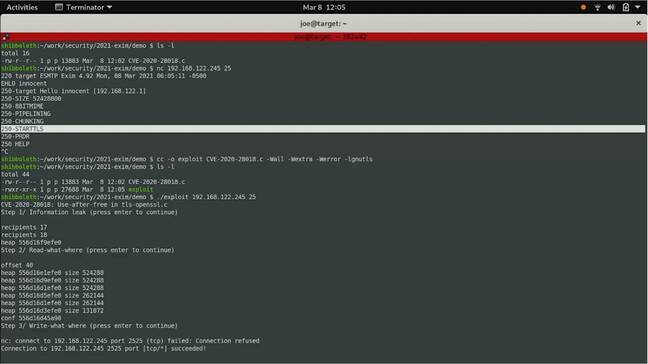
Qualys demonstrates a proof of concept exploit against the Exim mail server, achieving root access to the remote server
The Qualys researchers have now reported on 21 critical vulnerabilities discovered via a code audit, 10 of which can be exploited remotely.
The local vulnerabilities are also an issue, as they can enable local users to escalate privileges to root. Most of the vulnerabilities are longstanding, the researchers say, with some going back to the beginning of its Git history (the Exim source code repository).
A proof of concept video shows an exploit (developed by Qualys but not publicly available) in action. “To run the exploit, all we need to do is point it to the target Exim server IP endpoint,” explained researcher Bharat Jogi. The exploit starts with a use after free bug (where memory is referenced after it has been freed), then discovers where Exim’s configuration resides in memory, and modifies it to “execute an arbitrary command.”
This opens a Netcat shell, at which point the attacker has a local terminal as the Exim user. A further vulnerability allows the attacker to take ownership of any file on the system, because part of the Exim code runs as root. Ownership of the system password file then gives the user full root privileges.
Timing was tight
Qualys said it informed the Exim security team of some vulnerabilities on 20 October 2020, followed by a further list on 29 October. Exim maintainers gave Qualys access to its Git repository both to review and to assist with writing patches. The timing was tight, though: patches were not completed until 24th February, and the Exim team did not give access to packagers and maintainers, who are responsible for providing Exim updates to users, until 27th April. The vulnerabilities were disclosed yesterday, 4 May, a date which Qualys said was agreed with the Exim project.
This timeline inevitably means that many servers were not patched at the time of the announcement. Debian released a security advisory yesterday for its current stable distribution, Buster. At the time of writing, the packages for Debian 9 (Stretch), which is end of life but in long term support, had not yet been updated. All Exim versions before Exim 4.94.2 are vulnerable.
The Qualys team chose the name 21 Nails as a pun on “21 vulnerabilities in a ‘Mail’ transfer agent.” Nothing to do with coffins, though the new vulnerabilities will reinforce claims that running Postfix, which was designed with security in mind (it was also called Secure Mailer) is a better idea from a security perspective.
Email servers are an obvious attack point because they are of necessity internet-accessible, as evidenced by another recent security incident, called Haffnium, that affected Microsoft Exchange. The number of Exim instances out there is far greater than the number of Exchange servers, although the corporate nature of Exchange may make it a more attractive target. ®
READ MORE HERE

