‘Oh sh..’ – the moment an infosec bod realized he was tracking a cop car’s movements by its leaky cellular gateway
Black Hat If you want to avoid the cops, or watch deliveries and call-outs by trucks and another vehicles in real-time, well, there’s potentially not a lot stopping you.
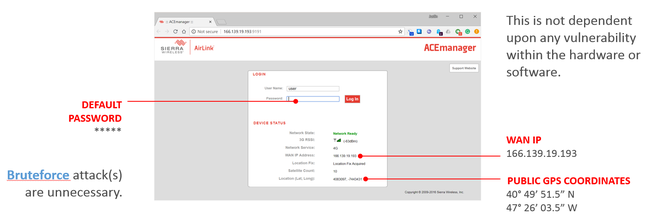
Security researchers have found more than 100,000 internet-facing cellular gateways, some of which broadcast their exact whereabouts to the world. These particular devices are fitted to fleet vehicles, police cars, ambulances, and so on, blab their coordinates on webpages served by their built-in web servers from their public IP addresses. Thus, they and their vehicles can be found, inspected, and stalked using port scans and search engines, such as Shodan.io.
This security blunder was found by accident after an investigation by F5 Labs into Linux malware took an interesting turn, leading the team to stumble across the gossiping gateways. Since then more than 13,500 warning notes have been sent out to people making and operating exposed equipment, we’re told, with two replies were received – one of which was Sierra Wireless, the manufacturer of most of the discovered gateways.
The location information is leaked from misconfigured cellular gateways that are used to connect equipment in a vehicle to the internet via a cellphone network, or provide Wi-Fi that routes connections out to the outside world via a cellular connection.
Gateways from Sierra Wireless, Cradlepoint, Moxa, and Digi have been found on the public internet poorly secured by their owners, according to F5. They display the unit’s physical location in a device status box on the administrator login page, and possibly still use the username and password defaults of user/12345 on Sierra kit.
Once logged in, a miscreant can meddle with the router’s settings, snoop on it, disable it, and so on. Sierra built eight out of ten of the discovered gateways, and lists California Highway Patrol, Danish National Police, South Wales Police, Seattle Fire Department, and many others, as its customers. Obviously, not every shipped box is subsequently misconfigured by its operators, however, clearly, quite a few are.
“What happens when people go after police officers because they know where they live,” Justin Shattuck, principal threat researcher at F5 Networks, who gave a Black Hat USA talk this week about the findings, told The Register. “Using GPS we know where they buy their donuts, how long to get their orders – we know where they are down to the metre.”
Shattuck and his colleagues spotted something was up in late October 2016 while investigating a Bashlight malware infection at a major European airport: the software nasty, which brute-forces its way into systems, was found lurking on a digital sign that showed arrival and departure times.
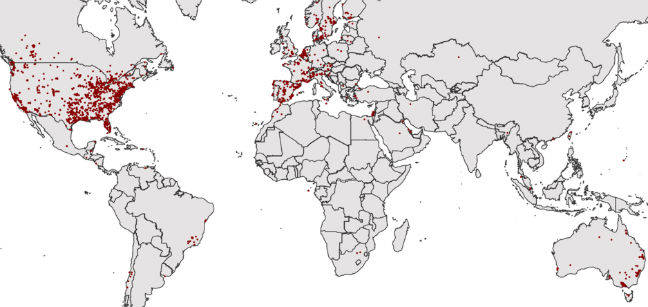
The team scanned the rest of the airport’s network that month, and found various Sierra Wireless cellular gateways, one of which was publicly accessible. They took their search wider, and found 49,962 internet-facing Sierra Wireless gateways, 84 per cent of which were in the US. By July this year, that was up to 105,400 hosts, with a significant amount in Europe.
The team began looking at what sort of gateways were broadcasting their locations to the public internet. Many were fixed in place, however, some went through regular movements around cities, often during eight or ten-hour shifts. IoT security biz Loryka’s Scott Harvey, who worked with the F5 team, told The Register of the moment when he realized what kind of gateway he was following. A cop car in San Francisco.
“We could get the coordinates in real time and track the route of cars,” he explained. “We saw a vehicle in San Francisco go across town and park. When we checked on Google Streetview, we saw the spot was at the police station behind a controlled-access gate. That was an ‘oh shit’ moment – that’s exactly what I said.”
It’s going to take a lot of effort to address these information leaks, as it will require alerting users to fetch and install improved firmware, when available. It would also be nice if equipment prompted people to change their passwords after the first login, and locked down access to particular VPNs or login keys. The hardware makers contacted by The Register for comment this week had no spokespeople available to talk.
“If it weren’t for white hat researchers, we would be finding out about discoveries like this from news media after a terror attack, which is entirely too late,” the team – Shattuck, Harvey and Sara Boddy and Preston Crowe – claimed. “The right thing to do is avoid the risk by remediating now.” ®
Sponsored: Following Bottomline’s journey to the Hybrid Cloud
READ MORE HERE