Insane in the domain: Sea Turtle hackers pwn DNS orgs to dash web surfers on the rocks of phishing pages
Internet domain registrars and at least one registry were hijacked to change certain websites’ DNS settings so that visitors to said sites were in fact directed to password-stealing phishing pages, researchers detailed on Wednesday.
It is believed this is the first time state-backed miscreants have compromised web domain organizations, including those handling country-code level top-level domains, in order to phish specific targets.
Essentially, once inside a registry or registrar, the hackers would change the DNS records for a particular website or server, so that when people tried to visit that system, their browsers or software would be told to connect to machines masquerading as the legit service. At that point, the malicious clones could collect usernames, passwords, and other sensitive information submitted by hoodwinked users, and log into the real services as them.
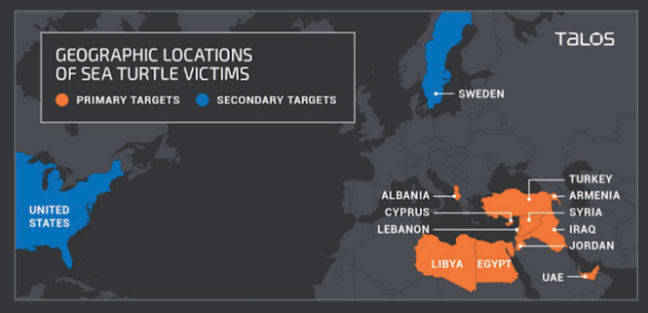
In their report out this week, eggheads at Cisco Talos outlined how the crew of miscreants, known as the Sea Turtle group, manipulated DNS entries to harvest user credentials from 40 specifically targeted companies and government organizations across 13 countries in the Middle East and North Africa. Those credentials were then used to infiltrate said businesses and organizations.
Computer systems within a registry and registrar were infected by tricking employees into opening spear-phishing emails laden with malware from sometime around January 2017, and continuing through the first quarter of 2019. Typically, registries manage top-level domains, such as .com or .org, and the public buy and sell domains using these TLDs via registrars.
The cyber-attacks on these domain management organizations were so serious that the US Department of Homeland Security issued an alert warning internet users in January to lock down their DNS records to avoid similar hijackings.
Talos noted that multiple vulnerabilities were exploited by the miscreants to break into the domain organizations. One of those was CVE-2017-3881, a remote code execution hole in the Cluster Management Protocol for Cisco IOS and IOS XE routers that would allow remote takeover via telnet connections.
“While this incident is limited to targeting primarily national security organizations in the Middle East and North Africa, and we do not want to overstate the consequences of this specific campaign, we are concerned that the success of this operation will lead to actors more broadly attacking the global DNS system,” Team Talos – Danny Adamitis, David Maynor, Warren Mercer, Matthew Olney, and Paul Rascagneres – said in its summary of the operation.
“DNS is a foundational technology supporting the Internet. Manipulating that system has the potential to undermine the trust users have in the Internet.”
We’re told the DNS entries for the targeted businesses and government entities were tampered with for a short period of time, ranging from minutes to a few days, indicating this was a highly focused espionage campaign.
The malicious credential-harvesting sites – that people working for the targeted companies and entities were redirected to via the DNS hijacking – used HTTPS certificates created by the snoops, using, say, Let’s Encrypt or Comodo, to make the phishing pages look legit.
Once the miscreants gained entry to a target’s network using the obtained login details, the infiltrated organization’s internal SSL certs would be snatched and used to briefly man-in-the-middle intercept VPN connections from staff to the spied-on company or government department. The hackers were, we’re told, able to run malicious servers that masqueraded as Cisco Adaptive Security Appliance (ASA) products to perform this eavesdropping.
We have been warned
Attacks on DNS systems have been a known danger for some time now. Going back more than a decade, researchers have warned of various ways scumbags could undermine the lookup system to funnel netizens into the hands of malicious servers.
One of the Sea Turtle-hacked registries, Swedish-based NetNod, has acknowledged it was pwned to redirect Saudi Arabian .sa domains to malicious boxes masquerading as legit corporate or government login portals.
As for protections, Talos is recommending folks opt for a DNS locking service, so that any changes to a site or server DNS record will require explicit permission from the domain owner. They also recommended following the usual best practices, such as keeping up to date on security patches, using multi-factor authentication, and having a plan prepared for network-wide password resets in the event of an attack. ®
Sponsored: Getting More From Less
READ MORE HERE