Top 5 use cases to help you make the most of your Cloud Access Security Broker
The number of apps and the flexibility for users to access them from anywhere continues to increase. This presents a challenge for IT departments in ensuring secure access and protecting the flow of critical data with a consistent set of controls.
Cloud Access Security Brokers (CASBs) are a new generation of security solutions that are essential to any modern security strategy. CASBs provide a centralized experience that allows you to apply a standardized set of controls to the apps in your organization. The term Cloud Access Security Broker was first introduced by analyst firm Gartner and has since been one of the fastest growing security categories and is considered one of the top 10 security projects for companies to implement by 2020.
Microsoft Cloud App Security is a CASB that allows you to protect all apps in your organization, including third-party apps across cloud, on-premises, and custom applications. Powered by native integrations with Microsoft’s broader product ecosystem, Cloud App Security delivers state-of-the-art security for multi-cloud environments.
Due to the fast pace of the market, the capability set of CASBs continues to grow, making it increasingly challenging for customers to decide how to get started.
Today, we explore five of the top 20 use cases for CASBs we identified as giving you an immediate return on your investment with very little deployment effort needed before moving on to more advanced scenarios.
Use case #1: Discover all cloud apps and resources used in your organization
No matter where you are in your cloud journey, many of your users likely started leveraging cloud services a long time ago and have stored corporate data in various cloud applications.
A CASB provides you with full visibility over all data stored in sanctioned and connected cloud apps. It gives you deep insights about each file, allowing you to identify if it contains sensitive information, the owner and storage location, as well as the access level of the file. Access levels distinguish between private, internal, externally shared, and publicly shared files, allowing you to quickly identify potentially overexposed files putting sensitive information at risk.
Cloud App Security gives you multiple options to get started with Cloud Discovery. You can leverage firewall logs, an existing Secure Web Gateway, or the unique, single-click enablement via Microsoft Defender Advanced Threat Protection (ATP).
To learn how to get started with app discovery, read Discover and manage shadow IT in your network.
Use case #2: Identify and revoke access to risky OAuth apps
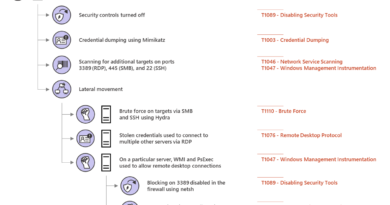
In recent years, OAuth apps have become a popular attack vector for adversaries. Hacker groups such as Fancy Bear have leveraged OAuth apps to trick users into authorizing the use of their corporate credentials, for example by duplicating the UI of a seemingly trustworthy platform.
A CASB enables you to closely monitor which OAuth apps are being authorized against your corporate environment and either manually review them or create policies that automatically revoke access if certain risky criteria are met. Key threat indicators are the combination of an app that has requested a high level of permissions, while having a low community use status, indicating that it’s not commonly found in other organizations and therefore more unlikely to be trustworthy.
Once you’ve enabled app discovery, all you need to do is connect the relevant apps like Office 365, Salesforce, or G-Suite to the service. You’re then alerted when new risky OAuth apps are authorized, so you can start managing them.
To learn more about how to get started with app discovery, read Manage OAuth apps.
Use case #3: Identify compromised user accounts
Identity attacks have increased by more than 300 percent over the past year, making them a key source of compromise and the number one threat vector for organizations.
A CASB learns the behavior of users and other entities in an organization and builds a behavioral profile around them. If an account is compromised and executes activities that differ from the baseline user profile, abnormal behavior detections are raised.
Using built-in and custom anomaly detections, IT is alerted on activities, such as impossible travel, as well as activities from infrequent countries, or the implementation of inbox forwarding rules where emails are automatically forwarded to external email addresses. These alerts allow you to act quickly and quarantine a user account to prevent damage to your organization. All you have to do is connect the relevant apps to Cloud App Security and activate our built-in threat detection policies.
To learn how to get started, read Monitor alerts in Cloud App Security.
Use case #4: Enforce DLP policies for sensitive data stored in your cloud apps
Cloud services such as Office 365 or Slack are key productivity solutions in many organizations today. Consequently, sensitive corporate data is uploaded and shared across them.
For existing data, a CASB solution can help you identify files that contain sensitive information and it provides several remediation options, including removing external sharing permissions, encrypting the file, placing it in admin quarantine, or deleting it if necessary.
Additionally, you can enforce data loss prevention (DLP) policies that scan every file as soon as it’s uploaded to a cloud app, to alert on policy violations and automatically apply data labels and relevant restrictions to protect your information. These policies can be created using advanced techniques such as data identities, regular expressions, OCR, and exact data matching.
To learn how to get started with a centralized DLP strategy across your key apps, read File policies.
Use case #5: Enforce adaptive session controls to manage user actions in real-time
In a cloud-first world, identity has become the new perimeter—protecting access to all your corporate resources at the front door.
Cloud App Security leverages Azure Active Directory (Azure AD) Conditional Access policies to determine a user’s session risk upon sign-in. Based on the risk level associated with a user session, you can enforce adaptive in-session controls that determine which actions a user can carry out and which may be limited or blocked entirely. This seamless identity-based experience ensures the upkeep of productivity, while preventing potentially risky user actions in real-time. The adaptive controls include the prevention of data exfiltration by blocking actions such as download, copy, cut, or print, as well as the prevention of malicious data infiltration to your cloud apps by preventing malicious uploads or pasting text.
You can apply a standardized set of controls to any app in your organizations, whether it’s a cloud app, on-premises app, or a custom application, giving you a consistent set of controls to protect your most sensitive information.
To get started with our built-in templates for inline controls, read Deploy Conditional Access App Control for featured apps.
Starting a CASB project can be daunting given the breadth of capabilities and possibilities of configuration. The five use cases outlined above, and the focus on simple deployment and optimization of UI in Cloud App Security, will ensure that you can make the most of your investment and get started quickly. For more use cases, download our Top 20 CASB use cases e-book.
Learn more and provide feedback
As always, we want to hear from you! If you have any suggestions, questions, or comments, please visit us on our TechCommunity page.
READ MORE HERE