Google warns devs as it tightens Chrome cookie security: Stuff will break if you’re not clued up
You’ll have to tag those for cross-site use from February

Want a cookie? Some you do, some you don’t
Google is asking developers to get ready for more secure cookie settings to be implemented in Chrome 80 that is planned for release in February 2020.
The announced changes relate to the SameSite cookie attribute. First specified in July 2016, the SameSite attribute is set by the developer when the cookie is planted, and can be either “strict”, “lax”, “none” or omitted.
These settings (provided the browser supports them) control what happens when the browser requests content from a site other than the one you are visiting, such as when an ad is displayed. If it is set to strict, no cookies are sent to the third-party site. If it is set to lax, no cookies are sent unless you click a link that takes you to that site, in which case they are sent. If it is set to none, cookies set by the third-party site are always sent.
The SameSite attribute protects users from cross-site request forgery, where you are logged into site A and a script on site B impersonates you by sending a request to site A. If site A receives your session cookie, that request would appear to come from you.

Google puts Chrome on a cookie diet (which just so happens to starve its rivals, cough, cough…)
The major browsers, including Chrome, have supported this attribute for years, but Google has been gradually tightening security. Now it is moving to the next stage and implementing two changes:
- Cookies with no SameSite attribute specified will be treated as “lax” rather than “none”. Many developers do not bother to set this attribute so this will block a ton of cookies that are currently sent.
- Even cookies set to SameSite=None will not be sent across sites unless they are also tagged with the Secure attribute, requiring an encrypted connection.
Google is flagging up this issue for developers because the change in behaviour could break some features, such as single sign-on for business applications, if developers do not implement the required attributes. The change also impacts frameworks that set cookies. Enterprise administrators will be able to disable the new behaviour if necessary.
Although this is a welcome (perhaps overdue) change, it is not great for tracking protection, since advertisers that want to see tracking cookies can ensure that they set the required attributes. Users can of course set “Block third-party cookies” in the browser but this is off by default in most browsers since it breaks functionality. Firefox, for example, warns that blocking all third-party cookies “may cause websites to break”).
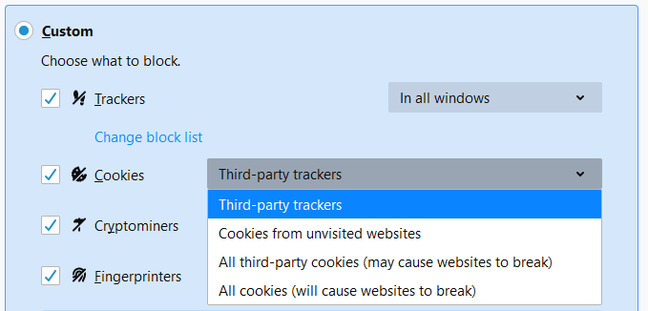
Firefox offers specific blocking of tracking cookies, and warns against blocking all third-party cookies
Mozilla has taken a more proactive line on the matter of tracking cookies by using a list of services that set tracking cookies and blocking third-party cookies from those sites only. This is now on by default in Firefox, but to use it in Chrome you need an extension.
Google takes a different view, arguing: “Blunt approaches to cookie blocking have been tried, and in response we have seen some user-tracking efforts move underground, employing harder-to-detect methods that subvert cookie controls. These methods, known as ‘fingerprinting,’ rely on various techniques to examine what makes a given user’s browser unique.”
Fingerprinting grabs what information it can about the user’s browser and machine to track identity without relying on cookies. Google is promising to “more aggressively restrict fingerprinting across the web”, but this is non-trivial and implementation will be imperfect. Google is also concerned about what it calls the “web ecosystem”, no doubt including its own income from advertising and investment in personalisation, which means it is not a neutral party in respect of this issue.
Google does note that, once we reach the point where all cross-site cookies have these attributes set, “browsers could offer users fine-grained controls to manage cookies that are only accessed by a single site separately from cookies accessed across multiple sites.” This is still challenging, though, since not all cross-site cookies are harmful.
Google’s efforts to tighten web standards are welcome in that as the maker of the dominant web browser, it has the clout to ensure that changes are implemented. That said, it lacks incentive to make its web browser the best in terms of privacy, which means rivals like Mozilla Firefox are likely to stay ahead in this area.®
Sponsored: How to Process, Wrangle, Analyze and Visualize your Data with Three Complementary Tools
READ MORE HERE