Sierra Wireless Patches Critical Vulns in Range of Wireless Routers

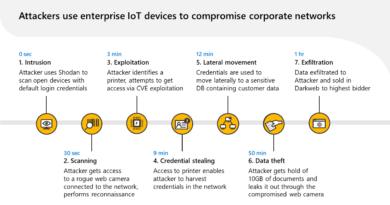
Sierra Wireless has patched two critical vulnerabilities for its range of wireless gateways that would leave the enterprise devices helpless to an array of remote threats, including the charms of the Reaper IoT botnet.
The more critical of the two (with a 9.4 CVSSv3 Temp Score) is a privilege-escalation bug (CVE-2018-10251), which could allow a remote attacker with no authentication whatsoever to the device to execute arbitrary code and gain full control of an affected system, including issuing commands with root privileges.
The second issue (slightly less alarming with an 8.4 CVSSv3 Temp Score) is also a privilege-escalation flaw (CVE-2017-15043) that allows remote code execution and device takeover; however, the vulnerability is due to insufficient input validation on user-controlled input in an HTTP request to the targeted device. An attacker would need to be in possession of router login credentials to exploit the vulnerability; after that, he or she could do so by sending a crafted HTTP request to the affected system.
The potential attack surface is large: Sierra Wireless has a footprint of more than 3 million AirLink devices. Both vulnerabilities affect AirLink Gateways LS300, GX400, GX/ES440 running 4.4.6 or older; and GX/ES450, RV50, RV50X, MP70, MP70E running 4.9.2 or older.
Armed with an exploit for either flaw, remote attackers could download malware to the devices to carry out cyber-espionage and corporate data exfiltration, perform man-in-the-middle attacks, move laterally to other parts of the network, and harvest credentials and other information that could be used for identity theft, business email compromise or other forms of fraud.
Sierra Wireless also warned that the devices could be recruited to the Reaper (or IoTroop) botnet, which was discovered last October enslaving IoT devices such as IP wireless cameras, routers and DVRs at a far faster rate than the Mirai botnet did in 2016. Qihoo 360 Netlab at the time observed, over the course of a single day, more than 2 million infected devices waiting to be processed in the C&C servers’ queue, and Check Point, which offered the initial analysis, said that the DDoS devastation it could cause could dwarf the Dyn attack.
Unlike Mirai, which relies on non-existent, default or weak passwords, Reaper uses exploits on unpatched devices to take control of them, harvesting the device’s credentials and maintaining contact with the C&C server for instructions.
Sierra Wireless said in a technical bulletin related to the HTTP request vulnerability referenced above that it has seen the botnet infecting Airlink gateways running older firmware, if they have outside internet connections and are using default user or viewer passwords.
LS300, GX400, GX/ES440 running firmware 4.4.5 or older and GX/ES450, RV50, RV50X, MP70, MP70E running 4.9.1 or older are ripe for the Reaper, the company said.
The good news is that, in all of these cases, the potential attack scenarios can be thwarted by simply upgrading to the latest version of firmware for the affected device.
Read More HERE