Oh-so-generous ransomware crooks vow to hold back from health organisations during COVID-19 crisis
Don’t take their word for it. Governments need to up their security game, says security firm

Ransomware is the most disruptive security risk for most organisations
Ransomware operators of DoppelPaymer and Maze malware stated that they will not target medical organisations during the current pandemic.
Laurence Abrams, who runs the security news site Bleeping Computer, reports that he made contact with “the operators of the Maze, DoppelPaymer, Ryuk, Sodinokibi/REvil, PwndLocker, and Ako Ransomware infections to ask if they would continue targeting health and medical organizations during the outbreak.”
The DoppelPaymer operators responded that “we always try to avoid hospitals, nursing homes … we always do not touch 911 (only occasionally is possible or due to missconfig in their network) … if we do it by mistake – we’ll decrypt for free.”
Maze operators also responded, sending Abrams a “press release” stating that “We also stop all activity versus all kinds of medical organizations until the stabilization of the situation with virus.”
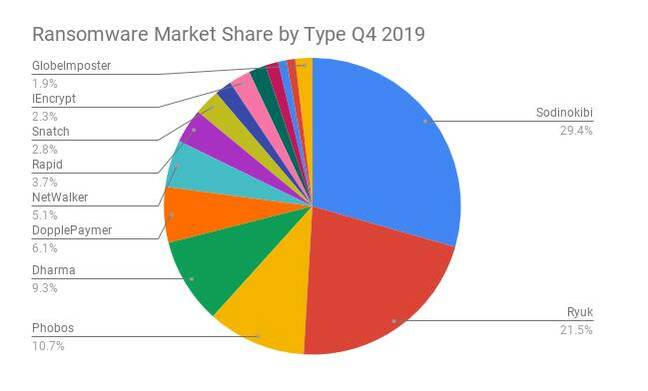
These statements are no cause for celebration. According to security company Coveware, the top ransomware types at the end of 2019 were Sodinokibi, Ryuk, Phobos, Dharma and DopplePaymer. If you suffer a ransomware attack, chances are that it will be the wrong type.
Better news is that Emsisoft and Coveware are offering free help to healthcare providers during the outbreak.
Emsisoft also includes an appeal to the criminals, stating: “We also know you are humans, and that your own family and loved ones may find themselves in need of urgent medical care… Please do not target healthcare providers during the coming months and, if you target one unintentionally, please provide them with the decryption key at no cost as soon as you possibly can. We’re all in this together, right?”
Ransomware is hugely disruptive, in effect closing down access to IT systems and data for those affected. What needs to be done? In its report on ransomware in 2019 in the US, Emsisoft said lax security standards were largely to blame, noting that “[while] 966 government agencies, educational establishments and healthcare providers were impacted by ransomware in 2019, not a single bank disclosed a ransomware incident. This is not because banks are not targeted; it is because they have better security.”
Well, unless they are Travelex, perhaps. Emsisoft added that “unless governments improve their cybersecurity posture, cyberattacks attacks against them will continue to succeed.”
Could organisations easily do more to protect themselves? Microsoft has reported that 1.2 million Office 365 accounts are compromised every months, which could be cut by 99.9 per cent if organisations enforced multi-factor authentication.
Security is hard and can be inconvenient, but getting some basic best practices in place might at least reduce the number of times ransomware slingers rake in the cash and crow over their “success”.®
Sponsored: Webcast: Why you need managed detection and response
READ MORE HERE