Now we know what the P really stands for in PwC: X-rated ads plastered over derelict corner of accountants’ website
A forgotten subdomain on PricewaterhouseCoopers’ dot-com has been hijacked to host ads for porno websites and apps, neatly demonstrating why you should not neglect your corporate DNS records.
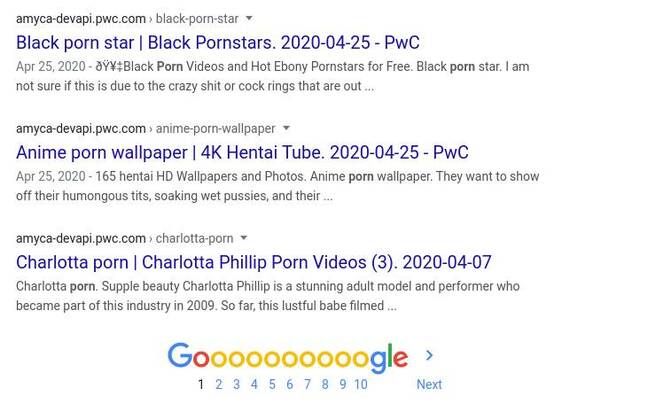
Developer and security researcher Vitali Fedulov told The Register this week he has twice now found the pwc.com subdomain hosting a roster of X-rated adverts to lure netizens to online smut emporiums, X-rated apps, blogs, and adult-only chat rooms. The material also shows up in web searches.
The subdomain, amyca-devapi.pwc.com, has since been taken offline – it no longer resolves to an IP address – though its entries in Google remain for now:
Fedulov, who runs an image search engine, said two times is too many for such a large accountancy firm serving government contracts.
“Since the company provides security services, including for governments, I believe it is time to share the incidents to the public,” he said. “Also, because, from my communication with them, the company seems not interested in supporting the cyber-security community by, for example, offering a bug bounty rewards, the way other large companies do it.”
While PwC declined to comment, both Fedulov and El Reg were able to figure out how the subdomain was commandeered and plastered with filthy ads.
The subdomain, when created by PwC, pointed to amyca-dev-node.azurewebsites.net, a custom Microsoft Azure subdomain created by the bean-counters to host some kind of API development system in the cloud. At some point, the accountancy goliath let its amyca-dev-node subdomain expire or lapse, allowing a miscreant to register it. When people, and search engine bots, visited amyca-devapi.pwc.com, they would be directed to the hacker-controlled amyca-dev-node.azurewebsites.net, which contained anything the miscreant wanted – in this case, a revolving set of risque ads.
In other words, there was no intrusion of the PwC network itself, or any other part of the dot-com site, just some DNS trickery and a forgotten Azure subdomain that someone swooped in and re-registered for themselves.
To verify this, we turned to an infosec bod who previously studied Azure subdomain takeovers, Numan Ozdemir of security firm Vullnerability. Ozdemir took a quick look at the situation, and confirmed that, indeed, the Azure namespace had been hijacked with what he referred to as “hacklinks.”
In this case, Ozdemir explained, the miscreant was likely trying to use the reputation of PwC and its dot-com to game Google into ranking the linked-to smutty pages higher in search results, a particularly underhanded form of SEO.
“The subdomain tells Google, ‘I am the PwC website,’ which has a high domain authority for Google,” Ozdemir told The Register. “So, Google will trust this hacklinked website and let you take a look.”
Ozdemir also noted the miscreants had gone to some lengths to keep the caper under the radar, leaving a “coming soon” page by default on the Azure cloud subdomain, and only placing the naughty ads on separate pages – eg: amyca-dev-node.azurewebsites.net/my-example-awesome-adult-app.html. This allowed the miscreants to keep the naughty pages on the subdomain undetected for two or three months, a period of time needed to build credibility with Google.
“If you add a hacklink and if it just lives for two weeks on the website, Google will rate this as unexpected and it generally hurts your SEO score,” he said.
Ozdemir added this is not a terribly uncommon occurrence. Other large entities, including major universities and government departments have similarly seen their forgotten subdomains and domains taken over and used to serve up pornography or worse.
It is, however, something that will put a dent in a company’s prestige and trust.
Just as the smut-slinging hacker is benefiting from PwC’s domain clout, the company could see its reputation suffer from being associated with these shady pages. The lesson here is: keep good DNS management records, assign people to maintaining them, and don’t lose control of your subdomains. ®
Sponsored: Webcast: Build the next generation of your business in the public cloud
READ MORE HERE