Reworking the Taxonomy for Richer Risk Assessments
By accommodating unique requirements and conditions at different sites, security pros can dig deeper get a clearer sense of organizational risk.
For many years, I have been performing risk assessments of multiple large facilities. These risk assessments have ranged from major power plants to large substations to oil/gas pipelines to oil sands facilities to multistory office buildings. One thing I began to realize over the years is that each risk assessment had its own nuances; however, the approach I took was generally the same.
The assessments are generally conducted following three phases: pre-assessment/planning, on-site risk assessment, and reporting.
Admittedly, this looks rather simple. There are multiple elements in each of these blocks or phases, but generally the approach is the same.
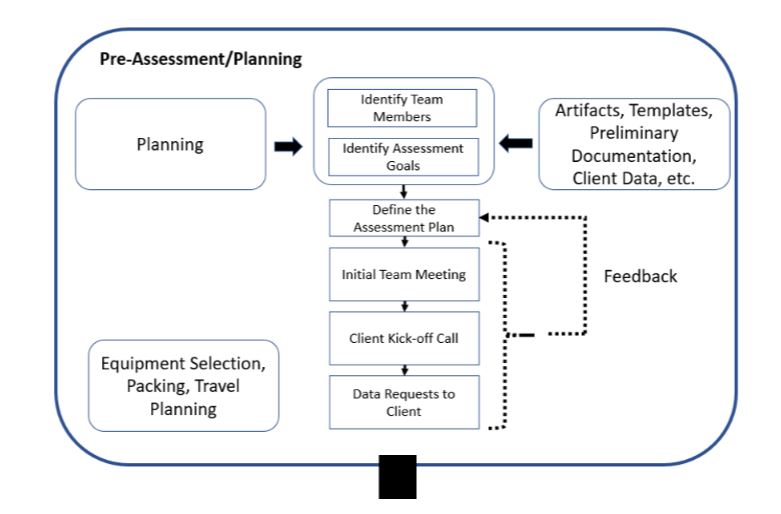
Pre-Assessment/Planning
With pre-assessment and planning, you need to think about the desired outcome (i.e., identify the risks to the facility) and identify the necessary actions to mitigate or eliminate the risks and associated vulnerabilities.
The flow chart above is a detailed view of this phase and includes collecting and digesting documents, identifying the team members and the necessary skill sets, and getting ready for travel. Of course, contacting the “customer” and setting up the necessary on-site logistics are important.
On-site Activities
Now comes the fun part: Getting on-site and looking for threats and vulnerabilities.
Don’t forget these threats and vulnerabilities can be cyber or physical. They can also be part of the site management and culture. What about training or lack thereof? They can all contribute to the risk profile of the facility.
The graphic above offers some elements of the on-site activities. You can see that we have inspections, observations, taking photographs, and looking at the site network and architecture. Even a cyber-vulnerability scan may be part of the site assessment.
These activities are intended to be part of the site assessment plan. However, don’t let the plan place barriers on your site risk reviews. Feel free to follow leads and evidence of problems, since that is why you are on-site rather than doing a remote risk assessment via Zoom.
Reporting
Just like the phrase says, the work isn’t complete until the paperwork is done! In fact, this is very important in order to help your customer — that is the manager of the facility you just inspected — to understand their threat profile, understand what they need to fix, and understand what needs to be mitigated first (that is, categorized risks).
The reporting phase is more than just regurgitating what you found at the site but really understanding the weaknesses identified and identifying how they can become findings, which may include merging some weaknesses. The findings are then built into the report with recommendations for mitigation.
Of note, the report should delineate what each finding is relative to the risks identified. I usually use the following categories: critical, high, medium, low, and observational risks (basically a concern — like housekeeping — that is not in scope for the risk assessment).
Yes, this flow chart does appear elementary — almost too elementary — but it is intended to be the structure to help the risk assessors attack a large facility and determine the threats, vulnerabilities, and ultimate risks. And while not particularly easy, risk assessments are a necessity for our complex facilities and organizations.
Mr. Ernie Hayden, MIPM, CISSP, CEH, GICSP(Gold), PSP — Ernie is a highly experienced and seasoned technical consultant, author, speaker, strategist and thought-leader with extensive experience in the power utility industry, critical infrastructure protection/information … View Full Bio
Recommended Reading:
More Insights
Read More HERE
