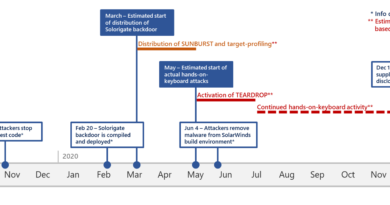
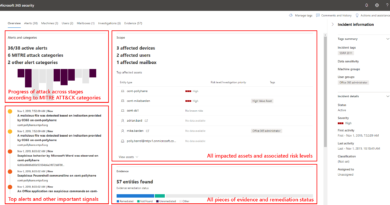
Resources for accelerating your Zero Trust journey
For many organizations, 2020 was the year that finally saw remote work become a reality on a global scale. As many people begin transitioning back to the office, many organizations are thinking about how they can transition from a remote workforce to a more permanent hybrid workplace. We recently conducted a study with over 900 chief information security officers (CISOs) on the state of Zero Trust and found that 81 percent say their organization has started or currently has a hybrid work environment in place and that 91 percent plan for their organization to be fully transitioned to hybrid work within the next five years. The era of hybrid work is here to stay. Learn more about our perspective and security efforts in Vasu Jakkal’s blog, Securing a new world of hybrid work: What to know and what to do, posted earlier this month.
However, as recent events have shown us, the cybersecurity landscape continues to evolve. Bad actors are getting more sophisticated and the need for a stronger security model has never been more important. Zero Trust is no longer an option, it’s now imperative for organizations that want to protect themselves while providing employees the flexibility they need to be productive.
Accelerating your hybrid work readiness with Zero Trust
Implementing a Zero Trust model means transitioning from implicit trust—where everything inside a corporate network is assumed to be safe—to a model that assumes breach and explicitly verifies the security status of identity, endpoint, network, and other resources based on all available signal and data. A contextual, real-time policy helps enforce least-privileged access principles and minimize risks. Zero Trust not only strengthens security but also enables the transformation needed to embrace hybrid work.

I often hear from customers that implementing a Zero Trust security framework can be daunting and that they’re looking for help in creating a roadmap with the right prioritized milestones to maximize investments and positively impact their users. In this post, I’d like to provide an overview of the resources available to help accelerate your Zero Trust readiness and provide actionable guidance.
If you haven’t already, I suggest starting with our Zero Trust Maturity Model whitepaper, which breaks down Zero Trust requirements across identities, endpoints, apps, networks, infrastructure, and data. This paper provides a strong starting point to assess your current Zero Trust maturity, prioritize security efforts to maximize impact, and get a foundational understanding of overall capabilities and requirements.
My colleague, Mark Simos, also posted a blog, Zero Trust Strategy—what good looks like, based on his experience helping customers transform their security strategies that expands on many of the concepts in the maturity model.
Assess your Zero Trust maturity and plan the next steps in your journey with the updated assessment tool
We created the Microsoft Zero Trust Assessment tool to help you determine where you are in your Zero Trust implementation journey and provide to-dos and deployment guidance to help reach key milestones. This month, we released an updated version that provides more targeted guidance and a curated list of resources to help you better prioritize milestones based on your current progress. Now, when a gap is identified in your Zero Trust readiness, you’ll see which specific capabilities you need, the Microsoft products and services that can provide those and step-by-step guidance on implementation.

Get specific suggestions for next steps in your Zero Trust adoption with the assessment tool.
Get up to speed on the essentials of Zero Trust
This month, we’re kicking off our new Microsoft Mechanics video series focused on Zero Trust. In this series, Jeremy Chapman, Director of Microsoft 365, provides a breakdown of how you can adopt a Zero Trust approach across the six layers of defense—identities, endpoints, apps, networks, infrastructure, and data. This series will share tips and provide hands-on demonstrations of the tools for implementing the Zero Trust security model.
Our first two videos are out now:

Watch our new video series, starting with Microsoft Mechanics Zero Trust Essentials.
Other resources
Here are some of the other resources we’ve put together as a result of our efforts helping customers, managing our own Zero Trust deployment, and listening to all of you:
- For an in-depth look at our latest updates that will help accelerate your Zero Trust journey, check out Vasu Jakkal’s blog, How to secure your hybrid work world with a Zero Trust approach, from earlier this month.
- For technical guidance, visit our Zero Trust Resource Center—A repository of information that provides specific guidance on implementing Zero Trust principles across their identities, endpoints, data, applications, networks, and infrastructure.
- If you’d like to learn from our own Zero Trust deployment journey at Microsoft, our CISO Bret Arsenault and team share their stories at Microsoft Digital Inside Track.
- To hear from leaders who sponsored, guided, and oversaw the adoption of Zero Trust within organizations, check out the Zero Trust Business Plan.
- Learn how to get buy-in for Zero Trust in a recent webcast with Microsoft Corporate Vice President, Microsoft Identity, Alex Simons.
- If you’re into podcasts, please check out Episode 3 of the Strengthen and Streamline Your Security podcast to hear discussion on the steps leading organizations are taking and get recommendations to reduce your risk and enable employee productivity.
- Lastly, Examining Zero Trust is an executive roundtable discussion with 10 security leaders sharing their own experiences and real-life examples of adopting the fundamentals of Zero Trust.
Learn more
For more information about Microsoft Zero Trust, please visit our website and keep up-to-date with product announcements, technical guidance, planning resources, and more in our Zero Trust blogs.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
READ MORE HERE