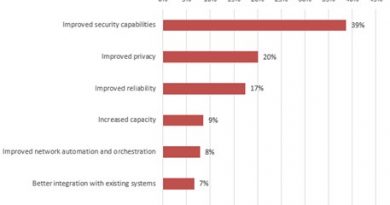
Browser Notification Spam Tricks Clicks for Ad Revenue Threat Researcher

As many countries reintroduced lockdowns and restrictions, more people are once again stuck at home. Not only are people possibly bored at home, but many major sporting events are taking place. This brings fans to streaming sites to watch the games and inadvertently becoming victims of a major click fraud campaign.
As many countries reintroduced lockdowns and restrictions, more people are once again stuck at home. Not only are people possibly bored at home, but many major sporting events are taking place. This brings fans to streaming sites to watch the games and inadvertently becoming victims of a major click fraud campaign.
Web push notifications are a browser feature that allows websites to push notifications to subscribed users. Chrome introduced the browser notification feature in 2015 to allow websites to push notifications for new content or articles to their subscribers. When a user allows browser notifications for a site, it allows the website to push notifications to the browser.
Unscrupulous advertisers are taking advantage of this feature in a unique case of click fraud that might be taking advantage of more people being stuck at home and searching for streaming content. Trend Micro noticed an increase in this type of spam beginning in late February. Upon further investigation, we found something interesting and unique about this browser notification scheme. Instead of leading to anything malicious, the pop-up takes engaged users to legitimate security software websites.
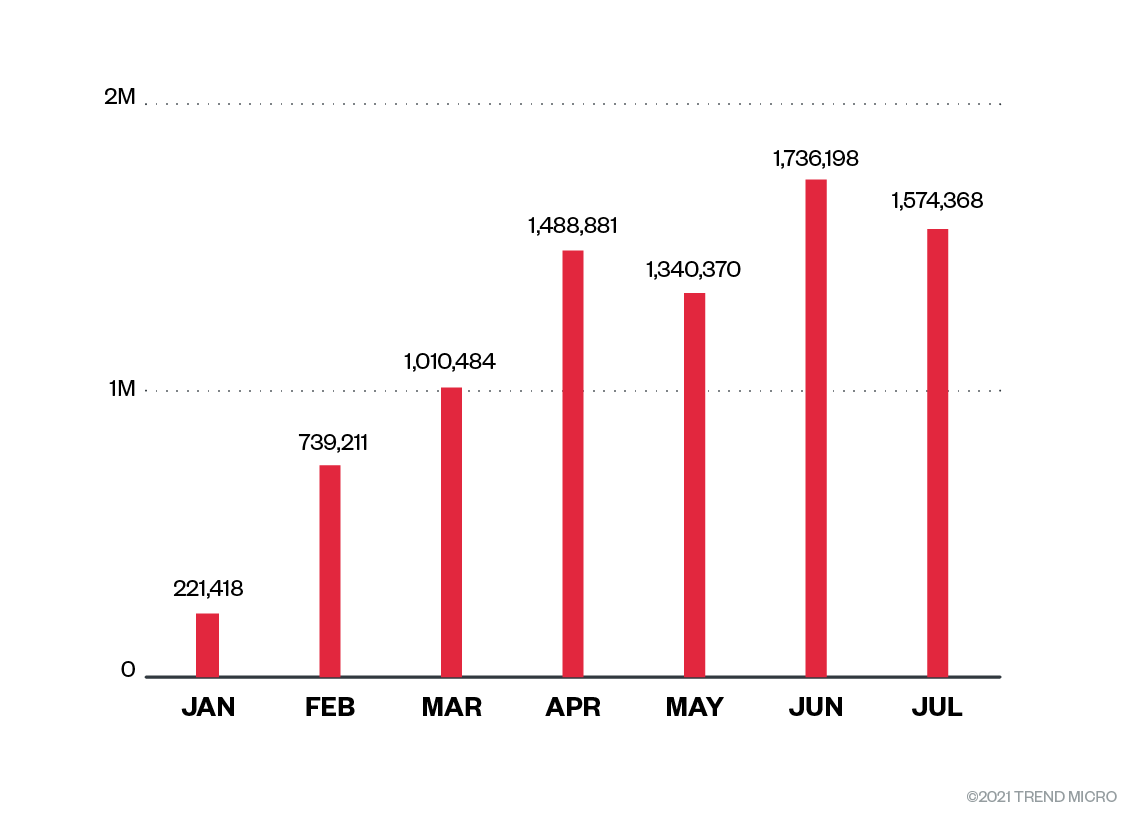
The abuse of the browser notification feature breaches the users’ trust. The spammers are using this feature as a way to generate clicks for ad revenue, and using fear or misleading notifications to convince users to allow notifications.
The doorways to spam
Beginning in March, users started reporting unsolicited pop-up advertisements while browsing the internet using mostly Chrome and Edge browsers. Our initial investigation found that these pop-ups often originated from websites that were built to trick the users into allowing push notifications to the browser.
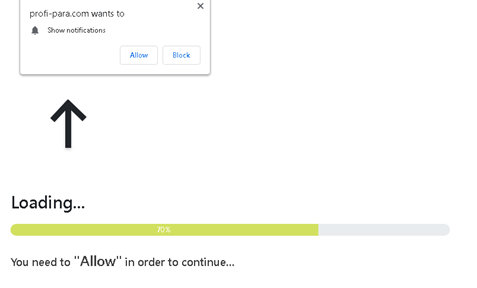
These browser notifications are common when using Chrome and Edge, and some users may default to clicking “Allow” when one of these notifications pop up.
Users are led to the browser notification spam (BNS) sites through a variety of doorway pages, most of which seem to have been created specifically to attract user visits and redirect them to the BNS sites. In total, we identified more than 3,500 domains that redirect to more than 80 BNS sites. Based on IP ranges and registration information, we believe that the same actor or group developed many of the doorway pages for this spam campaign.
Some of the sites used in this attack, which account for a significant portion of the traffic we saw, include:
- allowsuccess.org
- aloha-news.net
- beastbuying.com
- centralheat.net
- news-back.net
- news-central.org
- typiccor.com
The 3,500+ doorway pages target a wide range of user interests. The majority of sites are for adult content, while sports streaming, video streaming, media sharing, and DIY blogs are also quite common. Some doorway pages were even localized; we’ve seen doorways in various languages such as Bahasa, Chinese and Japanese. We’ve even seen doorway pages hosting illegal manga in Japanese, implying the group behind this is not just setting up web pages randomly, but are actually aware of the types of content people in a particular country would be searching for.
The doorway pages not only facilitate this spam, but copyrighted material is also illegally used in the web pages’ content. In Japan, the use of copyrighted manga is strictly enforced.
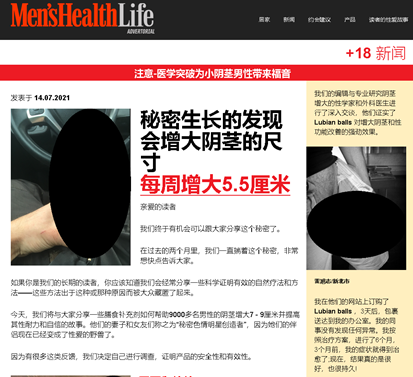
Ads displayed depend on user’s location
The main goal of the group behind this is to redirect user traffic to the final advertisement sites. The text and images of the advertisement is localized based on the user’s IP address. A user browsing from North America would be served a different advertisement compared to a user in Latin America or Asia. Below are three examples of advertisements that were localized for users in Brazil and Japan.

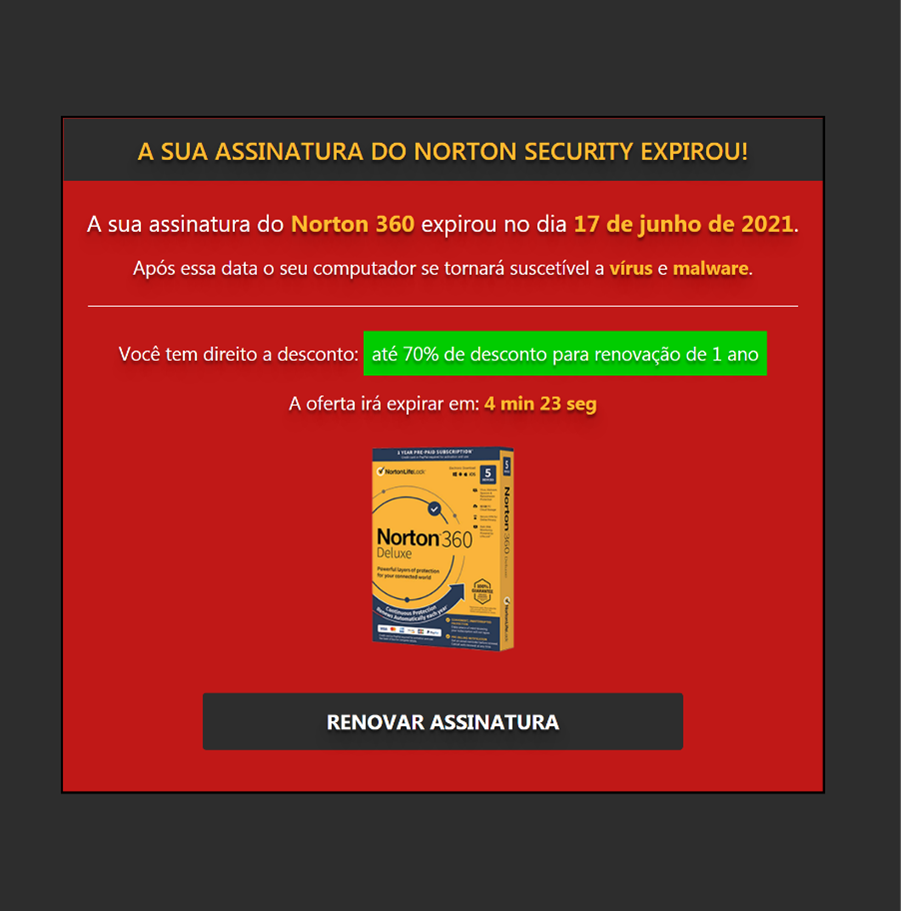
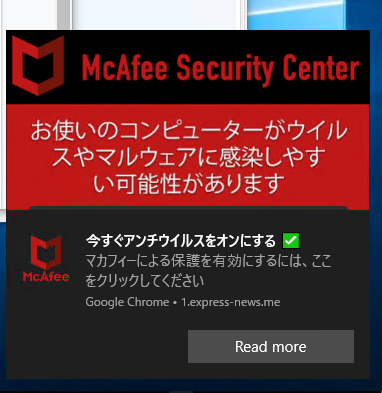
Users who continue from here and click on the renew options on these pop-ups are redirected to the official online shops for McAfee and Norton 360.
It was surprising to us that the pop-up spam would bombard users with ads to purchase legitimate security software. Apparently, this is a very specific kind of scheme in which commissioned affiliates are attempting to earn more from the security companies by tricking more users to visit their websites.
For users in the US, most of the advertisements we’ve seen are for Norton and McAfee, however we were also redirected to an advertisement for the Honey shopping coupon extension.
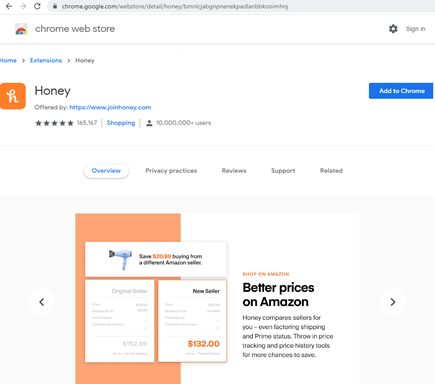
Users outside the US were targeted with more diverse ads. While security software still comprised most of the advertisements, ads for online dating and sexual performance enhancing drugs were also shown.
The infection chain
The following graphic below summarizes this attack’s infection chain:
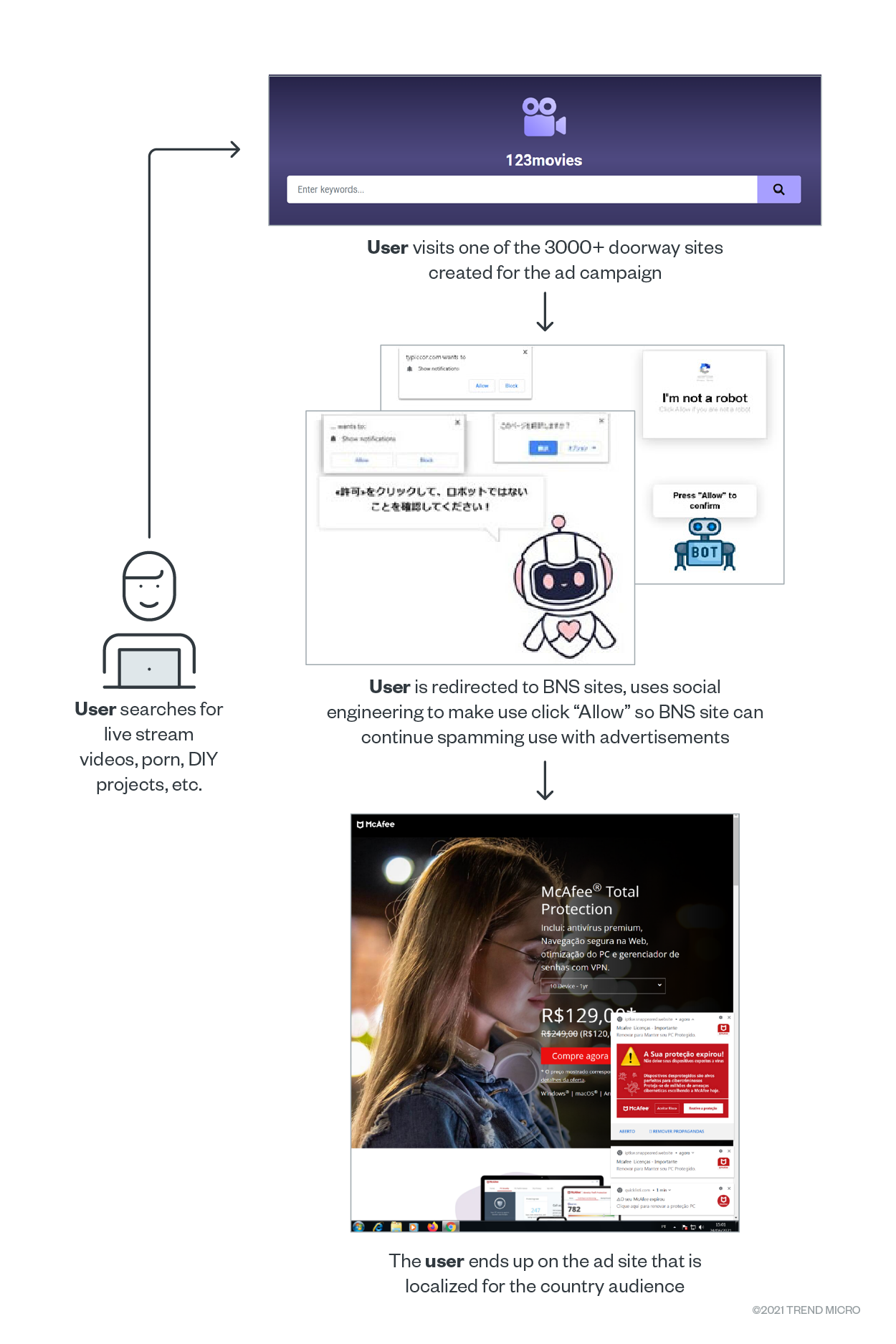
This is the whole redirection chain from the doorway pages, to the BNS sites, and to the final advertisements. It is interesting to note the advertisements also seem to be specifically created for this recent spam campaign, as most of the domains were registered within the last few months.
What users should do
As this spam situation appears to be ongoing, we have notified McAfee and Norton of the potential abuse. Google is also cracking down on the abuse of the browser notification feature, specifically wanting to stop notifications that “mislead users, phish for private information or promote malware.”
It’s quite possible that victims could go through this redirect process without knowing they had been swindled. This is particularly true if the user actually had a McAfee or Norton 360 subscription that had lapsed. Users can avoid this or similar spam attacks by following these recommendations:
- Avoid visiting untrusted websites. Instead, users should find streaming content or topics that match their interests from reputable websites to minimize the risk that they have been compromised for this spam.
- Users should be wary of accepting browser notifications in general. If those are not allowed, this spam and others like it cannot move forward. Google shares a helpful tutorial for disabling these in Chrome.
- Pop-up blockers are a great way to limit this type of browser redirect. Users who do get a pop-up that interests them should go directly to the recommended website rather than clicking on the ad.
Trend Micro’s consumer products can also block traffic to the browser notification sites and prevent these aggressive ads from pestering and tricking users.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE