Auto Apply IPS Rules for Solid Cloud Workload Security Solution Engineer
Workload Security
Learn how to leverage automated and programmable APIs to quickly scan and secure workloads with high or critical severity IPS rules.
You need an intrusion prevention system (IPS) to secure your workloads, but you don’t want to deal with second-guessing vulnerabilities in your system and outdated IPS rules that slow down your workflows. Using an easily manageable solution with IPS rules backed by industry-leading vulnerability research and automated recommendation scans allows you to continue working securely and quickly.
In this article, we will demonstrate how Trend Micro Cloud One™ – Workload Security uses customizable APIs to run automated recommendation scans and only apply high and critical severity IPS rules, ensuring your system is properly configured and elevating your overall security posture.
Demo overview
To follow along, sign up for your free, 30-day trial of Trend Micro Cloud One™ and clone the GitHub repository. The script we are using is easily modifiable, so you can tailor it to your specific use case. The only mandatory variable you need to configure is your API key, you are free to configure the active workloads you want to scan, as well as the total scan time.
Here is a closer look at how we modified our script for this demo:
- Active workloads (lines 165-173): In this demo, we are only scanning endpoint 4105. If you’d like to add multiple endpoints/workloads/servers, paste the script file from the appropriate hostID on line 171, and then uncomment that line.
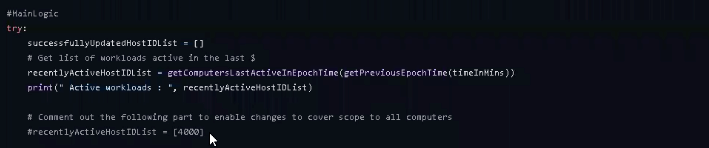
- timeInMins (line 34): You can configure the API to scan any endpoints that have called out to your server within a certain time (for example: 10 minutes) for more efficiency.
- sleepTimeInMins (line 35): Here is where you input the length of the recommendation scan. Depending on the size of your server, you may need to adjust the time to make sure the IPS can complete a thorough scan. There’s no magic number for how long the scan will take—so it we advise starting at 10 minutes, as we did in this demo, and working your way up.

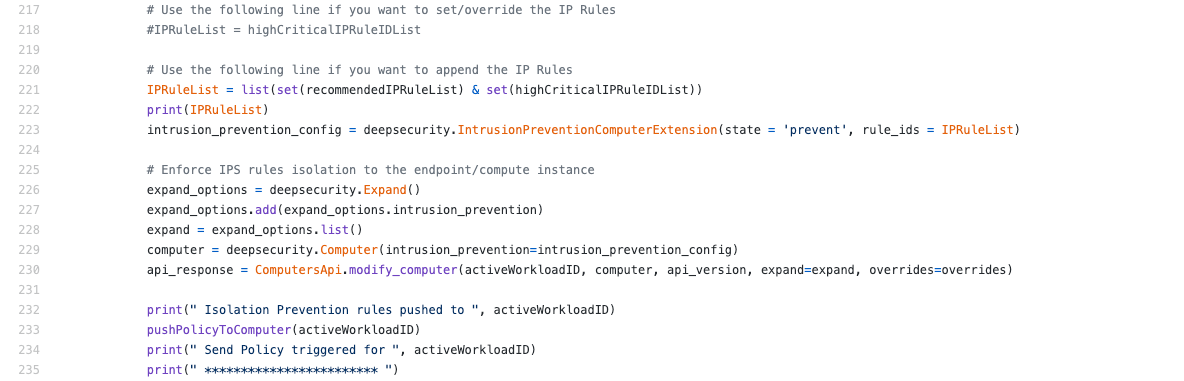
- IPRuleList = highCriticalIPRuleIDList (line 217): This line is critical to our demo as it will override any base IPS policies and apply the IP rule list you want.
- IPRuleList = list (set(recommendedIPRuleList) & set (highCriticalIPRuleIDList)) (line 221): This tells Workload Security which rule list to apply. In this case, we are only applying high and critical severity rules.
- Enforce IPS rule isolation to the endpoint/compute instance (lines 226-235): Here we isolate the application of the IPS rule list to only the endpoint scanned.
Over in the Workload Security console, we have already integrated the test compute instance 3.133.117.141 (am-1) [i-0575fd46c0872f563]. Now that your instance is installed, let’s review its configurations:
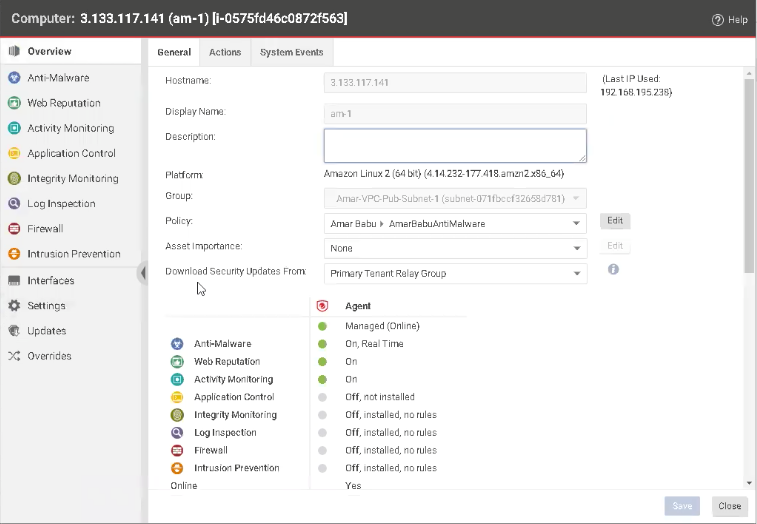
As you can see, Intrusion Prevention is currently off and when you click into it, there are no rules in the Assigned Intrusion Prevention Rules box. In the Recommendations section, dropdown menu beside Automatically implement Intrusion Prevention Recommendations (when possible) is set to Inherited (No). If you didn’t run this script and just selected Yes, it would apply all the IPS rules, regardless of severity, and you will be back at square one trying to prioritize thousands of alerts. The script we’re using is flexible enough that you can modify it to override your base policies and replace the IPS rules or override your base policies and augment your existing IPS rules. In our demo, the script will override and replace the rules.
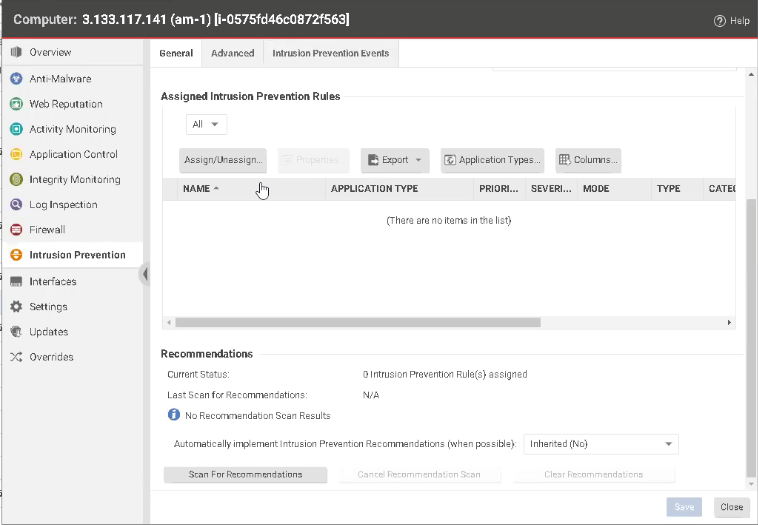
If you click Scan For Recommendations, it will do just that and generate a consolidated log of recommendations and its severity (low to critical), priority level (0 as the lowest, 4 as the highest), and application impacted (browser, mail, etc.) across pre-set endpoints. No more manual hunting, gathering, and prioritizing threat information and alerts.
Demo
Alright, now that we’ve covered the basics of our setup, let’s trigger the recommendation scan.
1. Open your IDE of choice (in this demo we are using Visual Studio Code) and enter the script. You can also run it as a Python script on command line. Modify as you wish for your use case and then run it. When it starts to run, you will see all the active endpoints listed, but the recommendation scan will only push the policy on the specified endpoint.
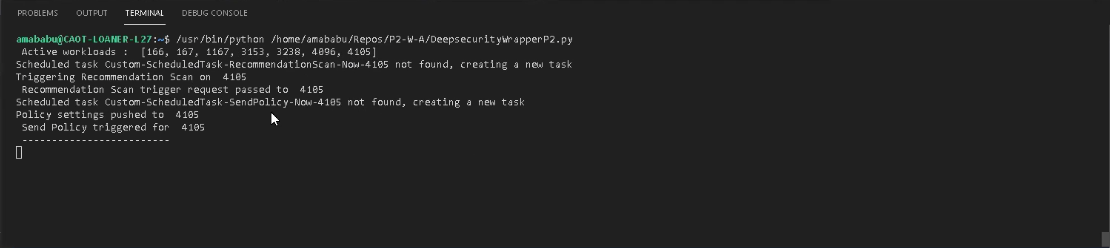
2. After the scan is complete, you will see the total number of high and critical rules found. Don’t panic, this scary number refers to all the rules found and published by vulnerability disclosure programs such as the Trend Micro™ Zero Day Initiative™. Since our script dictated that recommendations will only be applied endpoint 4105, the irrelevant rules are filtered out, and now we are down to 12.
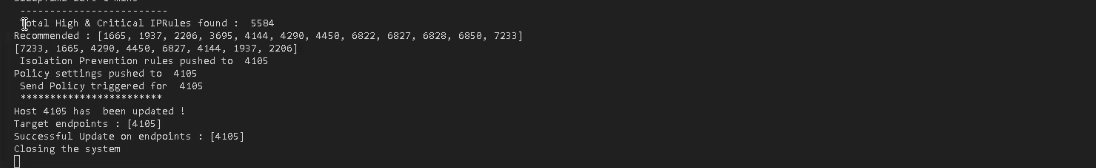
3. That seems more manageable, right? Go to your Workload Security console, select the test instance, and you’ll see that Intrusion Prevention is now says On, Prevent, 8 Rules. Remember that we configured our script to only apply high and critical alerts, therefore, we narrowed the list down even further by eliminating the medium-level recommendations.
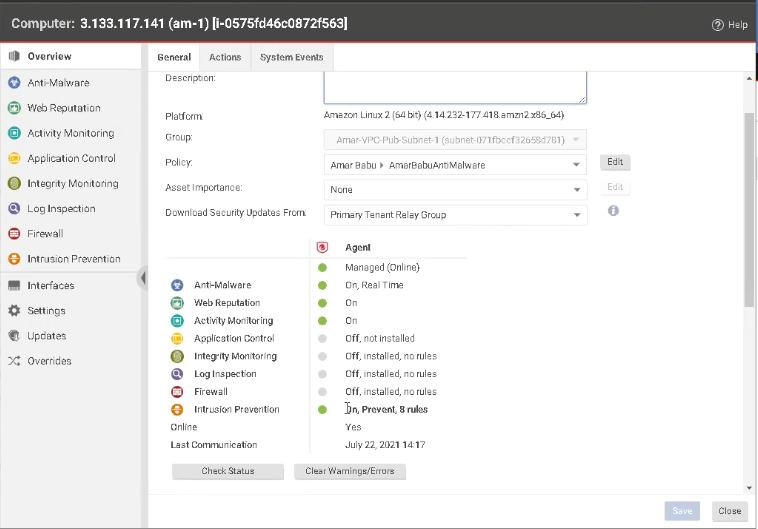
4. Click Intrusion Prevention to view the full list of detected vulnerabilities. Now you have a comprehensive list of detected vulnerabilities that can be sorted by severity and priority level. How easy was that?
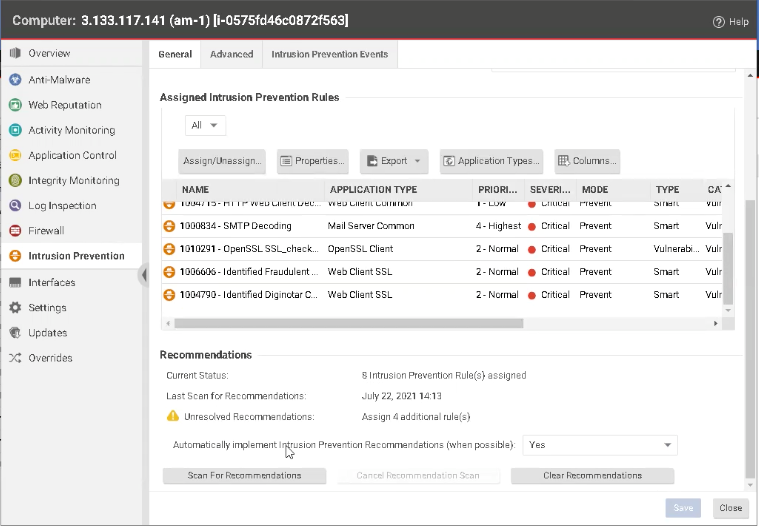
Note that under Recommendations, you will see Unresolved Recommendations: Assign 4 additional rule(s). That doesn’t mean Workload Security missed something—those are the four recommendations that weren’t high or critical severity.
Next steps
Not all IPS are equal. Choose a IPS solution backed by world-leading vulnerability research to ensure that your systems are safe from the latest threats lurking in the wild. Workload Security uses customizable APIs that allow you to automatically scan and apply the most up-to-date IP rules across endpoints of your choosing. It also integrates with your cloud services from AWS, Microsoft Azure, Google Cloud Platform™, and more.
To learn more about the capabilities of Workload Security for DevOps, watch this video. You can also explore more Workload Security use cases by checking out Automate Malware Quarantining for Workloads.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE




