US Treasury Dept. sanctions Russian cryptocurrency exchange for work with ransomware groups
The US Treasury Department announced on Tuesday that it was going after Russia-based cryptocurrency exchange Suex for facilitating ransomware payments in some of the first public, concrete action taken against ransomware groups.
Last week, the Wall Street Journal reported that the Treasury Department was planning some sort of ransomware-related sanctions but US officials explained its plans in detail on Tuesday.
The Department of the Treasury’s Office of Foreign Assets Control’s (OFAC) said Suex was being sanctioned for its role in facilitating “transactions involving illicit proceeds from at least eight ransomware variants.”
Data showed that more than 40% of Suex’s transactions involved “illicit actors” according to the Treasury Department, which added that virtual currency exchanges like Suex are “critical to the profitability of ransomware attacks, which help fund additional cybercriminal activity.”
US officials said it was the first sanctions designation against a virtual currency exchange and was done in coordination with the FBI.
They noted that not all virtual currency exchanges are working with ransomware actors and explained that some are often exploited by malicious actors. But a number of exchanges work directly with ransomware gangs to increase profits.
“As a result of today’s designation, all property and interests in property of the designated target that are subject to US jurisdiction are blocked, and US persons are generally prohibited from engaging in transactions with them. Additionally, any entities 50% or more owned by one or more designated persons are also blocked,” the Treasury Department said of Suex.
“In addition, financial institutions and other persons that engage in certain transactions or activities with the sanctioned entities and individuals may expose themselves to sanctions or be subject to an enforcement action. Today’s action against Suex does not implicate a sanctions nexus to any particular Ransomware-as-a-Service (RaaS) or variant.”
Blockchain analysis company Chainalysis — which assisted in the investigation — said that while Suex is registered in the Czech Republic, it does not have a physical office there and has multiple branches in Moscow and St. Petersburg. There are also Suex branches across Russia and in the Middle East.
The exchange has become popular among cybercriminals because it claims to be able to convert cryptocurrency holdings into cash at branch locations and even facilitate the exchange of cryptocurrency for physical assets like real estate, cars and yachts, according to Chainalysis.
The sanctions are part of a larger effort to disrupt ransomware, which brought in at least $400 million in ransoms in 2020.
Treasury Secretary Janet Yellen highlighted that ransomware groups have not stopped their attacks on businesses, schools and hospitals since the White House ramped up efforts to stop the spate of incidents crippling hundreds of organizations. This week a US agriculture company was knocked out of commission due to a ransomware attack.
“We will continue to crack down on malicious actors,” Yellen said. “As cyber criminals use increasingly sophisticated methods and technology, we are committed to using the full range of measures, to include sanctions and regulatory tools, to disrupt, deter, and prevent ransomware attacks.”
The US is trying to institute an anti-money laundering/countering the financing of terrorism (AML/CFT) framework among virtual currency exchanges and companies as a way to disrupt how ransomware groups manage to get away with their crimes.
OFAC also released an updated advisory discouraging companies from paying ransoms and urging organizations to promote more stringent cybersecurity practices. The advisory implores organizations to contact US government agencies in the event of an attack and work with them “to avail themselves of OFAC’s significant mitigation related to OFAC enforcement matters and receive voluntary self-disclosure credit in the event a sanctions nexus is later determined.”
The government noted that through its Financial Crimes Enforcement Network, it has been collecting information on ransomware payments.
The Treasury Department used the Chainalysis platform and tools from the company to conduct its investigation into Suex.
Gurvais Grigg, global public sector CTO at Chainalysis, told ZDNet the company has a long history of supporting government efforts by providing insight into how cryptocurrencies are used, and in some cases, abused by bad actors.
“With Suex specifically, we have been following them for a while. We first identified them in 2019 as one of a relatively small group of OTC brokers who were helping bad actors cash out a large amount of ill-gotten gains,” Grigg said.
“It’s a common misconception that cryptocurrency is anonymous and untraceable. Chainalysis has a long history of providing technology to government agencies to help them investigate illicit activity using cryptocurrency. Our investigative tools have been used in some of the most high-profile recent cybercrime investigations including ransomware, child sexual abuse, darknet markets, and more.”
Grigg added that the company anticipates further actions as governments and agencies grow their proficiency and access to the data and tools necessary to conduct investigations into cryptocurrency.
When asked whether the company was working with other law enforcement agencies around the world, Grigg said they work “with many partners around the world and our data and services are leveraged in over 60 countries.”
“These partners are actively working similar cases and leverage our data and tools in a similar manner as did Treasury in the actions taken today,” Grigg said.
The company released a blog post explaining some of their role in the investigation, noting that Suex has moved hundreds of millions of dollars worth of cryptocurrency — mostly in Bitcoin, Ether, and Tether — much of which is from illicit and high-risk sources.
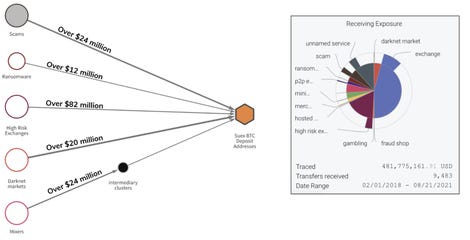
“In Bitcoin alone, Suex’s deposit addresses hosted at large exchanges have received over $160 million from ransomware actors, scammers, and darknet market operators. Chainalysis’ investigation reveals that the OTC is converting cryptocurrency into cash at physical branches located in Moscow and St. Petersburg, and possibly also at other offices outside of Russia as well,” Chainalysis said.
“Suex is also found to have received over $50 million worth of Bitcoin sent from addresses hosted at illicit cryptocurrency exchange BTC-e from 2018 through 2021, well after BTC-e was shut down by U.S. authorities for its own money laundering activity on behalf of cybercriminals.”
Chainalysis said it had been tracking money laundering on Suex for a while, finding that multiple addresses associated with the site are included in the group of 273 service deposit addresses they identified as receiving 55% of all funds sent from illicit addresses in 2020 in their recent Crypto Crime Report. Suex addresses also appeared widely in other lists of addresses connected to money laundering.
The company said due to Suex’s size, shutting it down would “represent a significant blow to many of the biggest cyber threat actors operating today, including leading ransomware attackers, scammers and darknet market operators.”
“Suex operates as a nested service, meaning it operates using addresses hosted by larger exchanges in order to tap into those exchanges’ liquidity and trading pairs. While many nested services are legitimate, some exchanges don’t hold nested services to high enough compliance standards, meaning they can be exploited for money laundering,” Chainalysis found.
“Blockchain analysis reveals that Suex has received tens of millions worth of cryptocurrency payments from addresses associated with several forms of cybercrime, as well as from addresses associated with the now-shuttered exchange BTC-e.”
Chainalysis researchers said there are significant financial ties between SUEX and BTC-e. Despite being shut down in 2017, Suex facilitated transfers on behalf of BTC-e administrators, associates, or former users who were “attempting to liquidate cryptocurrency trapped at the exchange.” Some of the BTC-e transfers took place this year even, despite the platform being shut down years ago.
$481 million in Bitcoin has made its way to Suex since it emerged in February 2018, including almost $13 million from ransomware gangs like Ryuk, Conti, Maze and others. Other cybercriminals, like those involved in Finiko, have also spent millions on the site.
“A small group of illicit services facilitate the majority of cryptocurrency-based money laundering, and Suex is one of the worst offenders, so today’s action represents a positive step forward in the fight against cybercrime,” Chainalysis said.
“We commend OFAC for making this designation and look forward to working with our partners in the public and private sectors to continue the fight against money laundering service providers.”
READ MORE HERE
