Vigilante Hacks Government Linked Cyber Espionage Group
Somewhere, government-linked hackers might be panicking. A digital vigilante has struck back against what researchers believe is a cyberespionage group connected to a nation state. The hacker has allegedly stolen, rather ironically, a cache of data that the government-linked hackers lifted from their own victims across the Middle East.
The news provides a rare instance of someone targeting a so-called advanced persistent threat, or APT, as well as an opportunity for a behind-the-scenes look at a government hacking campaign.
“10 minutes of effort; intel on Iranian APTs,” the anonymous hacker told Motherboard in an online chat, saying which nation they believe may be linked to the hacking group. Some cybersecurity experts tentatively agreed. But Kaspersky, which originally reported on the hacking group it dubbed “ZooPark” earlier this month, told Motherboard it could not currently link the outfit to a known actor.
The stolen data the hacker provided to Motherboard though is noteworthy. It includes text messages, emails, and GPS locations seemingly swept up by ZooPark’s tools; audio recordings apparently captured by the malware of people speaking; and the hacker said they found another related server hosted in Tehran, Iran during their spree.
Got a tip? You can contact this reporter securely on Signal on +44 20 8133 5190, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
The hacker broke into a specific ZooPark server that was listed in Kaspersky’s research—the hacker then pasted their own message on to the ZooPark server, explaining how they allegedly carried out the hack, and pushed a copy to the Internet Archive as proof.
To corroborate the hacker’s claim that the data was taken from a ZooPark server, Motherboard cross-referenced the stolen material with details in Kaspersky’s recent report. Kaspersky’s report said ZooPark had victims in Egypt, Jordan, Morocco, Lebanon, and Iran. Motherboard dug through the GPS coordinates provided by the hacker and found a heavy concentration of infected devices in Egypt and others in Iran. The report added that this was an Android hacking campaign; the data obtained by Motherboard includes sections naming the model of phones, and all appear to be different types of Android devices. Kaspersky’s report said this particular version of ZooPark’s malware was created in 2016; the earliest timestamp of an infected device in the data is from that same year, and stretches up to this month.
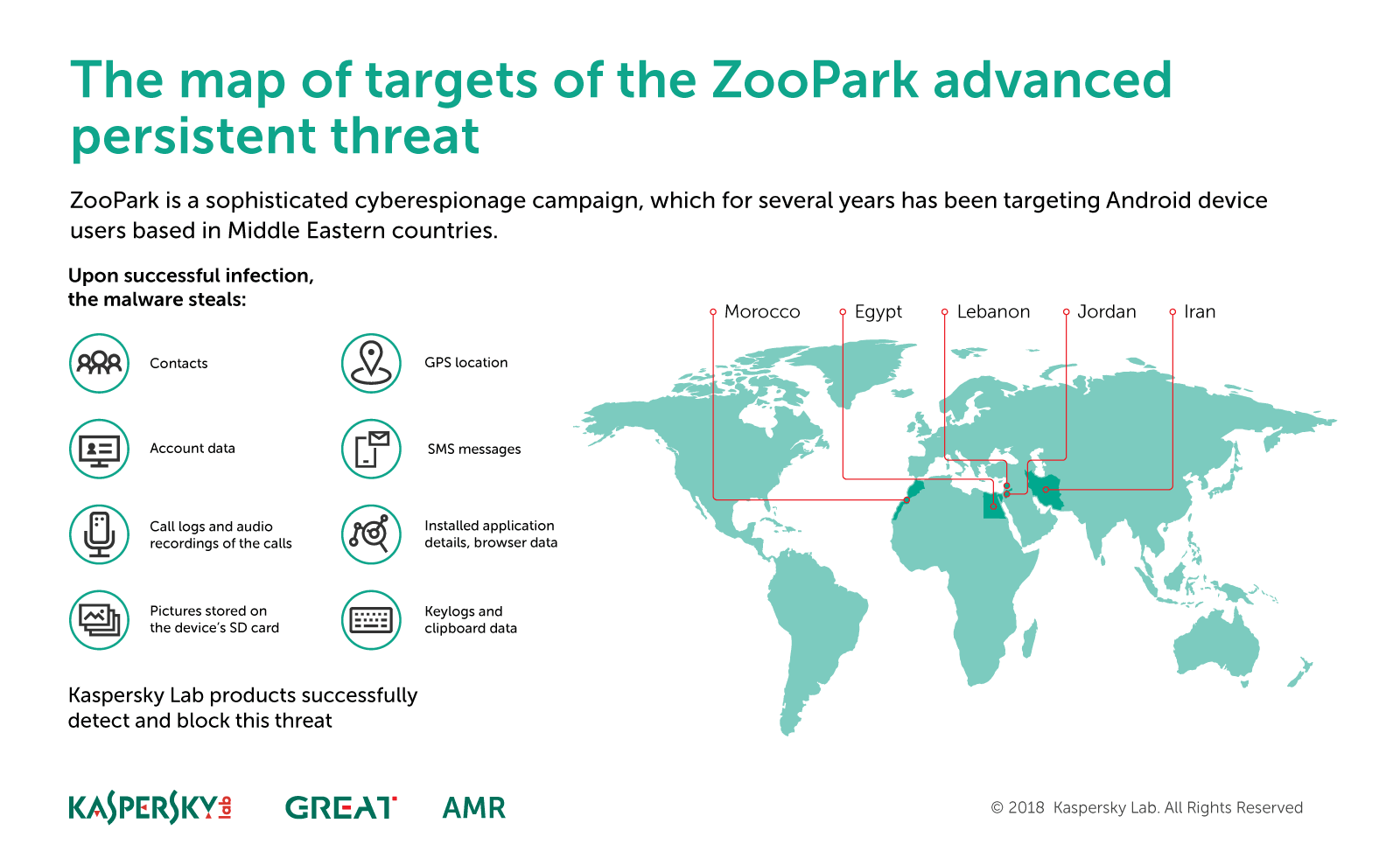
Caption: A Kaspersky infographic on the ZooPark group. Image: Kaspersky Lab.
Kaspersky’s press release said ZooPark potentially targeted members of the United Nations Relief and Works Agency, based on the news topics that the group used to trick victims into installing the malware. And the report adds that one of the group’s pieces of malware was delivered as a fake voting app in the independence referendum in Kurdistan. Notably, one infected device included in the data obtained by Motherboard visited Islamic State-related websites, but the context of why this person browsed those websites is unclear.
Some of the intercepted text messages include verification codes for Instagram and Telegram accounts.
THE BREACH
Kaspersky’s report said ZooPark has used several different pieces of malware over the past few years. The third version of ZooPark’s malware is based on Spymaster Pro, a piece of spyware that the ordinary consumer can purchase, perhaps for spying on their children, employees, or spouses, according to the report. ZooPark’s version of Spymaster Pro lets an attacker record phone calls, monitor a phone’s internet browsing, and steal photos too.
Alexey Firsh, the security expert at Kaspersky Lab who authored the ZooPark report, said this version of the malware was delivered through so-called watering hole attacks; meaning the malware is pushed to a target once they visit a particular malicious website. Firsh said the malware came from alnaharegypt.com and alhayatnews.com, two Arabic language sites, and although he didn’t go into detail, said this particular strain of the malware was used to target “employers of international organizations.”

Caption: A section of the hacker’s message left on the ZooPark server. Image: Screenshot
In February, a hacker targeted Spymaster Pro and provided the stolen data to Motherboard. After seeing the Spymaster Pro connection to the Kaspersky research, that same hacker decided to probe ZooPark’s infrastructure, the hacker told Motherboard in an online chat. The hacker claims they breached a ZooPark server listed in the report by uploading a malicious file, obtaining the server’s administrator credentials, and then moving throughout the system.
“Hacking back should be legalized so Kaspersky could of done this themselves,” the hacker wrote in their message on the ZooPark server.
In its press release, Kaspersky described ZooPark as a “sophisticated cyberespionage campaign.” Although ZooPark did start using more sophisticated malware with its fourth version, the hacker who claims to have breached ZooPark suggests the APT is anything but advanced.
“I don’t think these guys are APTs at all; LamePTs,” the hacker said. “Code reuse kills everyone in the end, if you want to be an APT dont be a fucking skid.”
READ MORE HERE


