93% of Tested Networks Vulnerable to Breach, Pen Testers Find
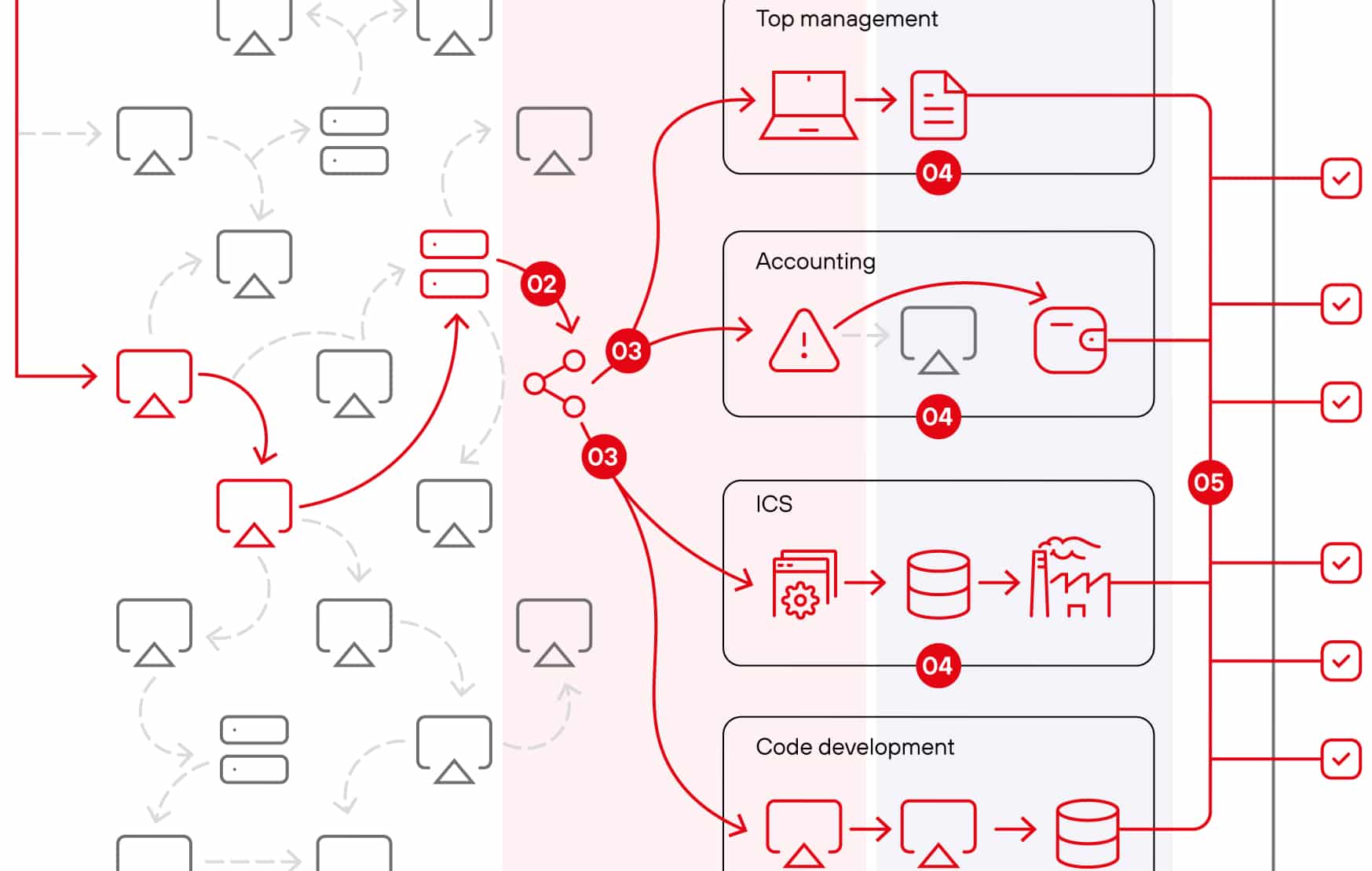
The vast majority of businesses can be compromised within a month by a motivated attacker using common techniques, such as compromising credential, exploiting known vulnerabilities in software and Web applications, or taking advantage of configuration flaws, according to an analysis of security assessments by Positive Technologies.
In 93% of cases, an external attacker could breach a target company’s network and gain access to local devices and systems, the company’s security service professionals found. In 71% of cases, the attacker could affect the businesses in a way deemed “unacceptable.” For example, every bank tested by the security firm could be attacked in a way that disrupted business processes and reduced the quality of their service.
Positive Technologies describes cyberattacks as a series of compromises of key systems that then expose a target system to malicious manipulation. This, in turn, causes one or more “unacceptable events,” which may include disruption of production or services, compromise of executives’ identities, theft of money or sensitive data, and/or the ability to defraud users.
Positive Technologies’ annual report shows that companies need to take stock in 2022 and model likely threats, says Ekaterina Kilyusheva, the company’s head of research and analytics.
“Every company can fall victim to an attack, both targeted and massive,” she says. “According to our data, the number of cyberattacks is increasing from year to year, and their consequences are becoming more serious. Just look at the damage that ransomware operators inflict on organizations.”
The study examines data from security assessments performed from the beginning of July 2020 through the end of June 2021. The company’s penetration testers conducted assessments of dozens of companies and used 45 projects as the basis for the report.
They found compromised credentials were the most reliable way to gain entry into a corporate network, with credential use succeeding in 71% of projects because most employees use overly simple passwords. In 60% of projects, exploiting unpatched software with known vulnerabilities allowed the attacker to further infiltrate a target company’s network. In 54% of cases, misconfiguration of devices and software led to greater compromise.
Finally, in 81% of cases, gaining access to a domain administrator account required an attacker to have only a low level of skills.
“An attacker with credentials and domain administrator privileges could obtain many other credentials to move laterally in the corporate network and gain access to computers and servers,” Positive Technologies states in the report. “Most companies lack network segmentation by business process, which allows several attack vectors to be developed to the point of multiple unacceptable events occurring simultaneously.”
Not all pen-testing data paints such a grim picture. In 2020, assessment firm Lares found — as Positive Technologies did — that easily guessable passwords continued to be a major attack vector, but that enterprises’ security postures had slowly improved over time.
Positive Technologies’ assessments found most industries had significant security weaknesses. Seven out of every eight companies in the industrial and energy sectors were vulnerable to an “unacceptable event” caused by an attacker, the report states. Poor security practices, even on the part of IT professionals, created weaknesses for attackers to exploit. Nine out of 10 engineers, for example, had plaintext documents that described part of the network, along with unencrypted credentials.
Companies should first identify their most critical assets and determine what events and risks might be considered “unacceptable,” says Kilyusheva.
“First of all, it is necessary to draw up a list of events that are inappropriate or undesirable for the business and determine whether an attack by an intruder could lead to their implementation,” she says. “If such events are feasible, then you should determine which target and key systems are involved in the most important business processes and focus efforts on protecting these systems.”
In addition, Positive Technologies recommends that companies partition business processes to keep attackers from easily moving across business units. Organizations are also advised to harden defenses, monitor potential attack vectors, identify attack chains, and modify processes to add steps — such as multifactor authentication — to any avenues of compromise.
“Whether the information security service has time to respond in the event of detecting an attack depends on how far the intruder has to ‘travel,'” the report states. “The shorter the chain, the fewer options the defenders have. To stop an attack in time, before an unacceptable event occurs, it is vital to eliminate the shortest paths from the penetration points to the target system.”
Read More HERE
