Microsoft publishes new report on holistic insider risk management

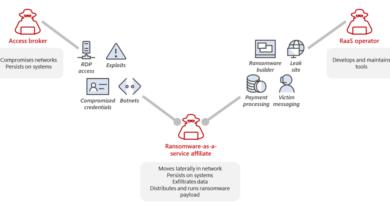
The risk landscape for organizations has changed significantly in the past few years. The amount of data captured, copied, and consumed is expected to grow to more than 180 zettabytes through 2025.1 Traditional ways of identifying and mitigating risks don’t always work. Historically, organizations have focused on external threats; however, risks from within the organization can be just as prevalent and harmful. These internal risks include unprotected and ungoverned data, accidental or intentional data oversharing, as well as the risks for failing to meet ever-changing regulations. Not to mention, with more than 300 million people working remotely, data is being created, accessed, shared, and stored outside of the traditional borders of business.
Core to a security team’s mission is protecting the company’s assets, especially its data. Strong data protection requires securing the most sensitive or critical data, preventing that data from leaving the organization, and managing potential risks inside and outside of your environment.
And managing internal risks can be challenging because it requires analyzing millions of daily signals to detect potentially risky user actions that may lead to a data security incident. For example, what confidential files are your users sharing or accessing? Are users sharing sensitive files externally? Are they downloading files to unapproved devices or uploading them to unapproved locations? All the while, you must balance security controls and productivity, and ensure user privacy is built into your program.
To be effective in addressing insider risks, it’s critical that organizations start thinking about how and why they should be implementing a holistic data protection strategy across their entire organization that encompasses people, processes, training, and tools. At Microsoft, we transitioned from a fragmented insider risk management approach to one in which we addressed it holistically by taking a more comprehensive approach, getting more buy-in from organizational leadership, and making sure user privacy is built in from the get-go.
Following our own transition, Microsoft wanted to better understand how organizations are approaching insider risk management, specifically how some of these security and compliance teams were thinking about insider risk management holistically. Today we’re publishing our first Microsoft report specifically addressing insider risk, “Building a Holistic Insider Risk Management program.”
This Microsoft-commissioned report lays out several new insights about how organizations go from a fragmented approach to insider risk management to a holistic one, addressing potential risks from multiple lenses as part of a greater data protection strategy, with cross-leadership buy-in. For example, we found that more than 90 percent of holistic organizations believe privacy controls should be used in the early stages of investigations. Holistic organizations also get more buy-in on their risk programs from other departments, like legal, HR, or compliance teams, which is critical to building a culture of security. Furthermore, they put a greater emphasis on training with 92 percent agreeing that “training and education are vital to proactively address and reduce insider risks,” compared with 50 percent of fragmented organizations.
The report also shares best practices for organizations who endeavor to approach insider risk management more holistically and build a program that fosters trust, empowers users, and makes privacy a priority.
You can read the full report here.
Learn more
Learn more about Microsoft Purview.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
1Volume of data/information created, captured, copied, and consumed worldwide from 2010 to 2020, with forecasts from 2021 to 2025, Statista. September 8, 2022.
READ MORE HERE