Hardware-assisted encryption of data in use gets confidential
Reader Survey Results Data protection is a top priority for organisations tasked with protecting the integrity of not just their own data, but also the personally identifiable information (PII) they store and process on behalf of their business partners and customers. Not doing it properly risks losing their trust and falling foul of increasingly stringent data protection regulation. So what can be done to toughen up your defences?
We recently polled The Register readership on the subject of Confidential Computing to find out. A sizeable survey base of 177 readers stepped up to the plate, and here’s what they told us.
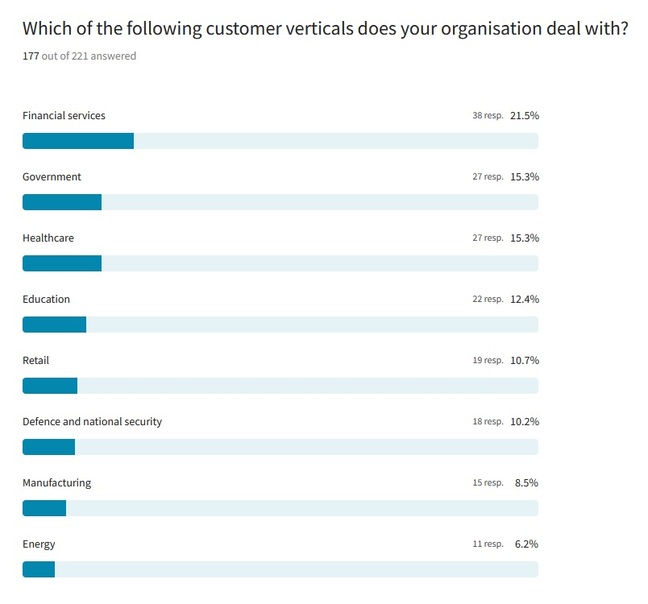
Those who took part indicated that their company deals with customers which hail from multiple different industry verticals, headed by financial services which furnished 21.5 percent of the poll. Equally as many respondents work with government bodies as they do customers in the healthcare sector (15.3 percent), followed by education (12.4 percent) and retail (10.7 percent). More surprising was the 10.2 percent of the poll base that deal with clients in defence and national security (are they even allowed to admit that?), with 8.5 percent hailing from the manufacturing vertical and 6.2 percent from the energy sector.
All of those industries are highly likely to collect, store and process sensitive information from their customers and business partners. We imagine some more than others in the case of those working in financial services, healthcare and defence/national security where rules and regulations tend to be more stringent.
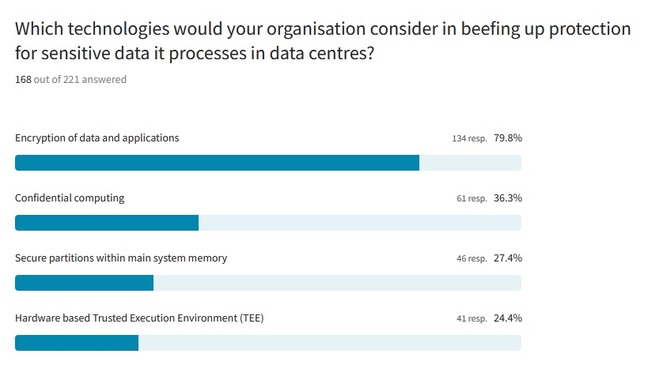
Having established the type of organisations most of you commonly deal with, we asked Which technologies would your organization consider in beefing up protection for sensitive data it processes in data centres? This was a question that allowed multiple responses, reflecting the inevitability that it’s not an either/or approach to cyber security, and could include the simultaneous use of multiple different tools for protecting the information that customers trust to a company for secure hosting and processing.
Encryption of data and applications is by far the single most deployed technology in this respect, deployed by almost 80 percent of the survey base, and 134 of the 177 respondents. That’s to be expected given the long history of encryption and the broad install base of virtual private network (VPN), disk encryption, encrypted email and other device level tools offering embedded symmetric and asymmetric DES, AES and RSA technologies.
What’s perhaps more interesting is that over 36 percent of the 177 people that responded have heard of Confidential Computing and felt that their organization would be interesting in evaluating its suitability to help them secure their data. For those that don’t know Confidential Computing was a term defined by the Linux Foundation’s Confidential Computing Consortium (CCC), a body of hardware vendors, cloud providers and software developers to accelerate the adoption of Trusted Execution Environment (TEE) technologies and standards set up in 2018.
Recognising that data is often encrypted at rest in storage and in transit across the network, the CCC’s focus is on securing data while it’s actually in use, through various technology approaches which involve computation in hardware-based, attested Trusted Execution Environment. That hardware-based TEE is significant because it was another option in our survey, one selected by just over 24 percent of respondents. Almost as many, but not quite, as the 27.4 percent that told us their organisation would consider secure partitions within main system memory as a method of beefing up data protection in their data centres.
What’s clear is that a sizeable chunk of these companies are using more than one technology or approach for pretty much the same end. Which illustrates just how big a deal it is for organisations to protect the sensitive data they store and process in data centres at all stages of its journey.
Sponsored by Intel.
READ MORE HERE