Beware: Lumma Stealer Distributed via Discord CDN

Cyber Threats
This blog discusses how threat actors abuse Discord’s content delivery network (CDN) to host and spread Lumma Stealer, and talks about added capabilities to the information stealing malware.
Our latest investigation revealed that threat actors are now delivering an information-stealing malware called Lumma Stealer via Discord, a popular chat platform for online gamers, content creators, and streamers. We’ve observed that malicious actors are abusing Discord’s content delivery network (CDN) to host and spread Lumma Stealer, while also using the social platform’s application programming interface (API) to create bots that can communicate with the malware and control it remotely. Some of these bots also send stolen data to private Discord servers or channels.
Lumma Stealer, which is written in the C programming language and steals user credentials, is one of the latest malware families to have been distributed by threat actors via Discord’s CDN. This infostealer was first detected in August 2022, and earlier this year, it was reported that Lumma Stealer operators targeted YouTube users via spear-phishing emails.
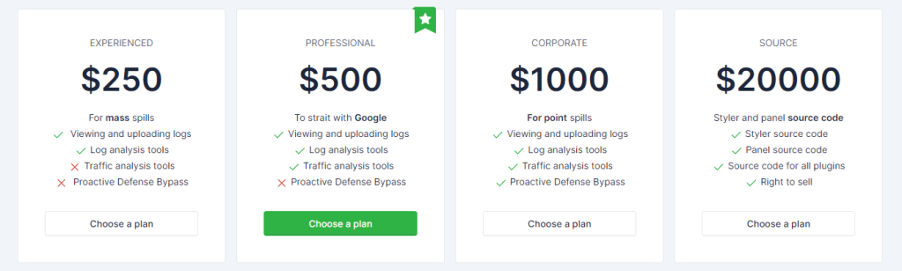
Currently, Lumma Stealer is being sold as a service in underground forums with prices starting at USD$250 per month. The lowest plan allows users to view and upload logs and provides access to log analysis tools, while the professional plan has the same set of features plus access to traffic analysis tools. The corporate plan, which costs four times as much as the cheapest one, includes proactive defense bypass services. Lastly, at US$20,000, the most expensive plan allows users to access the source code and gives them the right to sell the infostealer.
Technical analysis
Lumma Stealer operators typically use random Discord accounts to send direct messages to victims. Malicious actors also use compromised Discord accounts to target the compromised accounts’ connections. The attackers attempt to trick victims by seeking help for a project and offering US$10 or a Discord Nitro boost in exchange for the victims’ assistance. Nitro boosts are part of the platform’s subscription-based Server Boosting that allows users to buy special perks and features for specific servers. These boosts serve as an attractive offer in exchange for the victims’ playing a game and providing a review for it, something that threat actors promise will only take four to five minutes of their time. If a victim agrees to the attacker’s offer, the victim would be prompted to download a file.
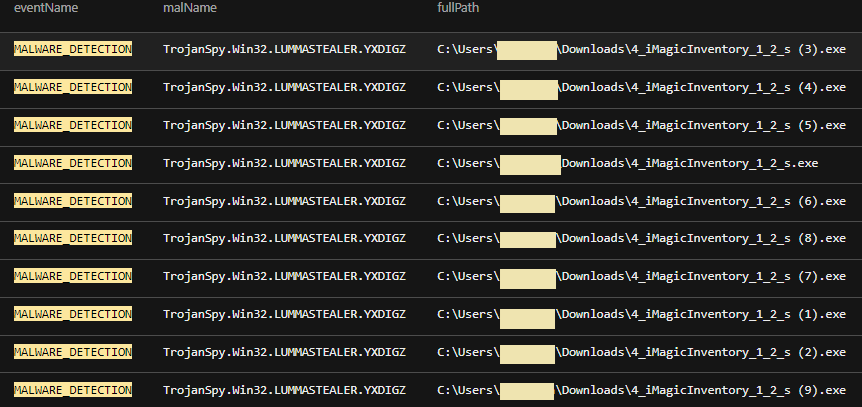
In our investigation, we saw that the victim accessed the fraudulent Discord message via Google Chrome on a work computer. Upon selecting the malicious link, it triggered multiple downloads of the malicious file “4_iMagicInventory_1_2_s.exe” that contains the Lumma Stealer malware.
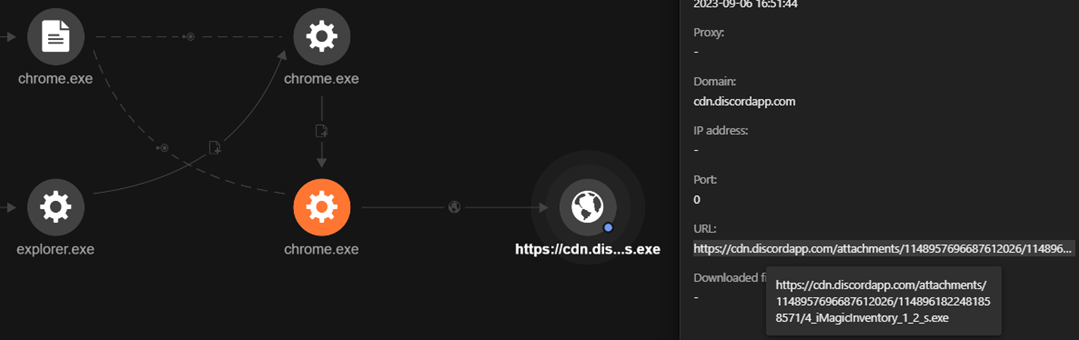
When executed, the file sample connects to a malicious domain, gapi-node[.]io, and tries to steal cryptocurrency wallets and browser data from the user.
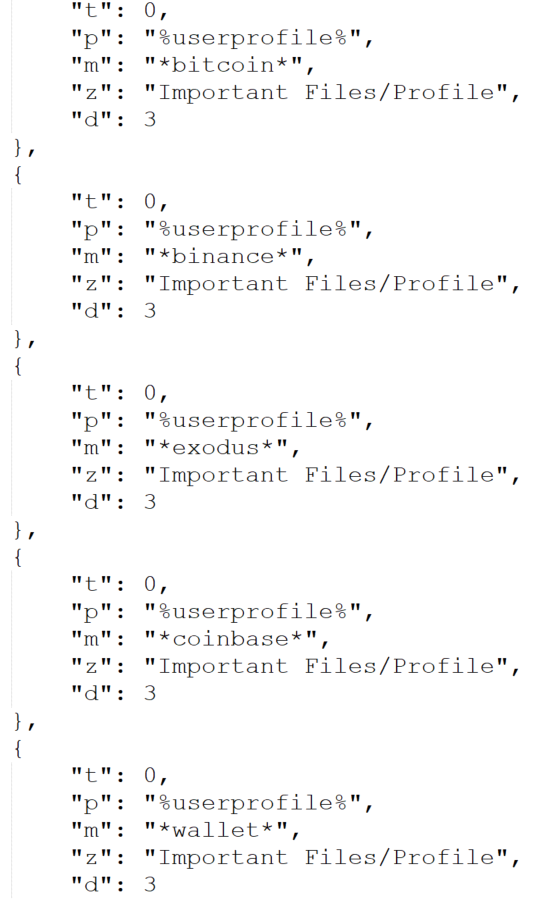
The threat actors behind Lumma Stealer have shared in underground forums that the malware now has the capability to load other files, and based on our observation, these files lead to other malware. Lumma Stealer threat actors also announced that the malware has the ability to detect “bots” using artificial intelligence and deep learning to filter out fruitless infections from their affiliates’ logs. We presume that the term “bots” refers to researchers or analysis environments and emulators.
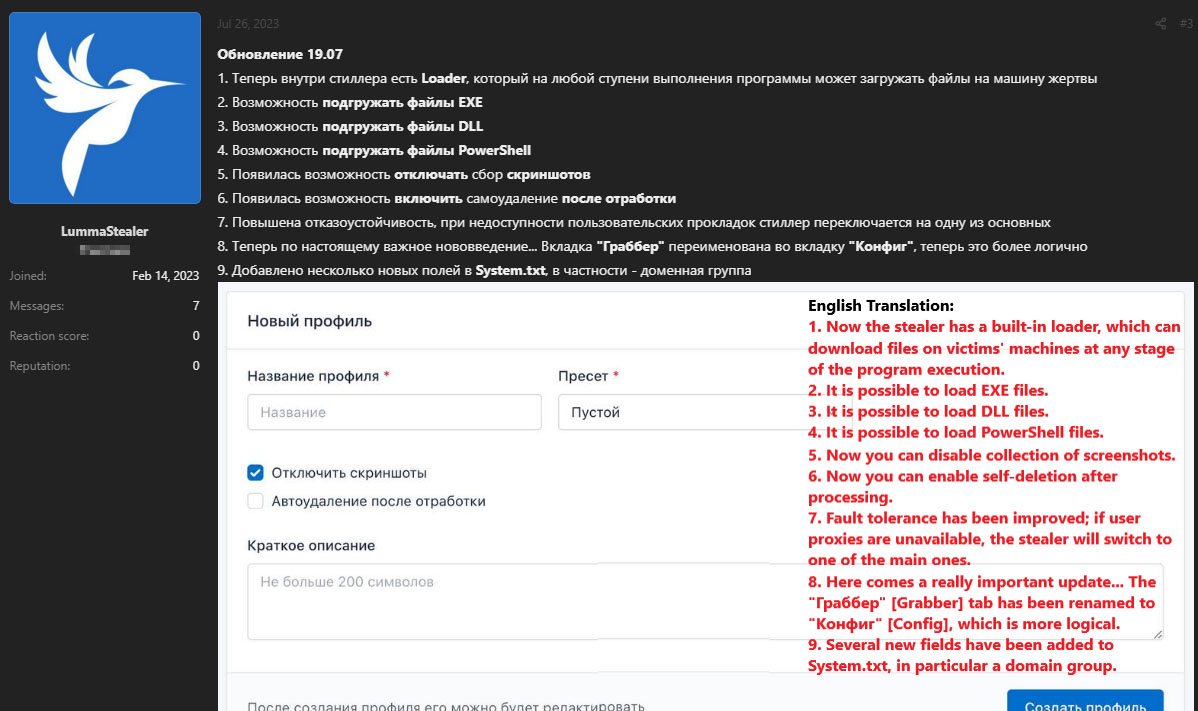
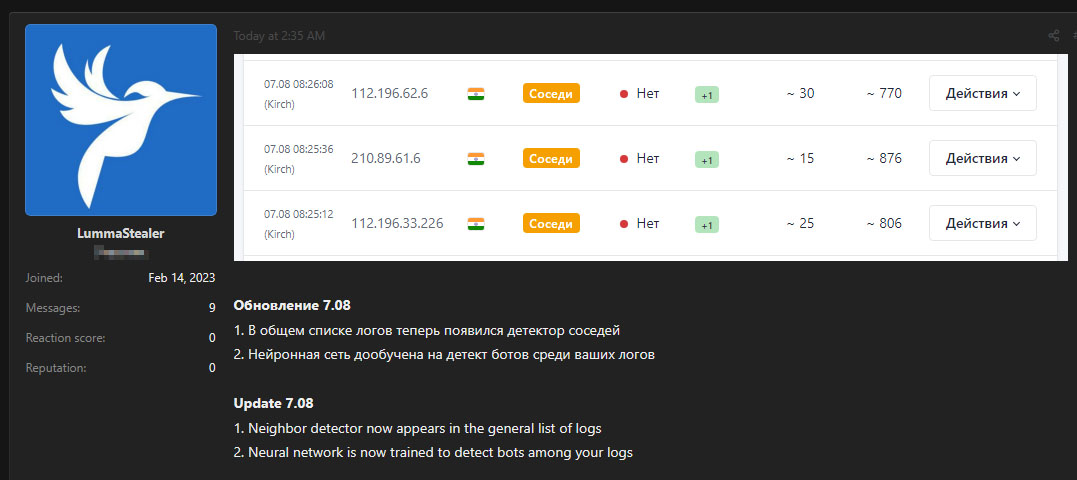
In our investigation, we detected the latest version of Lumma Stealer malware.
Conclusion and recommendations
Users should be careful when selecting links or downloading files from unknown sources, as they could be infected with Lumma Stealer or other malware. Users can also benefit from adhering to the following security recommendations to avoid falling victim to infostealers:
- Users should be cautious of unexpected or unsolicited direct messages. Before opening any attachments or selecting links, users should first verify the sender’s identity.
- Use reliable antivirus software to scan and protect devices from malicious threats.
- Have an inventory of communication tools within your environment and consider adding unsanctioned tools to the Trend Vision One Suspicious Objects List.
- Organizations should ensure that their employees are trained to spot and avoid social engineering scams. Enterprises should conduct regular information security training sessions to help keep everyone informed and up to date.
Trend Micro solutions
Managed XDR uses expert analytics to analyze vast amounts of data collected from various Trend technologies. XDR employs advanced AI and expert security analytics to correlate data from both customer environments and global threat intelligence, resulting in fewer but more accurate alerts and leading to quicker detection. Additionally, Vision One provides a single console that has prioritized alerts and is supported with guided investigation, making it easier for organizations to understand the full scope of an attack and its impact.
With Trend One™, businesses can enhance their resilience with round-the-clock premium support, managed XDR, and incident response services. This service includes automated updates and upgrades for solutions, on-demand training, access to best practice guides, and the ability to consult with cybersecurity experts.
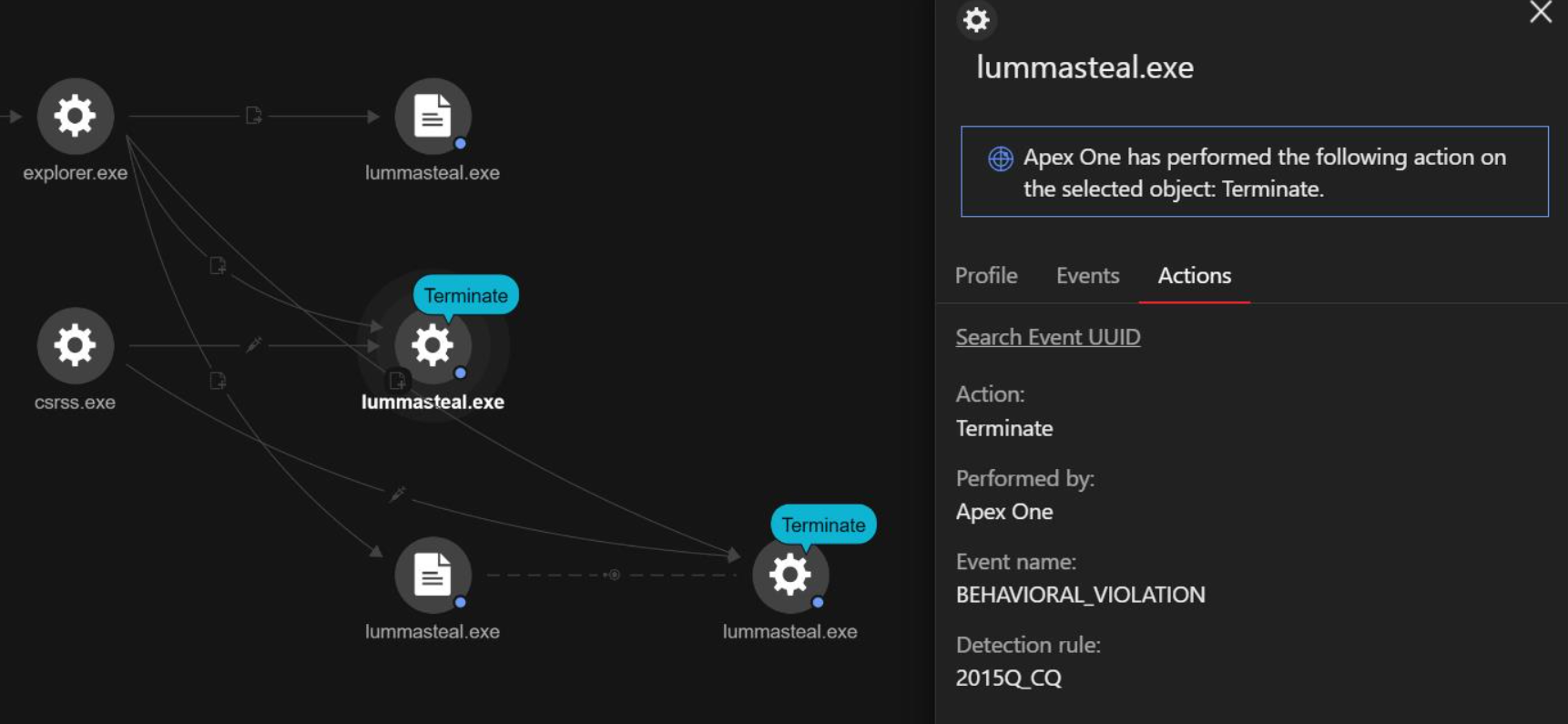
Trend Micro Apex One™ combines threat detection, response, and investigation in one solution. It automatically detects and responds to many types of threats, such as ransomware and fileless attacks. Apex One has advanced tools to detect and respond to attacks and can integrate with security information and event management (SIEM) systems.
Trend Cloud One™ – Endpoint Security and Workload Security protect endpoints, servers, and cloud workloads through unified visibility, management, and role-based access control. These services provide specialized security optimized for your diverse endpoint and cloud environments, which eliminate the cost and complexity of multiple point solutions. Meanwhile, the Trend Cloud One™ – Network Security solution goes beyond traditional intrusion prevention system (IPS) capabilities and includes virtual patching and post-compromise detection and disruption as part of a powerful hybrid cloud security platform.
Indicators of compromise
C&C: gapi-node[.]io
SHA256: 674d96c42621a719007e64e40ad451550da30d42fd508f6104d7cb65f19cba51
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE



