Delivering Proactive Protection Against Critical Threats to NVIDIA-powered AI Systems
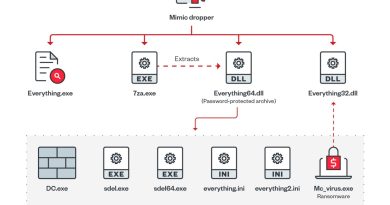
On Wednesday, NVIDIA released updates to fix a critical vulnerability in its NVIDIA Container Toolkit, which, if exploited, could put a wide range of AI infrastructure and underlying data/secrets at risk. With a CVSS v3.1 rating of 9.0, the flaw should be patched immediately. But for organizations unable to do so, Trend Vision One™ will provide proactive protection against attacks attempting to exploit it.
What is the vulnerability?
The NVIDIA Container Toolkit allows users to build and run GPU-accelerated containers, and is the deployment target of choice for many AI systems. CVE-2024-0132 affects all versions of the Toolkit up to v1.16.1. It’s described as a Time-of-Check Time-of-Use (TOCTOU) vulnerability when used with default configuration, which could lead to code execution, denial of service, escalation of privileges, information disclosure, and data tampering. However, it doesn’t impact use cases where Container Device Interface (CDI) specifies the access to underlying devices (such as NVIDIA GPU).
According to the researchers who discovered it, the bug enables a threat actor with control over any container images run by the vulnerable NVIDIA Container Toolkit to perform a container escape, and hijack the underlying host system with full root privileges. In shared environments, with full root privileges, integrity is broken and, as a side effect, confidentiality is too. Basically, any AI application running the affected Toolkit is impacted. Researchers estimate that a third (33%) of cloud environments are affected by CVE-2024-0132.
How does exploitation work?
An attack would look like this:
- An attacker creates a malicious image to exploit CVE-2024-0132.
- They run the image on the victim’s platform, either directly or indirectly (e.g. via supply chain/social engineering attack).
- This enables them to gain access to the host file system.
- With this access, the threat actor can subsequently access the Container Runtime Unix sockets, in order to execute arbitrary commands with root privileges—i.e. assume full remote control.
How can Trend Vision One help?
First and foremost, it is always recommended that users apply vendor-specific patches when they are available. In this case, NVIDIA has released the following patches in response to the vulnerabilities and customers are strongly encouraged to update as soon as possible:
- NVIDIA Container Toolkit 1.16.2 has been released that resolves the issue
- NVIDIA GPU Operator update to version 24.6.2 also resolves issues related to this component
However, for many reasons, rapid patching isn’t always possible. Trend Vision One™ – Container Security customers can use this proactive technology to uncover vulnerabilities, malware, and compliance violations within container images. Scanning for CVE-2024-0132 is available and will also reflect in Trend Vision One™ – Attack Surface Risk Management (ASRM).
An attacker can create a malicious image with the exploit from CVE-2024-0132 Trend can help detect this vulnerability on the pipeline before the image is pushed to production. This way if the vulnerability is detected the Container Security (admission control policy enforcement) can block the container image deployed in the production environment. We also can help detect this vulnerability in runtime, making sure the customer has full visibility of this security issue across the entire environment.
Read More HERE