Twitter Urges Users to Change Passwords Due to Glitch
Twitter said Thursday that a glitch caused account passwords to be stored in plain text on an internal log, sending users across the platform scrambling to change their passwords.
The social media company said that it found and has fixed the glitch, and its investigation shows no indication of a breach or misuse by anyone. While the company did not specify how many passwords were impacted, a Reuters report said its entire user base of 330 million are impacted.
“I’d emphasize that this is not a leak and our investigation has shown no signs of misuse,” a Twitter spokesperson told Threatpost. “We’re sharing this information so everyone can make an informed decision on the security of their account.”
The spokesperson declined to comment on the timeframe of the glitch and how many users were impacted.
“Due to a bug, passwords were written to an internal log before completing the hashing process,” said Parag Agrawal, CTO of Twitter, in a blog post. “We found this error ourselves, removed the passwords, and are implementing plans to prevent this bug from happening again.”
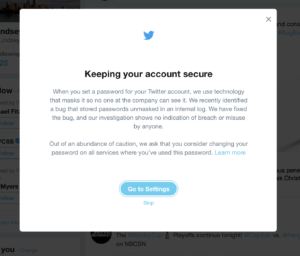
Users who opened their accounts Thursday evening received a prompt from Twitter asking them to consider changing their password on all services where they used the password.
Twitter said that it masks passwords through hashing using bcrypt, which replaces the actual password with a random set of numbers and letters stored in its system. However, the glitch caused passwords to be written into the company’s internal computer system before the hashing process was completed.
Agrawal said in a tweet that Twitter is sharing the information about the glitch to help users “make an informed decision about their account security.”
We are sharing this information to help people make an informed decision about their account security. We didn’t have to, but believe it’s the right thing to do. https://t.co/yVKOqnlITA
— Parag Agrawal (@paraga) May 3, 2018
Security researcher Troy Hunt told Threatpost that the real world risk of the glitch to users is likely very low: “I can see how it would happen – logs are often largely automated – but clearly it’s a massive oversight,” he said. “By the same token, if the extent of the issue is that the passwords were captured to internal logs, the logs weren’t exposed and they’ve subsequently cleaned that up, the real world risk is likely very low.”
The news parallels another incident earlier this week, where Github also disclosed that it had discovered a recently introduced bug exposing a small number of users’ passwords in plain text. GitHub also uses bcrypt to hash passwords.
Twitter found itself in hot water earlier in the week after disclosing that it sold data access to a Cambridge Analytica-linked researcher. This expounded on already tightening concerns by the security community about how social media companies protect private user data.
Read More HERE