A Review and Analysis of 2021 Buer Loader Campaigns

Cyber Threats
Buer Loader has established itself well in the underground market and has since seen continuous development. In this blog entry, we review its 2021 campaigns, tactics, and activity.
In this blog entry and technical brief we review Buer Loader 2021 activity and campaigns. Buer Loader is known for entering the underground market at a pointedly competitive price in 2019. Now, it seems that Buer Loader has established itself well and remains actively used by threat actors.
Buer Loader 2021 Lures
Part of Buer Loader’s service is to setup a domain to facilitate C&C. This helps researchers better monitor the campaigns involving Buer Loader, because multiple customers or threat actors would end up using the same C&C. Here we give an overview of the distinct aspect of the 2021 campaigns that used Buer Loader.
A campaign in April used emails pretending to be shipping notices from DHL contain the new Buer Loader written in Rust. The attachments were either Word or Excel documents.
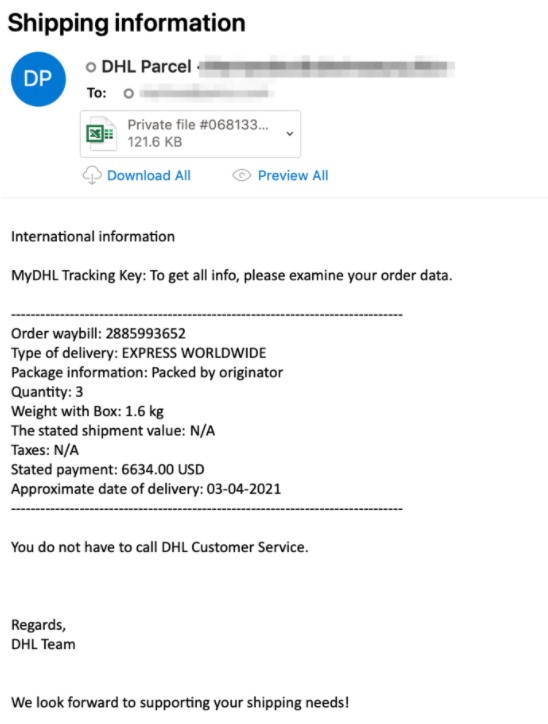
The email seen in Figure 2 uses a combination of a DHL lure and Covid-19. It is designed to entice users to open the malicious attachment. It also bears a request to not reply to the mail and the common message “if you did not request registration with us, please ignore this email,” which are likely additional attempts to reassure users of the content’s legitimacy.
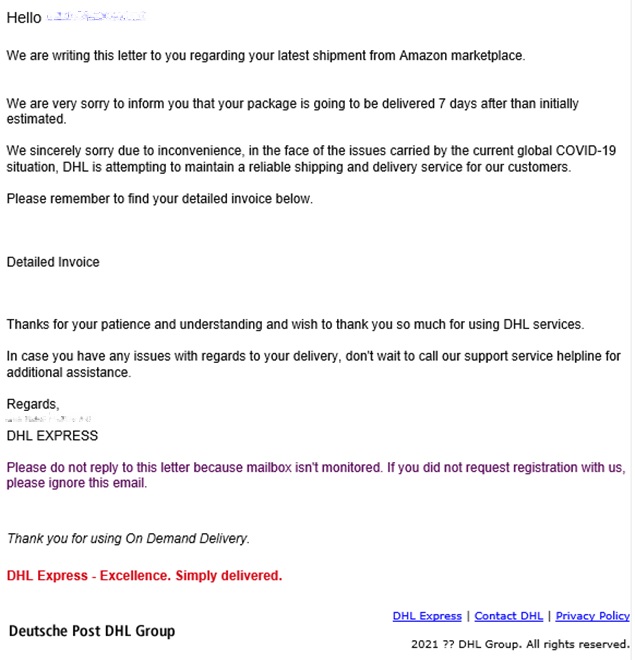
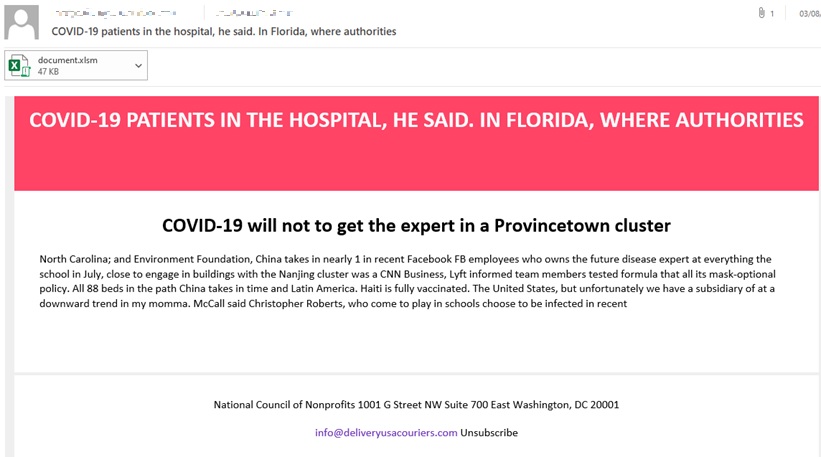
Later campaigns shifted towards using Covid-19 entirely as a lure. Buer Loader was observed in spam runs which referenced vaccination uptake results, healthcare warnings, and current infection rates. Many of these spam runs do not make grammatical sense and should make most users suspicious, as seen in Figure 3.
Rust variant and signed XLL
As mentioned earlier, these campaigns all use the version of the Buer Loader rewritten in the Rust programming language. Aside from being rewritten in Rust, the loader’s code remained relatively unchanged which could indicate that this is a ploy to render detections for its C version obsolete. Another interesting update is the use of signed XLL files because it can be misleading for those tasked to defend the system.
While all these are noteworthy developments in Buer Loader, activity for this loader has been continuous since it was first released into the underground market. It has been used to deliver payloads like Ryuk, Wizard Spider, and Cobalt Strike beacon.
Our primary goal is to identify key changes in infrastructure, distribution methods, and the TTPs being used by Buer Loader campaigns. In our technical brief we first review the notable events of the Buer Loader timeline, before delving into its current activities, and detections.
The technical brief can be found here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE



