Are You Planning for the Quantum, Transhumanist Threat?
Companies should start preparing — or at least planning — for likely threats of the future, including quantum computers that can decrypt current encryption in less than a day and humans who hack using implanted devices, said speakers at the SecTor security conference.
Nations and large companies, alike, are investing billions of dollars in quantum computing. While the technology promises to allow uncrackable communications, it also poses a likely threat to current digital infrastructure based on the latest encryption. Symmetric-key encryption, for example, could be cracked more easily using quantum computing, but it can be scaled up to larger key sizes to foil efforts. Public-key encryption, however, will almost certainly be broken by quantum computers in the future.
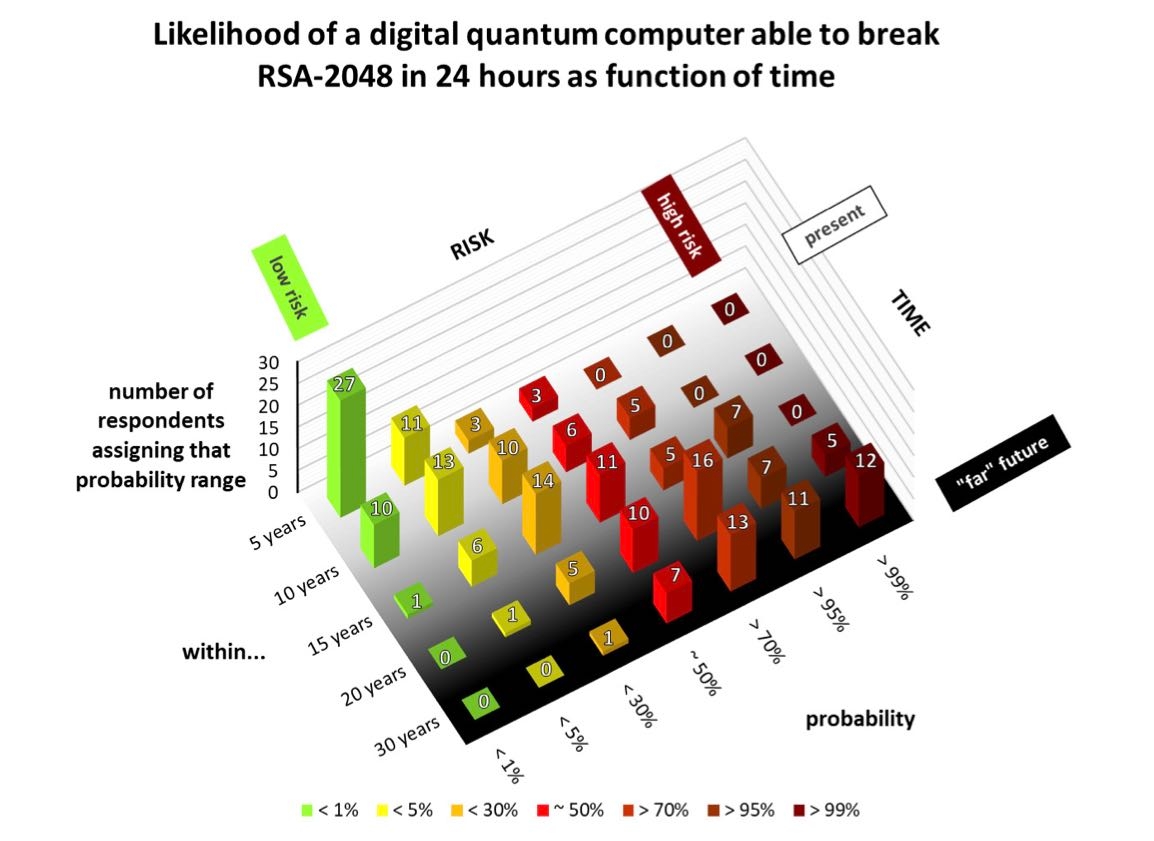
Such attacks will not be seen for at least five years and likely not a decade either, but they could pose a threat in 20 or 30 years, said Michele Mosca, CEO of evolutionQ, at last week’s SecTor. About 83% of quantum-computing experts currently experimenting with the technology believe that breaking RSA-2048 encryption in less than 24 hours is a challenge that will not be solved in a decade, but the same percentage believe the milestone will be reached in less than 30 years, Mosca said.
“The quantum computing train is on the tracks and accelerating, and we need to be ready for it from a cryptographic perspective,” he said, urging companies to create a plan to secure their infrastructure. “If you are only a year along a 10-year road map, you don’t get to call a timeout to make up for that lost time.”
Other threats will likely arrive even sooner — and, in some ways, are already here. The biohacking, or transhumanist, movement aims to improve the human body using various technologies, from supplementation to genetic tinkering and from the use of external devices to implantation. The last approach — augmenting the human body with devices — is already being used for hacking.
Len Noe, a white-hat hacker for Cyberark and biohacker, has turned himself — as he likes to say — into the attack vector. Noe told SecTor attendees that he has already implanted the NExT chip, a rod-like receiver for near-field communication (NFC) and radio-frequency identification (RFID) signals, as well as its big brother, the 41-mm disk-shaped flexNExT, which performs at longer ranges. An implanted flexEM device, which allows the emulation and cloning of various RF protocols, and the Vivokey Spark 2 “cryptobionic” implant, for strong cryptography, are some of the other devices Noe has had implanted in his hands.
The devices can be used for hacking access entry systems, cloning access cards, and other attacks, he said. Businesses and employees will have to be wary of such devices in the future and should start adding such technology to their threat models.
“Security admins know the normal attack vectors, but how do you address the fact that one of your employees could have a full Linux system underneath their skin?” he says. “With the number of regulations and audits that companies are required to do for compliance, how would you know whether someone has bypassed your security policy and brought a rogue asset into your environment? The short answer is, you wouldn’t.”
The two presentations at SecTor demonstrated potential threats that most companies don’t have to worry about today. However, they both pose significant threats for the future, so companies should start incorporating the possibility of attacks on encryption or through hidden devices as part of their threat model.
The threat of biohackers likely has the most straightforward trajectory, with more powerful devices almost certainly to be implanted in human bodies. Some biohackers have already attempted to implant a single-board computer into their bodies, with less-than-perfect results.
“This is on the outer edge of extreme, even for most biohackers,” Noe said. “This is not a simple process, and making sure that the single board computer is completely sealed has caused a number of individuals that have attempted this implant to require emergency removal surgery.”
Forward-looking security professionals should assume that individuals will successfully augment themselves with more technology that could be used for hacking.
The impact of quantum computing, however, has a much less well-defined trajectory but will likely have a more far-reaching impact. While the industry needs 100,000 times more processing power and 100 times better error correction, the eventual impact of the universal capability to break currently encrypted data could cause immense harm, according to scientists.
Just as damaging, however, is unprepared businesses rushing to deploy technology, said evolutionQ’s Mosca.
“We focus on the possibility that people will use quantum computers to steal information and hijack systems and so on,” he said. “That is a real threat and we want to avoid it, but if we avoid it in a sloppy, messy way, that is just as bad. When you deploy software in systems without enough quality assurance, systems crash.”
Most major countries have efforts underway to create plans for a post-quantum future. The National Institute of Standards and Technology, for example, is analyzing proposed safe encryption methods and will release recommendations for a quantum-resistant encryption algorithm. Companies that want to get a head start on planning can participate in the Open Quantum Safe project or other similar efforts.
Read More HERE
