Attackers Route Malware Activity Over Popular CDNs
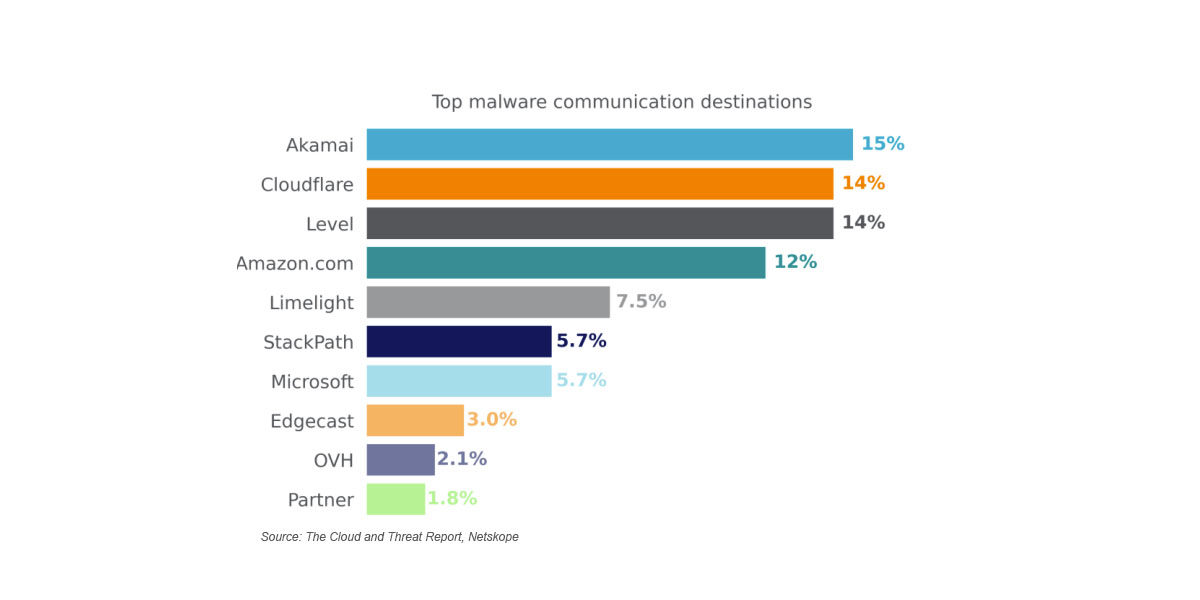
Attackers are abusing widely used cloud services and applications to deliver malware and hiding the malware’s post-infection activities by routing them over common network ports and well-recognizing content delivery networks (CDNs) and cloud providers, Netskope said in its latest “Cloud and Threat Report.” The report provides intelligence on active malware threats against enterprise users. On average, five out of every 1,000 enterprise users attempted to download malware in the first quarter of 2023, it states.
After the malware infects a victim machine, it establishes a communication channel with its home server to download additional malware payloads, execute commands, and exfiltrate data. Attackers are increasingly routing malware communications through IP addresses belonging to well-known CDNs and cloud service providers, primarily Akamai and Cloudflare. Amazon Web Services, Microsoft Azure, and Limelight are also commonly abused.
Only a small fraction of total Web malware downloads were delivered over methods recognized as risky, such as newly registered domains and uncategorized sites, the report points out.
In the first quarter, 72% of all malware downloads detected by Netskope were new, the company reports. Attackers delivered malware by abusing widely used services and applications, such as OneDrive, SharePoint, Amazon S3 buckets, GitHub, Weebly, Dropbox, Google Drive, Box, Google’s Gmail service, and Azure Blob Storage. According to Netskope, attackers had used 261 distinct apps in the first quarter for malware downloads.
“Cloud apps are also commonly abused as a form of social engineering, where attackers use app features familiar to the victims to entice them into downloading malware,” Netskope’s team states.
Read More HERE
