Automate Malware Quarantining for Workloads Solution Engineer

Workload Security
Leverage automated and programmable APIs to quickly secure and quarantine workloads without interrupting downstream workflows.
Manually tracking and investigating workloads for malware is nearly impossible given the speed of building in the cloud. Automated security policies that detect and protect new workloads as quickly as you create them is essential to staying on track.
In this article, we will demonstrate how Trend Micro Cloud One™ – Workload Security uses APIs to automatically isolate a workload and quarantine it with a firewall module when a threat is detected.
Architecture and configurations overview To follow along, sign up for your free, 30-day trial of Trend Micro Cloud One™ and clone the GitHub repository. We will be using EICAR, a well-known benign malware that evokes a similar response to other “real” malwares. We will also be using four AWS services: Simple Notification System (SNS), Elastic Computing (EC2), Secrets Manager, and Lambda. Below is an overview of the use case solution architecture:
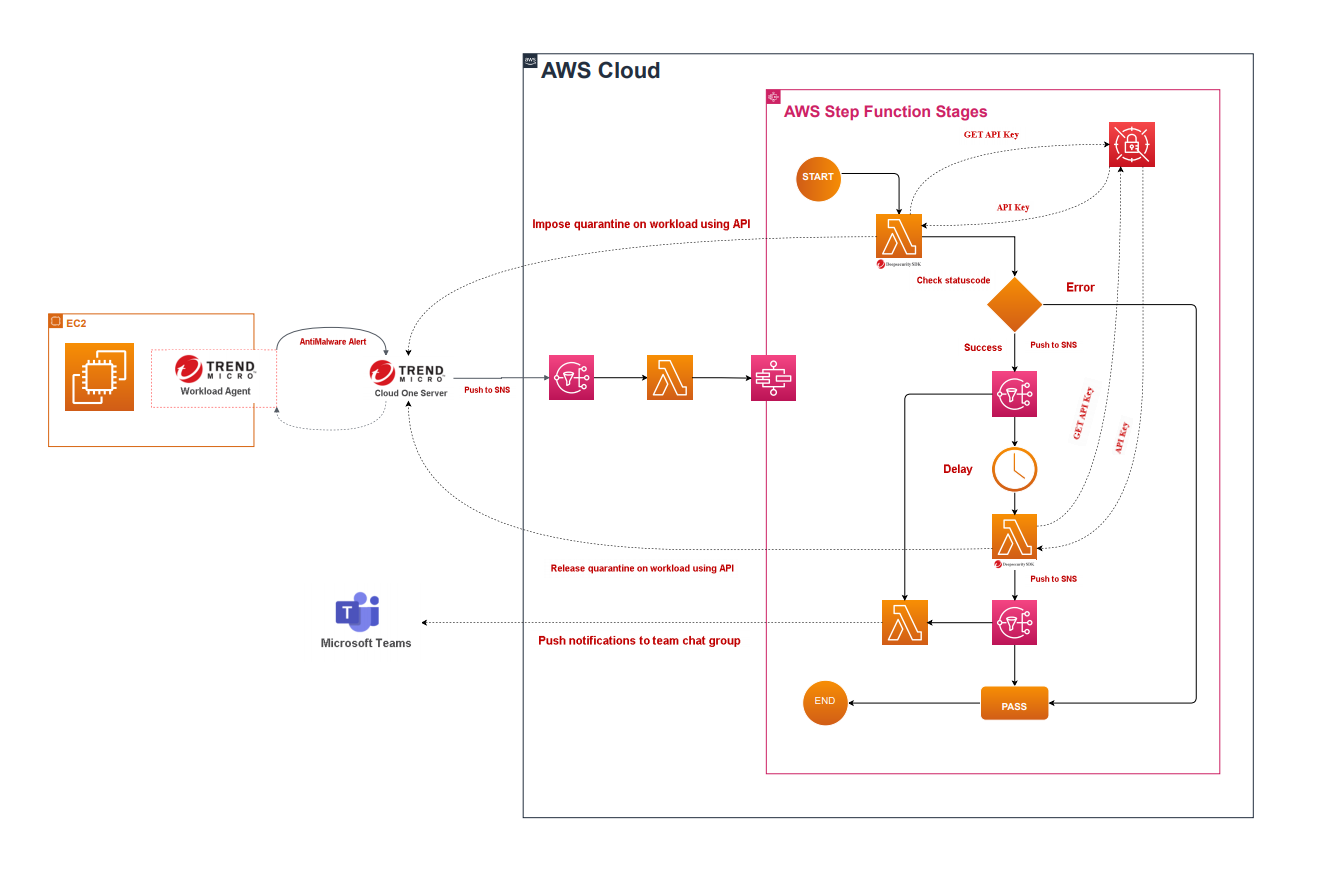
We have already integrated the test compute instance 18.188.15.133 (am-demo-1) [i-0d81213afa3ea2637] with Workload Security. Now that your instance is installed, let’s take a look at its configurations.
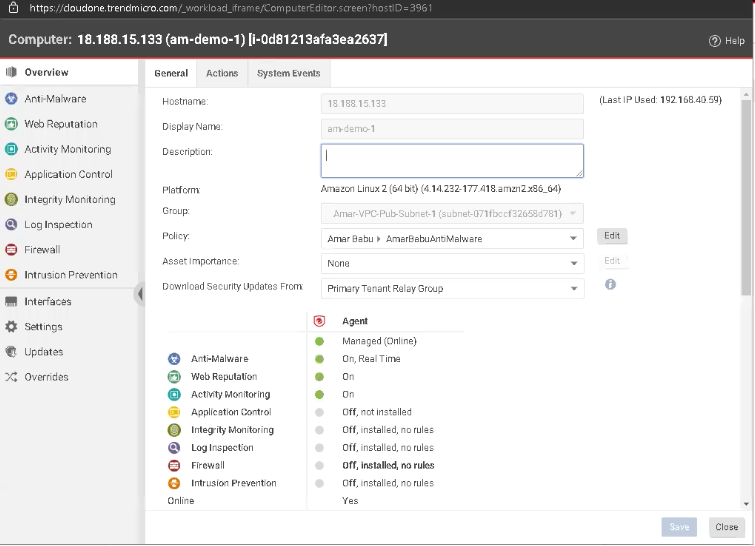
As you can see, Anti-Malware scanning is on, but Firewall is currently off, meaning there’s no filtration of ingress and egress traffic. For Anti-Malware, you can configure many rules, policies, and actions to be taken after detection. In this demo, we have configured it to activate the Firewall only after malware is detected. If no malware is detected, Firewall will remain off and reset to its original state, so you don’t have to worry about adjusting the rules every time.
Next, let’s dive deeper into the configurations for the four unique Lambda functions in our architecture.
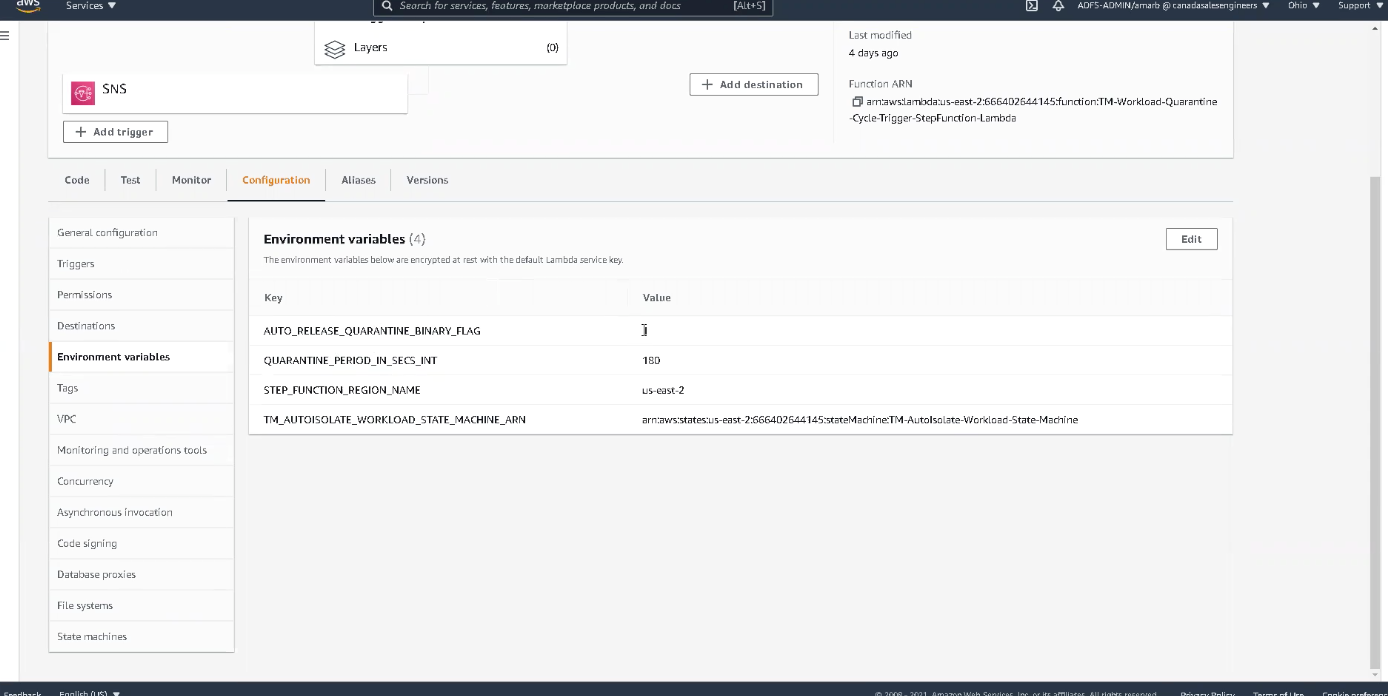
- Step Function (TM-Workload-Quarantine-Cycle-Trigger-StepFunction-Lambda): This function triggers the AWS Step Function cycle for the anti-malware event. Under Environment variables, you can see we have set up a delayed auto-release (value = 1. Indefinite quarantine value is 0) with a quarantine period of 180 seconds. You have the flexibility to set any time value of your choice, but for the purpose of this demo, we chose 3 minutes so you can see the entire lifecycle without waiting around for too long. It’s highly recommended that you indefinitely quarantine any potential threats until it is inspected and approved by a security professional.
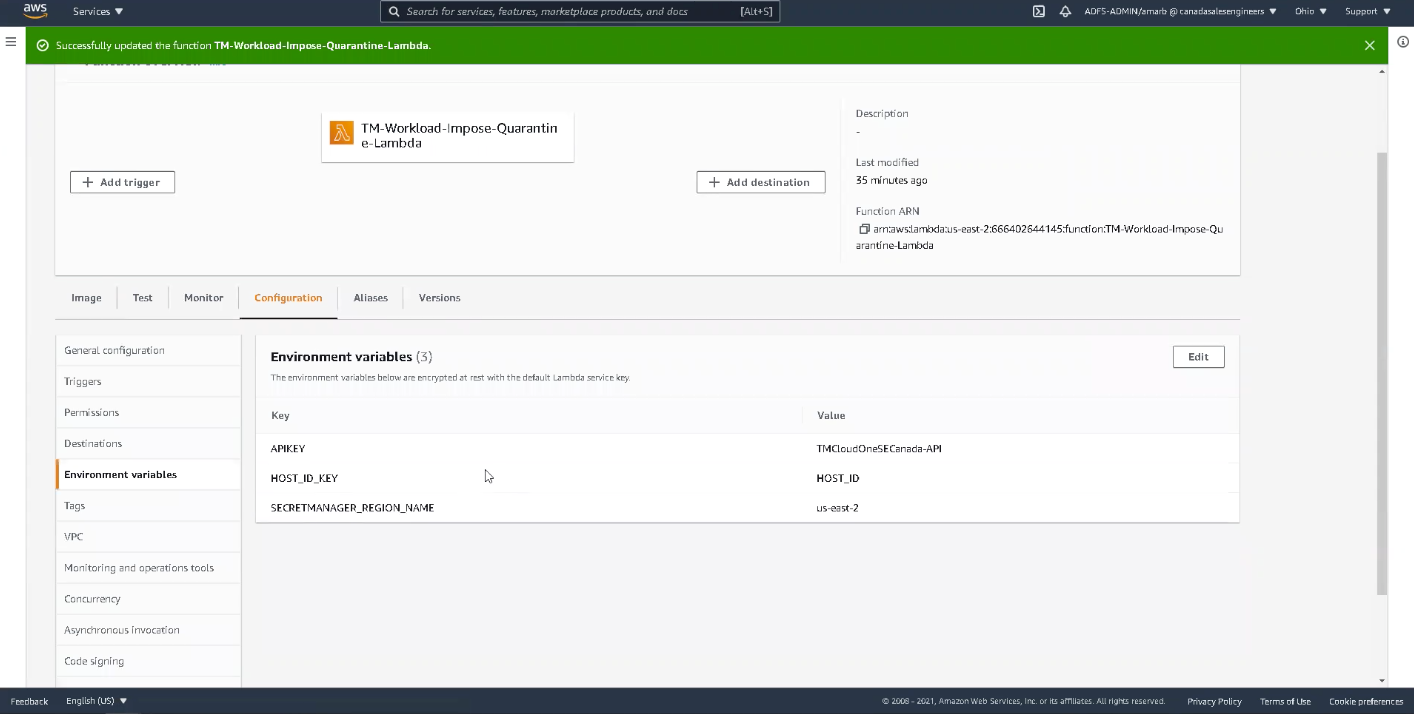
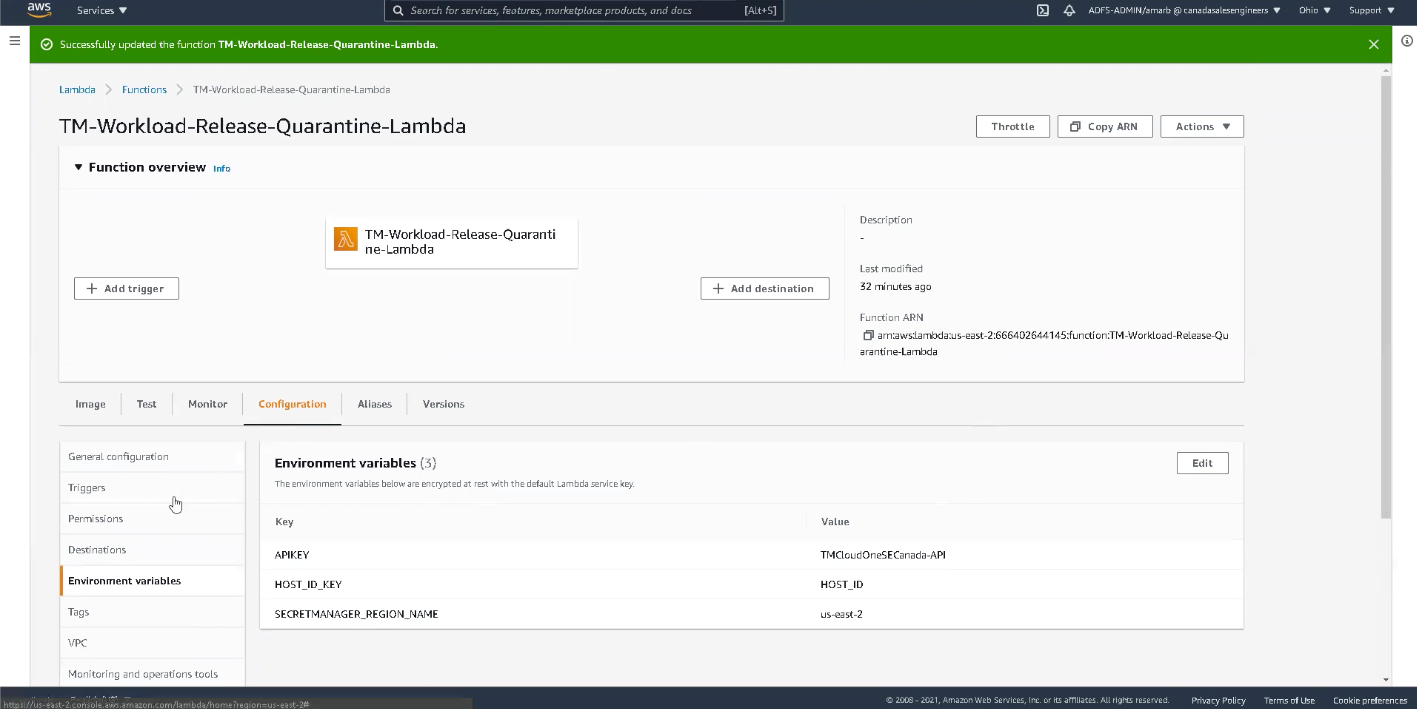
- Impose Quarantine (TM-Workload-Impose-Quarantine-Lambda): Here, we have configured our API key, Host ID, and AWS Secrets Manager. The API key is used to authenticate the function before it can communicate with the Trend Micro Cloud One server.
To configure API keys:
- Go to the Workload Security console
- Click Administration tab
- Click API Keys
- Click New and add the permissions, which will be stored in AWS Secrets Manager
- Release Quarantine: This is identical to the Impose Quarantine function but here we activate the release after 180 seconds.
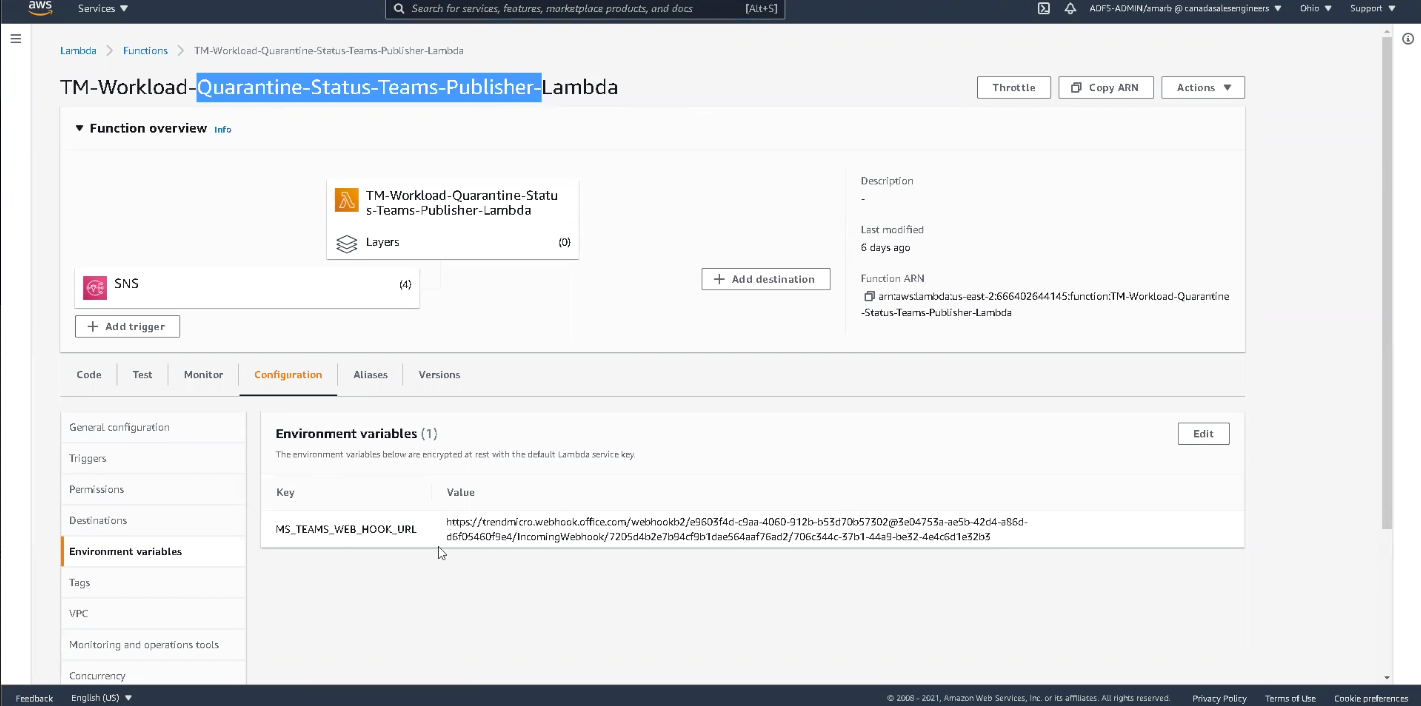
- Quarantine Status (TM-Workload-Quarantine-Status-Teams-Publisher-Lambda): This function sends an alert via Amazon SNS. Here you can specify where the notifications will be published, which in our case is Microsoft Teams. Setting up alerts is a great way to foster a collaborative environment and keep development and security teams on the same page.
Demo
Okay, now that we’ve covered the basics of our setup, let’s trigger the event:
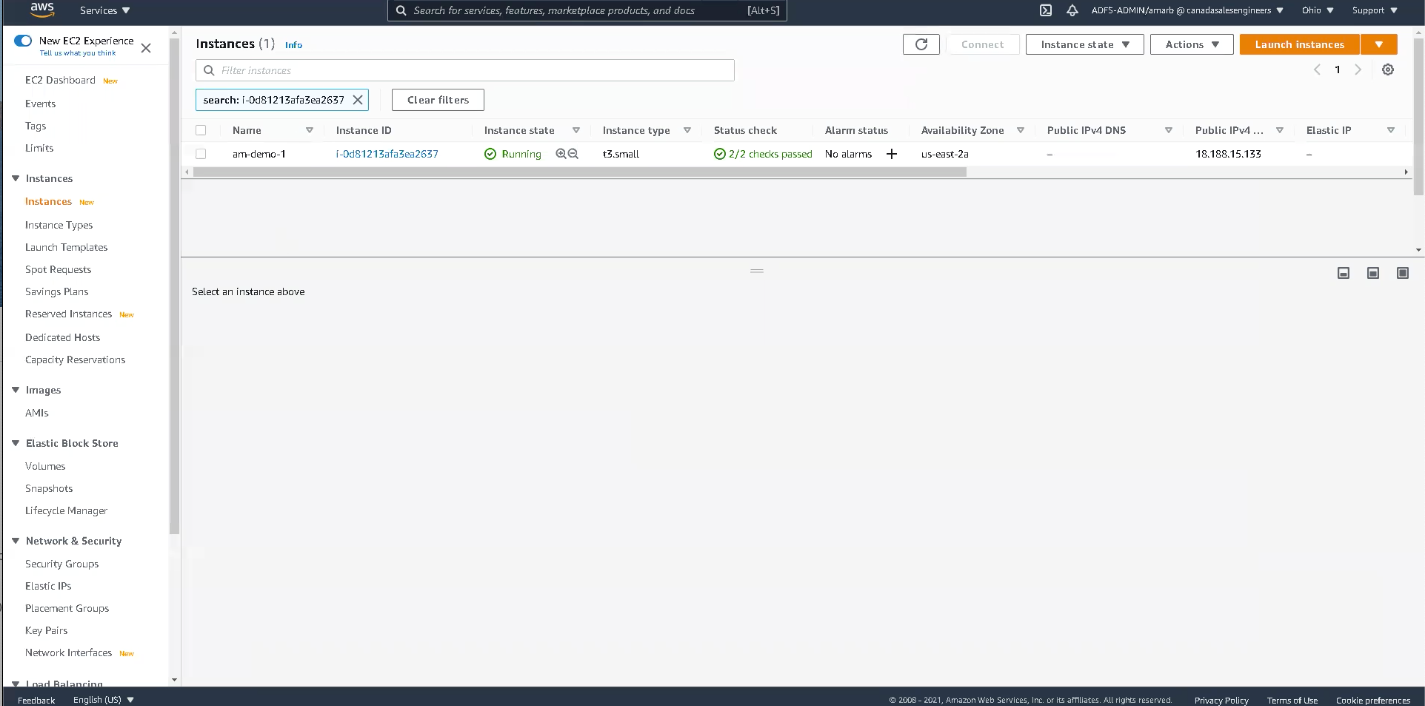
- Open your AWS EC2 dashboard and copy the public IP address (18.188.15.133) associated with the instance you’ve set up for this demo
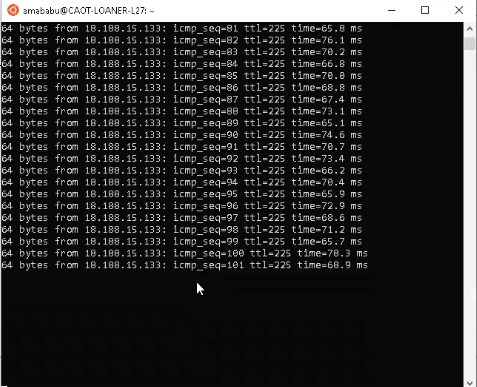
- Ping the IP address to check for the network connectivity. You should receive a response and see the traffic is flowing.
- Open the SSH session and input the EICAR malware text (X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*)
- Return to the Workload Security console, click Anti-Malware then scroll down.
- Under Malware Scan, click Full Scan for Malware.
- Go to Anti-Malware Events and you should see a new anti-malware event has been detected and the EICAR malware was identified (under Malware Type). Under Action Type, you will see the quarantine has been automatically triggered.
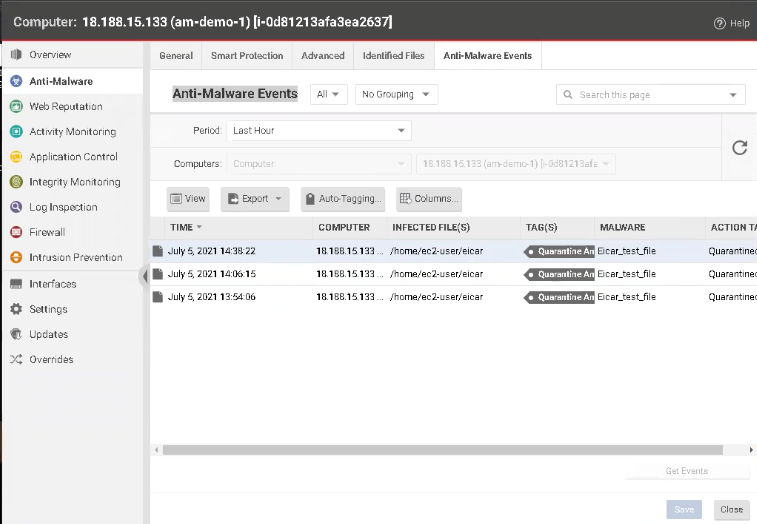
Now it’s time to sit back and watch the magic of Workload Security.
- After the anti-malware event begins, it will communicate with the first Lambda function in line (TM-Workload-Quarantine-Cycle-Trigger-StepFunction-Lambda)
- In your Lambda dashboard:
- Click Step Functions
- Click State Machines
- Click TM-AutoIsolate_Workload_State-Machine
- Under Executions, you will see the step function is now running.
- Click on that function and scroll down to Graph inspector, which shows the workflow of the anti-malware event. The screenshot below shows we have successfully passed through the first three stages and are in the delayed quarantine phase.
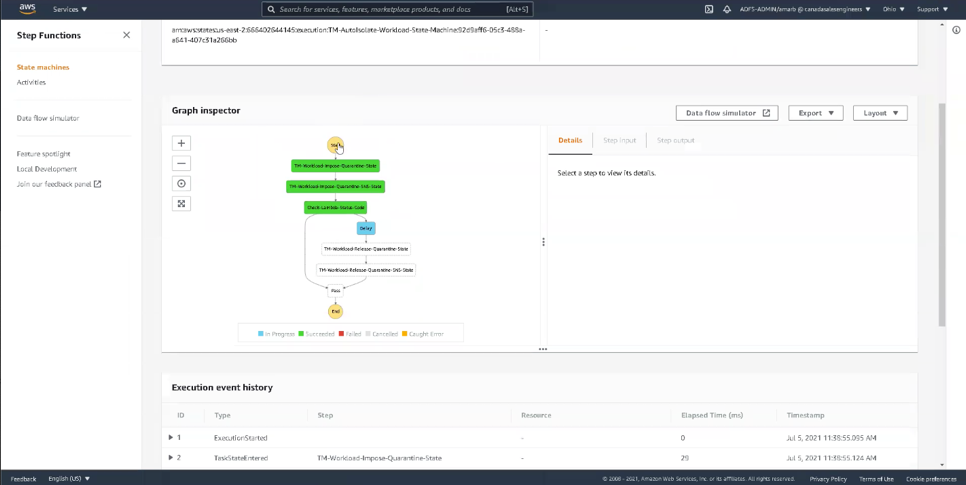
- After AWS Step Functions is triggered, the second custom Lambda (TM-Workload-Impose-Quarantine-Lambda) is prompted to communicate with the AWS Secrets Manager, fetch the API key to authenticate itself, and send instructions to the Trend Micro Cloud One Server to quarantine the malware. In this demo, we have chosen to quarantine with a delayed release, so production isn’t abruptly interrupted by any false positives.
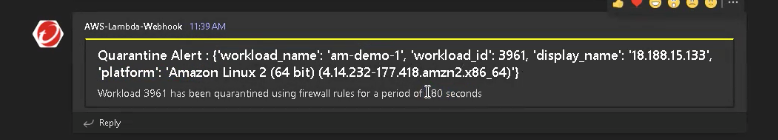
- Now that the malware is being quarantined, Amazon SNS will send a notification to Microsoft Teams to release an alert. Amazon SNS color codes each alert to make it easy for busy teams to identify the current stage of the event. Yellow = quarantine, orange = indefinite quarantine, and green = release.
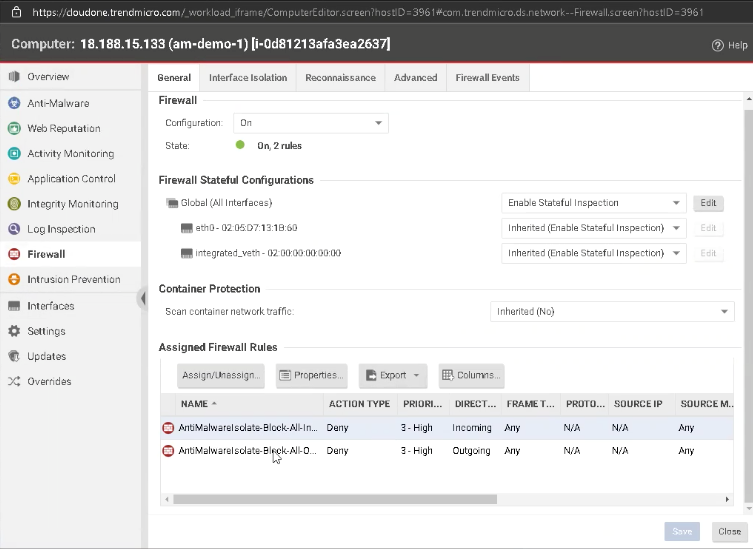
- After the malware has been quarantined, check that the Firewall is now active by going to the Workload Security console and selecting the compute instance for this demo. You should see that it has been activated with two new rules: block all incoming traffic and block all outgoing traffic. These are level three priority rules, meaning only one type of communication is being sent. It is not advised to use level four priority rules because it will interrupt communication between the Workload Agent and the Trend Micro Cloud One Server.
- You can also test that the Firewall is working by trying to send a ping to check network connectivity. You should see that all the traffic has stopped, which contains the threat so it cannot travel to other areas of your environment. You also will be unable to type and perform communications in the SSH session box. Perfect, everything is running as it should be.
- After 180 seconds have passed, you’ll see the Graph inspector is now in the Release Cycle stage. Subsequently, you should receive the release alert in Teams.
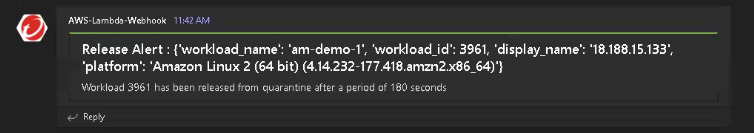
- Do a final check to make sure traffic is running again and that you can type and perform communications. Et voila, you are done!
Next steps
Not all automation is equal. Just like how a vendor sells different models of robot vacuums, automation capabilities vary from one security solution to another. Workload Security can automatically detect and protect against new and existing workloads and integrates with your cloud services from AWS, Microsoft Azure, Google Cloud Platform™, and more.
To learn more about the capabilities of Workload Security for DevOps, check out this video.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE




