Aviation-themed phishing campaign pushed off-the-shelf RATs into inboxes for 5 years
A phishing campaign that mostly targeted the global aviation industry may be connected to Nigeria, according to Cisco Talos.
The malicious campaigns centred around phishing emails linking to “off-the-shelf malware” being sent to people around the world – even those with a marginal interest in commercial aviation.
Although Talos couldn’t confirm the threat actor behind the campaign was actually based in Nigeria or associated with the Nigerian state, Cisco’s infosec arm was able to say with confidence that the campaign had been running for at least three years.
It compiled a list of IPs used by the threat actor’s domain and concluded that 73 per cent of those were based in the African nation, “further strengthening the theory that the actor in question is based in Nigeria.”
“Our research shows that actors that perform smaller attacks can keep doing them for a long period of time under the radar,” said Talos, adding that these seemingly small-fry attacks “can lead to major incidents at large organizations.”
The firm added: “These are the actors that feed the underground market of credentials and cookies, which can then be used by larger groups.”
Building on previous research from Microsoft, Cisco Talos dived into malicious emails that contained a link purporting to lead to a PDF file containing aviation-related information.
One example was themed to appear as if it had been sent by aviation safety authorities in Dubai. The PDF link, however, took unwary readers to a site hosting a .vbs script, hosted on Google Drive.
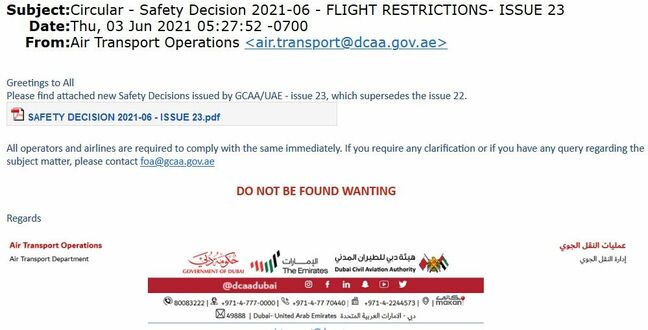
An example of the aviation-themed phishing campaign seen by Cisco Talos
Other lures included mentions of Bombardier, the well-known business jet manufacturer, and “Trip Itinerary Details”. Those were associated with the domain kimjoy[.]ddns[.]net as well as akconsult[.]linkpc[.]net.
“Analysis of the activity associated with the domain reveals that this actor has used several RATs and that, since August 2018, there are samples communicating with this domain with names that indicate the adversary wanted to target the aviation industry,” said Talos.
The malicious script eventually downloaded the CyberGate remote-access trojan (RAT) onto the victim’s machine. CyberGate, aka Rebhip, allows complete control of the target device including remote shell interaction and keylogging functionality. It is also freely available, as one Briton allegedly discovered – not that it did him much good.
Another domain Talos associated with the malware campaign was delivering the AsyncRAT trojan. VMware’s security unit Carbon Black defines it as a run-of-the-mill RAT, saying it “can perform many harmful activities such as disabling Windows Defender”.
Cisco Talos concluded: “In this case, we have shown that what seemed like a simple campaign is, in fact, a continuous operation that has been active for three years, targeting an entire industry with off-the-shelf malware disguised with different crypters.”
Even the least complicated of threats can still be meaningful if you’re not careful enough. ®
READ MORE HERE
