AWS has new tool for those leaky S3 buckets so, yeah, you might need to reconfigure a few things
re:Invent At its re:Invent event under way in Las Vegas, Amazon Web Services (AWS) dropped the veil on a new tool to help customers to avoid spewing data stored on its S3 (Simple Storage) service to world+dog.
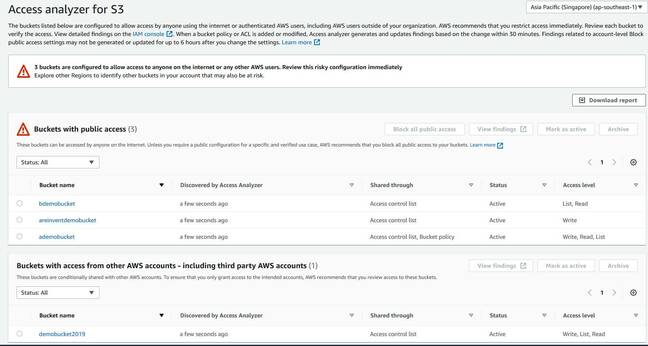
“Access Analyzer for S3 is a new feature that monitors your access policies, ensuring that the policies provide only the intended access to your S3 resources,” the cloud giant said.
Customers can enable Access Analyzer via a new option in the console for IAM (Identity and Access Management). The tool will then alert you when a bucket (an area of storage in S3) is configured to allow public access or access to other AWS accounts. The implication of the tool, of course, is that this is sometimes done accidentally via misconfigured policies or access control lists (ACLs).
A new single-click option will block public access – hopefully letting you avoid unauthorised use of the data before it is too late. The tool will also let you see which policy or ACL allows the access so that you know what to fix.
Some S3 buckets are, of course, deliberately public – as resources for a website, for example, or downloads to deploy or support an application. In this case, you can mark them within the tool to acknowledge that this is working as intended.
At the re:Invent shindig, senior principal engineer Becky Weiss presented at a packed session on the fundamentals of AWS security. She explained that “there are security patterns that repeat everywhere in AWS” and divided the subject into three parts. The first is IAM, used to control access to cloud infrastructure. “Every AWS service uses IAM,” she said. The second is KMS (Key Management Service), used to control data encryption. The third is VPC (Virtual Private Cloud), used to control access to a customer’s virtual network.
Weiss gave concise explanations of how IAM policies work in AWS, and what you do if you need to allow access from one AWS account to resources which belong to a different account. AWS uses Organizations to make it easier to manage multiple accounts.
She also introduced VPC private and public subnets, security groups, which are firewall rules controlling access to these subnets, and VPC endpoints, which let you manage network access to resources outside the VPC such as AWS serverless resources like S3.
Securing AWS resources is challenging because of the number of different services and the scale of their usage. The starting point is to understand the security patterns which AWS has provided, and which Weiss did a good job of outlining.
These are all things that every AWS customer should understand, but at the end of the session your correspondent overheard one attendee say to another: “So basically we need to reconfigure everything.”
As users enable the new Access Analyzer, our hunch is that no small number of alerts will be pinging. ®
Sponsored: How to get more from MicroStrategy by optimising your data stack
READ MORE HERE