Backdoored Images Downloaded 5 Million Times Finally Removed From Docker Hub

A single person or group may have made as much as $90,000 over 10 months by spreading 17 malicious images that were downloaded more than 5 million times from Docker Hub, researchers said Wednesday. The repository finally removed the submissions in May, more than eight months after receiving the first complaint.
Docker images are packages that typically include a pre-configured application running on top of an operating system. By downloading them from Docker Hub, administrators can save huge amounts of set-up time. Last July and August one or more people used the Docker Hub account docker123321 to upload three publicly available images that contained surreptitious code for mining cryptocurrencies. In September, a GitHub user complained one of the images contained a backdoor.
Eight months of inaction
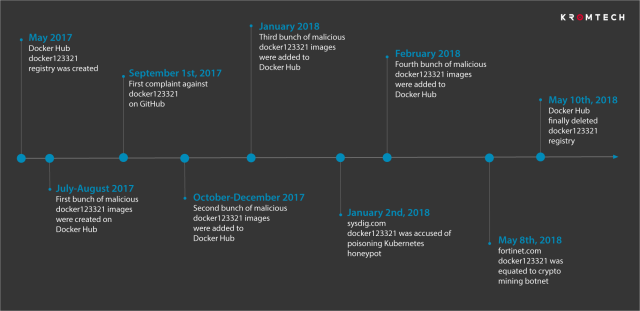
Neither the Docker Hub account nor the malicious images it submitted were taken down. Over the coming months, the account went on to submit 14 more malicious images. The submissions were publicly called out two more times, once in January by security firm Sysdig and again in May by security company Fortinet. Eight days after last month’s report, Docker Hub finally removed the images. The following image, provided by security firm Kromtech, shows the chronology of the campaign.
By the time Docker Hub removed the images, they had received 5 million “pulls.” A wallet address included in many of the submissions showed it had mined almost 545 Monero digital coins, worth almost $90,000.
The malicious image campaign, detailed in a blog post published Wednesday by security firm Kromtech, provides a cautionary tale for developers.
“For ordinary users, just pulling a Docker image from Docker Hub is like pulling arbitrary binary data from somewhere, executing it, and hoping for the best without really knowing what’s in it,” the researchers wrote.
They went on to warn that, despite the images being pulled from Docker Hub, many servers that installed the images may still be infected. The researchers also said that the malware may continue to run even after administrators think they’ve deleted the malicious image. Wednesday’s post includes the names of all 17 of the packages. Anyone who installed one should take time to analyze their computers for signs of infection.
READ MORE HERE