CAN Do Attitude: How Thieves Steal Cars Using Network Bus
Automotive security experts say they have uncovered a method of car theft relying on direct access to the vehicle’s system bus via a smart headlamp’s wiring.
It all started when a Toyota RAV4 belonging to one of the tech gurus suffered suspicious damage to the front wing and headlight housing, and was eventually successfully stolen. Some sleuthing and reverse engineering revealed how the motor was finally nicked.
Ken Tindell, CTO of Canis Automotive Labs, said the evidence pointed to thieves’ successful execution of a so-called CAN injection.
A Controller Area Network (CAN) bus is present in nearly all modern cars, and is used by microcontrollers and other devices to talk to each other within the vehicle and carry out the work they are supposed to do.
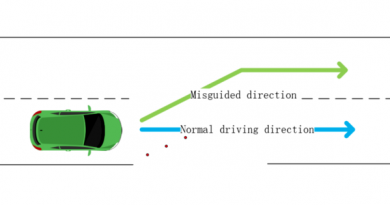
In a CAN injection attack, thieves access the network, and introduce bogus messages as if it were from the car’s smart key receiver. These messages effectively cause the security system to unlock the vehicle and disable the engine immobilizer, allowing it to be stolen. To gain this network access, the crooks can, for instance, break open a headlamp and use its connection to the bus to send messages. From that point, they can simply manipulate other devices to steal the vehicle.
“In most cars on the road today, these internal messages aren’t protected: the receivers simply trust them,” Tindell detailed in a technical write-up this week.
The discovery followed an investigation by Ian Tabor, a cybersecurity researcher and automotive engineering consultant working for EDAG Engineering Group.
It was driven by the theft of Tabor’s RAV4. Leading up to the crime, Tabor noticed the front bumper and arch rim had been pulled off by someone, and the headlight wiring plug removed. The surrounding area was scuffed with screwdriver markings, which, together with the fact the damage was on the kerbside, seemed to rule out damage caused by a passing vehicle. More vandalism was later done to the car: gashes in the paint work, molding clips removed, and malfunctioning headlamps.
A few days later, the Toyota was stolen.
Refusing to take the pilfering lying down, Tabor used his experience to try to figure out how the thieves had done the job. The MyT app from Toyota – which among other things allows you to inspect the data logs of your vehicle – helped out. It provided evidence that Electronic Control Units (ECUs) in the RAV4 had detected malfunctions, logged as Diagnostic Trouble Codes (DTCs), before the theft.
According to Tindell, “Ian’s car dropped a lot of DTCs.”
Various systems had seemingly failed or suffered faults, including the front cameras and the hybrid engine control system. With some further analysis it became clear the ECUs probably hadn’t failed, but communication between them had been lost or disrupted. The common factor was the CAN bus.
In reality, the faults were generated as the thieves broke into a front headlamp and tore out the wiring, and used those exposed connections to electrically access the CAN bus and send messages telling other parts of the system to basically give the miscreants the car. Disconnecting the headlamp caused the wave of aforementioned network communications failures. But how were the crucial unlock messages actually injected?
Tabor took to the dark web to look for equipment that may have been involved in the theft of his car and found a number of devices targeting the CAN bus. He worked with Noel Lowdon of vehicle forensics company Harper Shaw to look into reverse engineering a contender – a gadget capable of talking to a connected CAN bus and cunningly concealed within a normal-looking Bluetooth smart speaker. The fake speaker comes with cables you insert into an exposed bus connector, you press a button on the box, and it sends the required messages to unlock the car.
Since Tindell had helped develop Volvo’s first CAN-based car platform, he was brought in to help understand the gadget’s involvement in the car theft. More technical details are provided in the above write-up.
As the automotive industry develops ever more sophisticated tech systems for their vehicles, scumbags find more inventive ways to abuse these systems for their own ends.
Last year, a keyless entry exploit was demonstrated against Honda Civics manufactured between 2016 and 2020. Weak crypto used in the keyless entry system in Tesla’s Model S was blamed for the ease with which researchers could gain entry. Back in 2016, security researchers demonstrated how crooks could break into cars at will using wireless signals that could unlock millions of vulnerable VWs. ®
READ MORE HERE