Chaos Ransomware: A Proof of Concept With Potentially Dangerous Applications Threats Analyst

Ransomware
Since June 2021, we’ve been monitoring an in-development ransomware builder called Chaos, which is being offered for testing on an underground forum.
Since June 2021, we’ve been monitoring an in-development ransomware builder called Chaos, which is being offered for testing on an underground forum. While it’s purportedly a .NET version of Ryuk, closer examination of the sample reveals that it doesn’t share much with the notorious ransomware. In fact, early versions of Chaos, which is now in its fourth iteration, were more akin to a destructive trojan than to traditional ransomware.
In this blog entry, we take a look at some of the characteristics of the Chaos ransomware builder and how its iterations added new capabilities.
Chaos has undergone rapid evolution from its very first version to its current iteration, with version 1.0 having been released on June 9, version 2.0 on June 17, version 3.0 on July 5, and version 4.0 on Aug. 5.
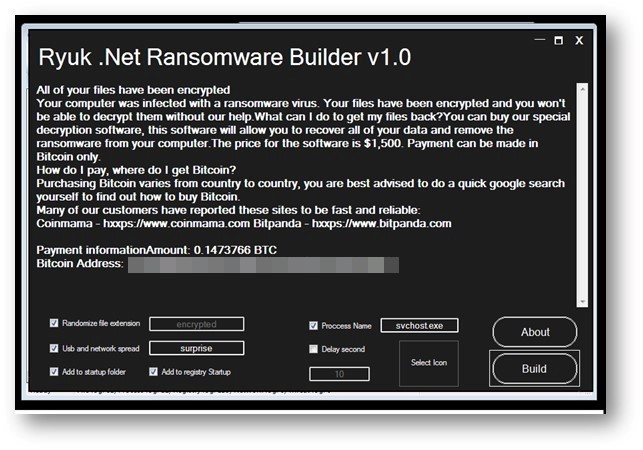
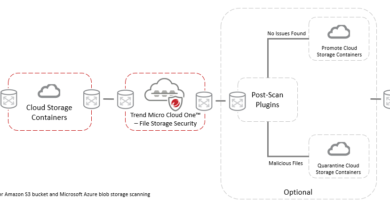
The most notable characteristic of the first version of the Chaos builder was that, despite having the Ryuk branding in its GUI, it had little in common with the ransomware. In fact, it wasn’t even traditional ransomware, but rather a destructive trojan. Instead of encrypting files (which could then be decrypted after the target paid the ransom), it replaced the files’ contents with random bytes, after which the files were encoded in Base64. This meant that affected files could no longer be restored, providing victims no incentive to pay the ransom.
It did, however, display certain characteristics found in other ransomware families. For example, it searched the following file paths and extensions to infect:
- \\Contacts
- \\Desktop
- \\Desktop
- \\Documents
- \\Downloads
- \\Favorites
- \\Links
- \\Music
- \\OneDrive
- \\Pictures
- \\Saved Games
- \\Searches
- \\Videos
- .3gp
- .7z
- .7-zip
- .accdb
- .ace
- .amv
- .apk
- .arj
- .asp
- .aspx
- .avi
- .backup
- .bak
- .bay
- .bk
- .blob
- .bmp
- .bz2
- .cab
- .cer
- .contact
- .core
- .cpp
- .crt
- .cs
- .css
- .csv
- .dat
- .db
- .dll
- .doc
- .docm
- .docx
- .dwg
- .exif
- .flv
- .gzip
- .htm
- .html
- .ibank
- .ico
- .ini
- .iso
- .jar
- .java
- .jpe
- .jpeg
- .jpg
- .js
- .json
- .jsp
- .lnk
- .lzh
- .m4a
- .m4p
- .m4v
- .mdb
- .mkv
- .mov
- .mp3
- .mp3
- .mp3
- .mp4
- .mpeg
- .mpg
- .ods
- .odt
- .p7c
- .pas
- .pdb
- .php
- .png
- .ppt
- .pptx
- .psd
- .py
- .rar
- .rb
- .rtf
- .settings
- .sie
- .sql
- .sum
- .svg
- .tar
- .txt
- .vdi
- .vmdk
- .wallet
- .wav
- .webm
- .wma
- .wmv
- .wps
- .xls
- .xlsb
- .xlsm
- .xlsx
- .xml
- .xz
- .zip
It then dropped a ransomware note named read_it.txt, with a demand for a rather sizeable ransom in bitcoin.
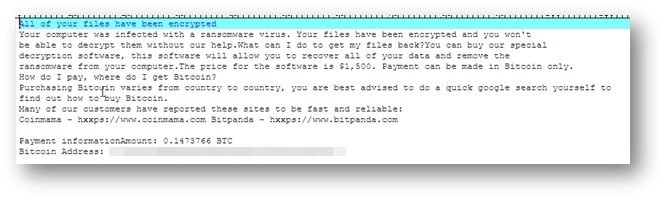
One of the more interesting functions of Chaos version 1.0 was its worming function, which allowed it to spread to all drives found on an affected system. This could permit the malware to jump onto removable drives and escape from air-gapped systems.
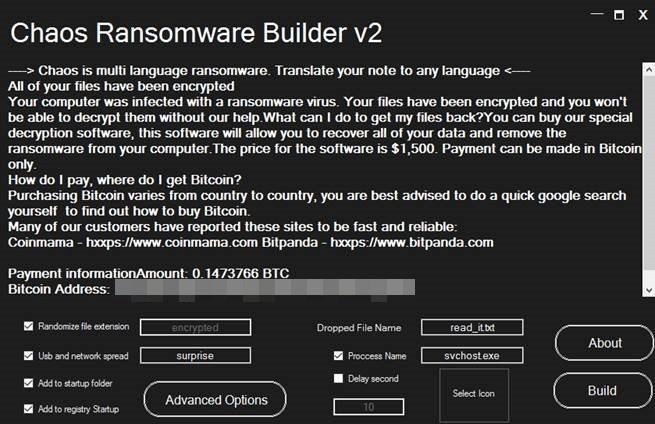
The second version of Chaos added advanced options for administrator privileges, the ability to delete all volume shadow copies and the backup catalog, and the ability to disable Windows recovery mode.
However, version 2.0 still overwrote the files of its targets. Members of the forum where it was posted pointed out that victims wouldn’t pay the ransom if their files couldn’t be restored.
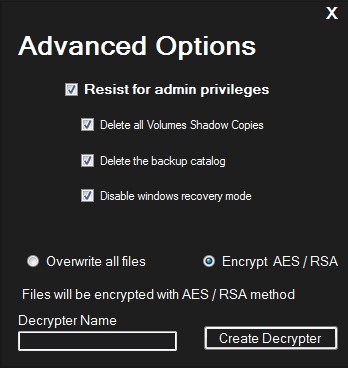
With version 3.0, the Chaos ransomware builder gained the ability to encrypt files under 1 MB using AES/RSA encryption, making it more in line with traditional ransomware. It also came with its own decrypter builder.
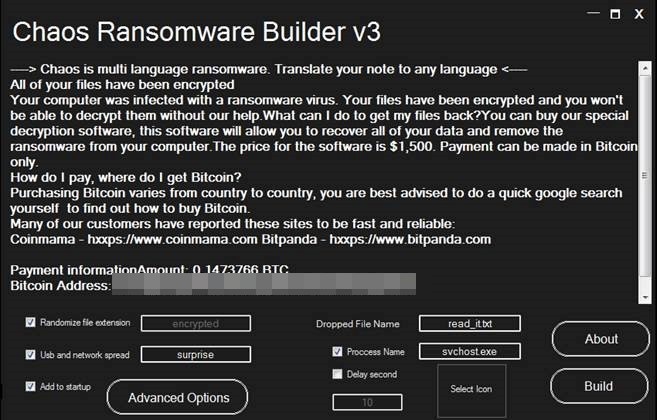
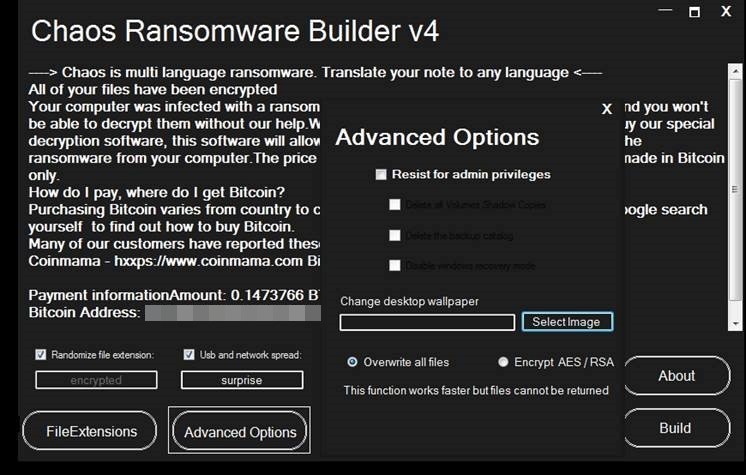
The fourth iteration of Chaos expands the AES/RSA encryption by increasing the upper limit of files that can be encrypted to 2 MB. In addition, it gives the ransomware builder’s users the ability to add their own extensions to affected files and the ability to change the desktop wallpaper of their victims.
We haven’t seen any active infections or victims of the Chaos ransomware. However, in the hands of a malicious actor who has access to malware distribution and deployment infrastructure, it could cause great damage to organizations.
In our view, the Chaos ransomware builder is still far from being a finished product since it lacks features that many modern ransomware families possess, such as the ability to collect data from victims that could be used for further blackmail if the ransom is not paid.
The following are the hashes and our detections for the different Chaos ransomware builder versions:
|
SHA-256 |
Detection |
TrendX detection |
Version |
|
0d8b4a07e91e02335f600332644e8f0e504f75ab19899a58b2c85ecb0887c738 |
Trojan.MSIL.FAKERYUKBUILD.THFAFBA |
N/A |
Chaos Ransomware builder version 1.0 |
|
325dfac6172cd279715ca8deb280eefe3544090f1583a2ddb5d43fc7fe3029ed |
Trojan.MSIL.FAKERYUKBUILDER.AA |
Ransom.Win32.TRX.XXPE50FFF046E0002 |
Chaos Ransomware builder version 2.0 |
|
63e28fc93b5843002279fc2ad6fabd9a2bc7f5d2f0b59910bcc447a21673e6c7 |
Trojan.MSIL.FAKERYUKBUILDER.AA |
Ransom.Win32.TRX.XXPE50FFF046E0002 |
Chaos Ransomware builder version 3.0 |
|
0d8b4a07e91e02335f600332644e8f0e504f75ab19899a58b2c85ecb0887c738 |
Trojan.MSIL.FAKERYUKBUILD.THFAFBA |
N/A |
Chaos Ransomware builder version 4.0 |
We also proactively detect the following components:
|
Detection |
Note |
|
Ransom.MSIL.CHAOSBUILDER.SMYPBHET |
Chaos ransomware builder and decrypter |
|
Ransom.MSIL.CHAOS.SMYPBHET |
Main Chaos ransomware executable |
|
PUA.MSIL.CHAOS.SMYPBHET.decryptor |
Chaos ransomware decrypter |
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE