Chinese Hacking Group Impersonates Afghan President To Infiltrate Government Agencies
A Chinese-speaking hacking group is performing ongoing cyberattacks against the Afghan government by impersonating its president.
On Thursday, Check Point Research (CPR) said that the Office of the President of Afghanistan, representing President Ashraf Ghani, is being used as a lure in spear phishing emails designed to infiltrate government agencies in the country, of which a successful attack has led to the compromise of the Afghan National Security Council (NSC).
It is thought that an advanced persistent threat (APT) group called IndigoZebra is responsible. The Chinese-speaking cyberattackers have targeted former Soviet Republics previously, as noted by Kaspersky.
Dupe email samples seen by the cybersecurity firm pretend to be from the president’s office and ask for an urgent review of modifications to a document relating to an upcoming press conference. The researchers say that these emails are sent from the compromised email inboxes of past, high-profile victims.
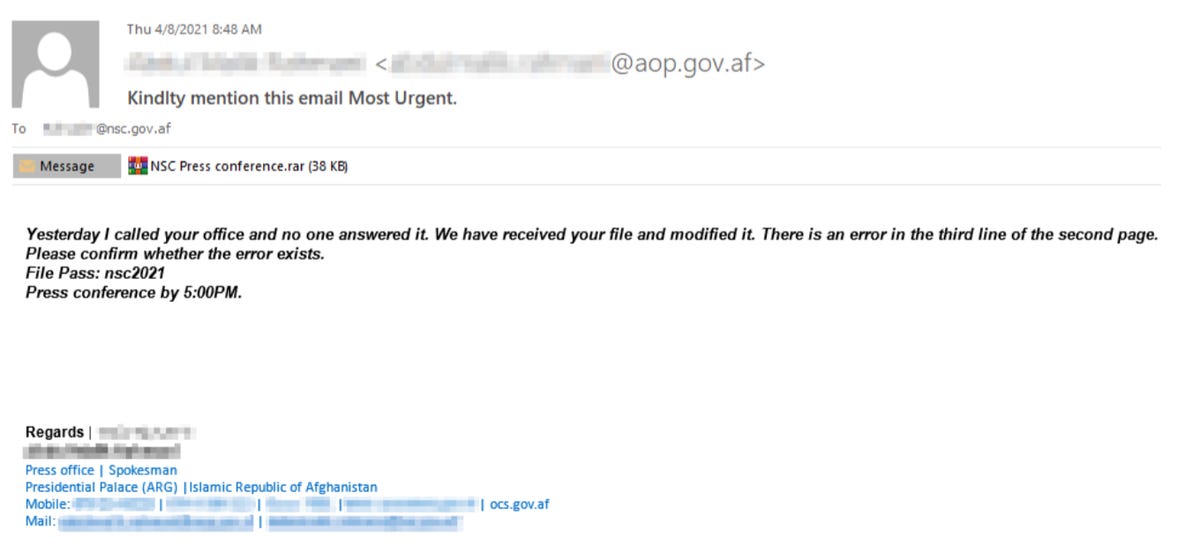
The file is a password-protected .RAR archive named NSC Press conference.rar. If a victim opens the file, they receive a Windows executable (NSC Press conference.exe), which deploys a malware dropper and the “xCaon” backdoor which maintains persistence by setting a registry key.
The backdoor is able to download and upload files, run commands issued through a command-and-control (C2) server, and steal data.
Dropbox is being abused as a form of C2 server in the latest version of this backdoor, dubbed “BoxCaon” by CPR.
Every victim secured by the threat actors is assigned a unique and pre-configured folder, named after a victim’s MAC address, which contains instructions for the malware and also acts as a storage bucket for exfiltrated data.
CPR says that by using the Dropbox API, this “masks their malicious activities, as no communication to abnormal websites takes place.”
IndigoZebra will also deploy a NetBIOS scanner tool adopted by another Chinese APT, APT10/Stone Panda, and may maliciously execute network utility tools for reconnaissance in the quest for further targets.
Malware utilized by the group also includes Meterpreter, Poison Ivy, xDown, and the xCaon backdoor.
CPR says that the APT in question is also likely responsible for attacks dating back to 2014, in which political entities in Kyrgyzstan and Uzbekistan were targeted.
“While the IndigoZebra actor was initially observed targeting former Soviet republics such as Uzbekistan and Kyrgyzstan, we have now witnessed that its campaigns do not dial down, but on the contrary — they expand to the new targets in the region, with a new toolset,” the researchers commented.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
READ MORE HERE
