Cinobi Banking Trojan Targets Cryptocurrency Exchange Users via Malvertising Threat Researcher Threat Researcher

Cyber Threats
We found a new social engineering-based malvertising campaign targeting Japan that delivered a malicious application. The malicious application abused sideloading vulnerabilities to load and start the Cinobi banking trojan.
In a previous blog entry, we reported on a campaign, which we labeled “Operation Overtrap,” that targeted Japan with a new banking trojan called Cinobi. The campaign, which was perpetrated by a group we named “Water Kappa,” delivered Cinobi via spam. It also delivered the trojan using the Bottle exploit kit, which included newer Internet Explorer exploits CVE-2020-1380 and CVE-2021-26411 and was used for malvertising attacks that was distributed only to Microsoft Internet Explorer users. Throughout 2020 and the first half of 2021, we observed limited activity from the Bottle exploit kit, with traffic decreasing during the middle of June — possibly indicating that the group was turning to new tools and techniques.
Meanwhile, we found a new social engineering-based malvertising campaign targeting Japan that delivered a malicious application disguised as either a free porn game, a reward points application, or a video streaming application. The malicious application abused sideloading vulnerabilities to load and start the Cinobi banking trojan. We consider this to be a new campaign from Water Kappa that is aimed at users of web browsers other than Internet Explorer.
Looking into the Cinobi sample, we found that the overall functionality remained relatively the same, but the configuration had been updated to include several Japanese cryptocurrency exchange websites as part of the target list. The group started to use Cinobi to steal the credentials of its victim’s cryptocurrency account.
Infection Routine
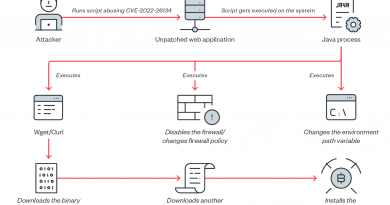
The campaign’s infection routine begins when a user received malvertisements that are disguised as advertisements of either Japanese animated porn games, reward points applications, or video streaming applications. While we have observed five different themes of their malvertisements, all of them attempt to trick victims into downloading the same archive with the same malware.
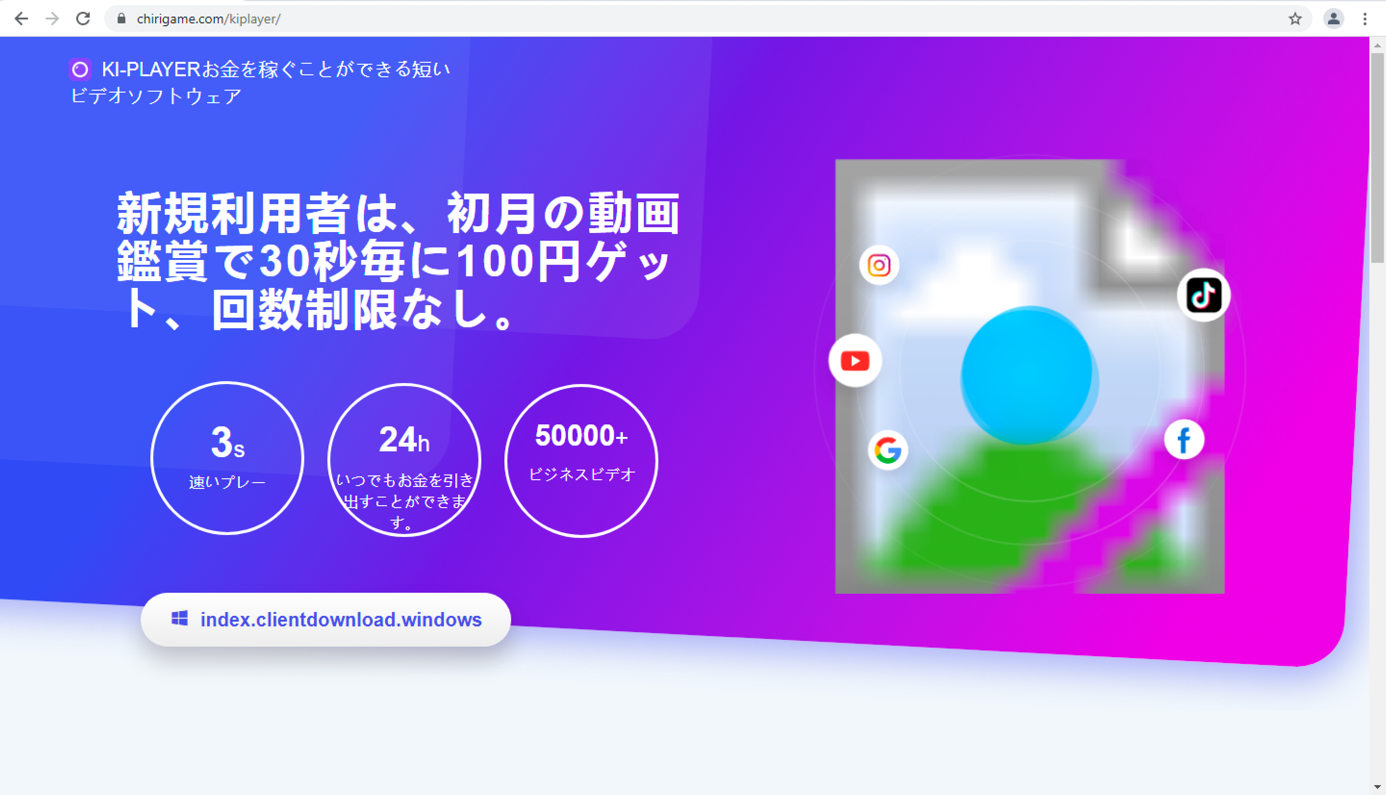
These malvertisements are likely cloned from legitimate websites by the malicious actor. Minor modifications are then applied, such as the removal of some buttons and the changing of certain information sections. The only buttons that are left lead to the new page — created by the malicious actor — that instructs the victims how to download and execute the application.
After clicking on the button with the text “index.clientdownload.windows” (as shown in figure 2), the landing page starts downloading the ZIP archive, which is followed by instructions for the victim on how to open, extract, and execute the main executable file. The other four malicious ads look visually different, but their behavior and landing page is similar.
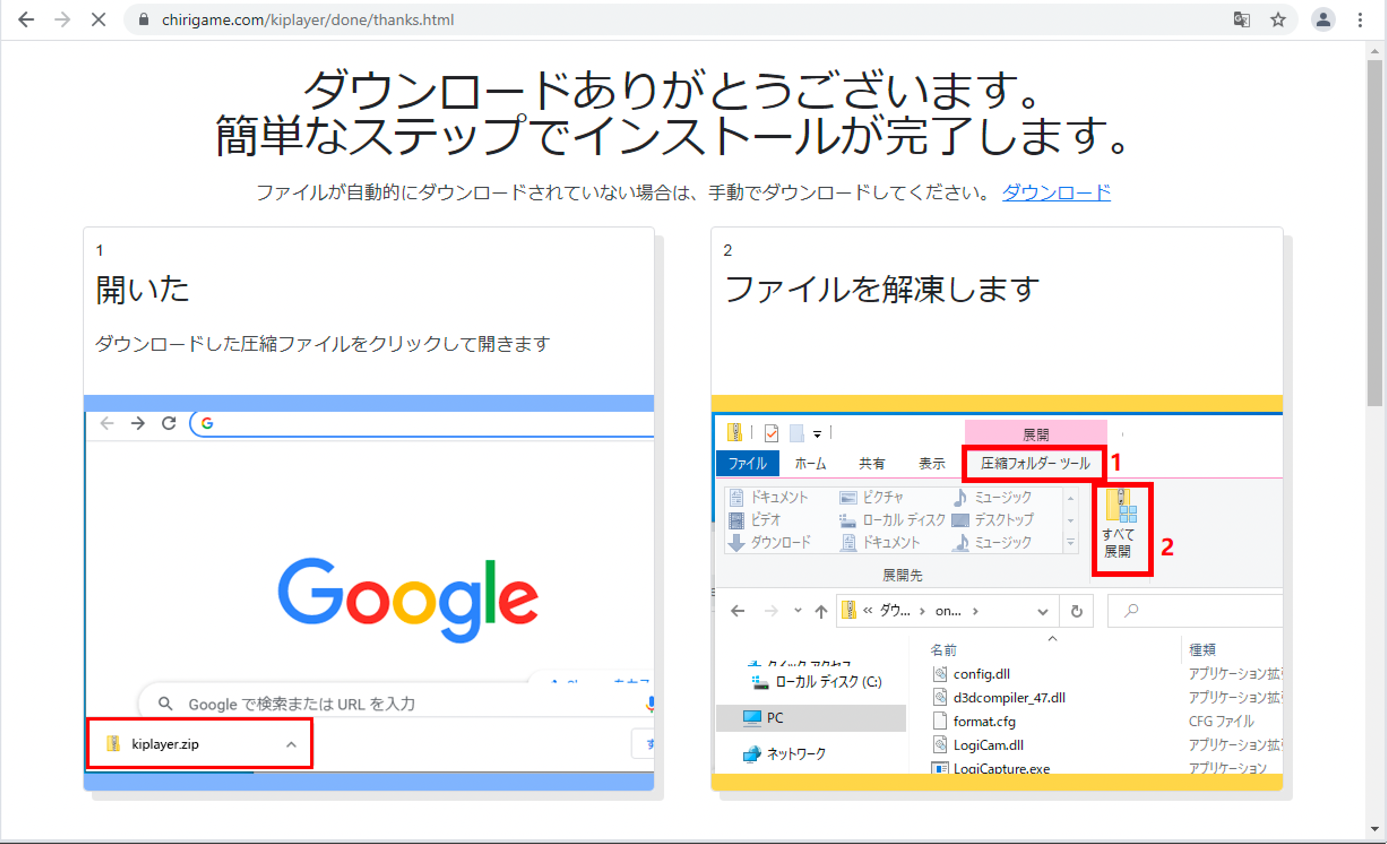
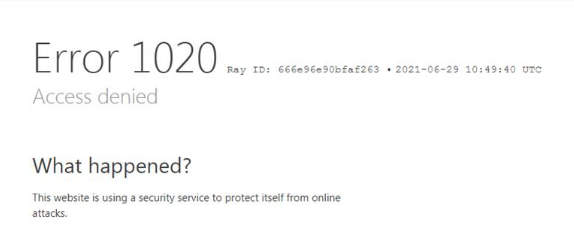
It is important to note that the access to the website is filtered based on the IP address. Non-Japanese IP addresses will see the following error message from Cloudflare.
Analysis of the malware
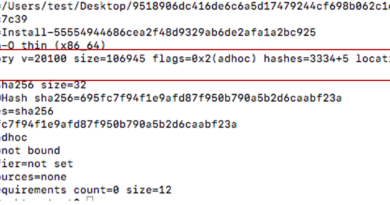
After extracting the ZIP archive, we noticed the listing seen in Figure 5. The files that we decided were interesting enough to be analyzed are marked in red.
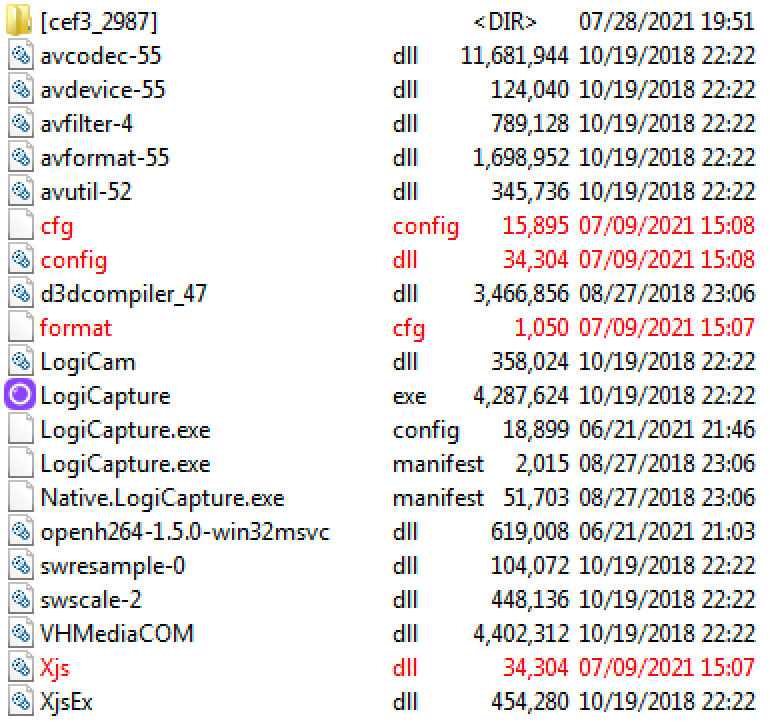
Most files are legitimate ones taken from an older version of the “Logitech Capture” application, dated 2018. The legitimate and signed LogiCapture.exe (08FB68EB741BF68F3CFC29A4AD3033D75AD57798ED826D926344015BDB8B0EBB) is instructed in LogiCapture.exe.config via custom application settings to load the Xjs.dll library.
The shellcode embedded into format.cfg copies config.dll and cfg.config to the temporary directory %TEMP%, renames these files to a.dll and 1.txt, and executes the export function named “a” of the a.dll library via the following command:
rundll32.exe “%TEMP%\a.dll”,a %TEMP%\1.txt
Config.dll (renamed to a.dll) resolves necessary APIs, loads the content of cfg.config (which is renamed to 1.txt), decrypts it with a XOR key, and executes the shellcode. The decrypted cfg.config is the first stage of the Cinobi baking trojan (as explained in our initial blogpost from 2020).
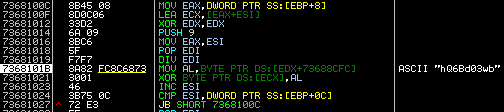
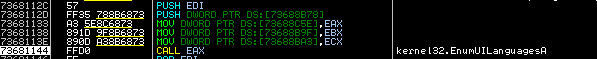
The Cinobi banking trojan is split into four stages, with each stage downloading additional components and possibly performing environment or anti-virtual machine (VM) checks. There are two command-and-control (C&C) servers, with one of them returning stages 2 to 4, while the other one returns the configuration files.
The malicious actor became more active in summer 2021 — we noticed a few more versions with slight differences from the ones described earlier. In addition to the application archive with four added malicious files (as shown in Figure 5), we also notice a refactored version of the archive with just three files (xjs.dll, format.cfg, and a file named “ros”), only three stages, and a single C&C server serving the configuration files.
In the refactored version, Xjs.dll decrypts and loads format.cfg, which is the first stage of the Cinobi banker. This stage, unlike our description from last year’s blog entry, does not download Tor and other additional stages from the first C&C server. Instead, it reads and extracts files from the file called “ros”, which is an encrypted package containing stages 2 and 3, a configuration file containing the C&C server, and an archive with Tor.
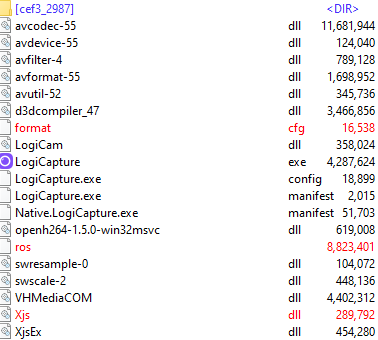
The most important of these is the configuration file containing websites targeted by the form-grabbing functionality. At the time of writing, we noticed that the banking trojan targets users of 11 Japanese financial institutions, with at least three of these involved in cryptocurrency trading.
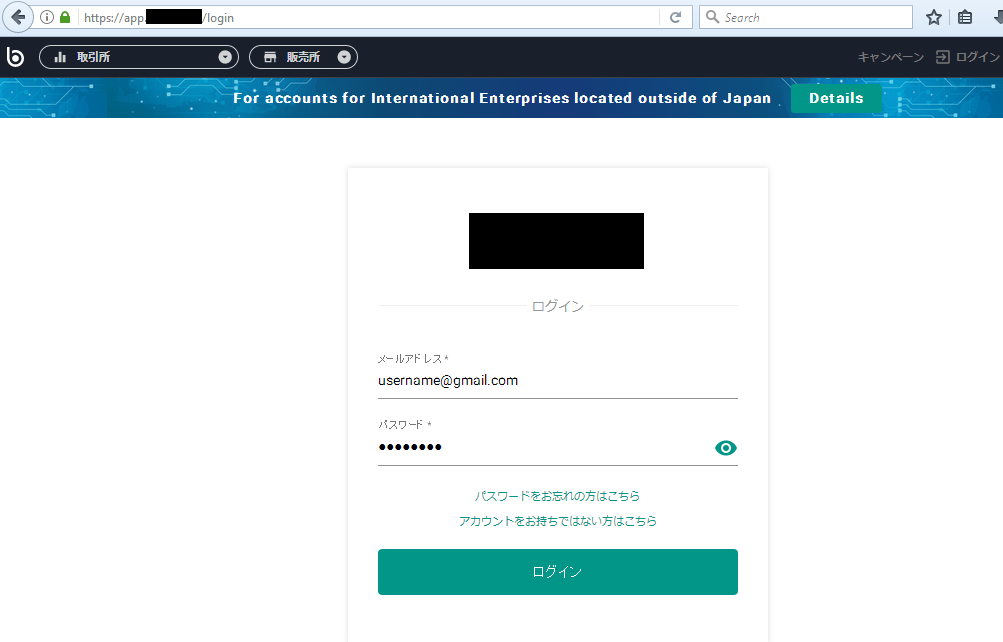
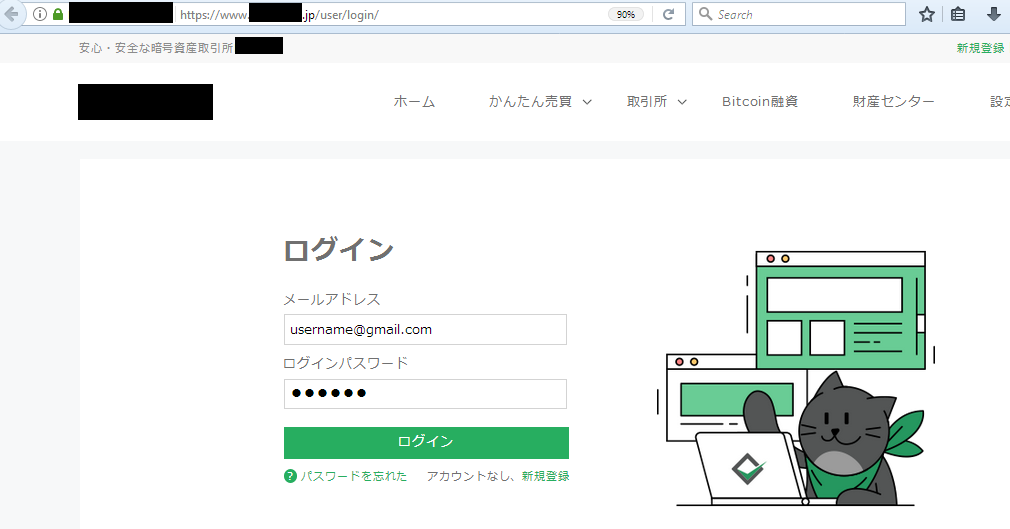
When a victim using an infected machine accesses one of the websites mentioned in the configuration file and sends the filled-out form back to the server, the form-grabbing feature of the banker gets activated. In the following screenshots, we show examples of login forms with filled data.
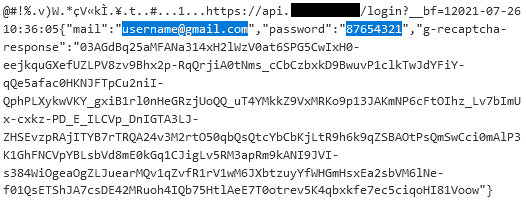
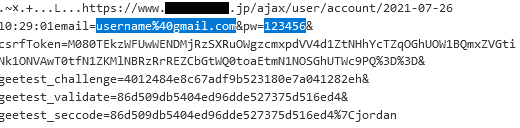
After clicking the submit button, a text file with an encrypted request briefly appears in the folder with the installed banking trojan. After the decryption of the temporary created text file, the highlighted stolen credentials can be seen.
Conclusion
The new malvertising campaign shows that Water Kappa is still active and continuously evolving their tools and techniques for greater financial gain — this one also aims to steal cryptocurrency. In order to minimize the chances of being infected, users need to be wary of suspicious advertisements on shady websites, and as much as possible, download applications only from trusted sources.
Trend Micro solutions that offer a multilayered defense system can help organizations protect their employees from these kinds of campaigns by detecting, scanning, and blocking malicious URLs.
Indicators of Compromise
This appendix contains the complete indicators for this attack.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE