CISA, NIST Says Use Cybersecurity Control Systems


Last July 2021, US President Joe Biden signed a memorandum on improving the US’s cybersecurity for critical infrastructure control systems. It establishes a voluntary initiative, encouraging collaboration between the federal government and the critical infrastructure community to improve cybersecurity control.
In line with this memorandum, the Department of Homeland Security (DHS) is instructed to lead the development of preliminary cross-sector control system cybersecurity performance goals and sector-specific performance goals within one year of the memorandum.
The Cybersecurity and Infrastructure Security Agency (CISA), together with the National Institute of Standards and Technology (NIST) performed a primary crosswalk of available control system resources, recommending practices that were produced by the US government and the private sector.
The crosswalk focused on various cybersecurity documents related to best practices and risk mitigation. These documents include CISA Cyber Essentials, NISTIR 8183, Rev 1, “Cybersecurity Framework Version 1.1 Manufacturing Profile, and CISA Pipeline Cyber Risk Mitigation.
Upon review, CISA and NIST have determined nine categories of recommended cybersecurity practices, using the categories as the foundation for preliminary control systems cybersecurity performance goals.
The nine categories are:
- Risk Management and Cybersecurity Governance, which aims to “identify and document cybersecurity control systems using established recommended practices”.
- Architecture and Design, which has the objective of integrating cybersecurity and resilience into system architecture in line with established best practices.
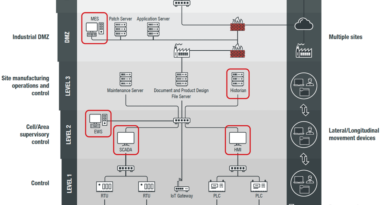
- Configuration and Change Management. This category aims to documents and control hardware and software inventory, system settings, configurations, and network traffic flows during the control system hardware and software lifecycles.
- Physical Security, which aims to limit physical access to systems, facilities, equipment, and other infrastructure assets to authorized users.
- System and Data Integrity, Availability, and Confidentiality. This category aims to protect the control system and its data against corruption, compromise, or loss.
- Continuous Monitoring and Vulnerability Management, which aims to implement and perform continuous monitoring of control systems cybersecurity threats and vulnerabilities.
- Training and Awareness aims to train personnel to have the fundamental knowledge and skills needed to determine control systems cybersecurity risks.
- Incident Response and Recovery. This category aims to implement and test control system response and recovery plans with clearly defined roles and responsibilities.
- Supply Chain Risk Management, which aims to identify risks associated with control system hardware, software, and manage services.
CISA explained that the nine categories’ goals outlined above are “foundational activities for effective risk management”, representing high-level cybersecurity best practices. The agency also said that these are not an exhaustive guide to all facets of an effective cybersecurity program.
As cyber threats and risks become more and more sophisticated and difficult to mitigate, it is important for critical infrastructure owners to future-proof their enterprises, minimizing operational risks and disturbances.
Apart from practices identified by CISA and NIST, owners and users should understand various practical countermeasures that should be considered during their planning and design phases.
Check out our “Best Practices for Securing Smart Factories: Three Steps to Keep Operations Running” to learn more about security issues, defense strategies, and the benefit of efficiently securing factories with minimal TCO.
Read More HERE