C’mon, if you say your device is ‘unhackable’, you’re just asking for it: Bitfi retracts edgy claim
Bitfi finally and reluctantly retracted its unhackable claim last night in the face of a new cold boot attack.
The John McAfee-backed hardware crypto-wallet firm got under the skins of security researchers by marketing its device as “unhackable” when it launched in July.
The $120 Wi-Fi-enabled Bitfi wallet is a hardware device that stores crypto-coins and other assets, protecting access to these devices through a passphrase. The passphrase is used to temporarily generate the private key needed to unlock a vault.
As previously reported, a hardware teardown exposed the device as essentially a cheap Android phone with the mobile connectivity components pulled out. The hardware is centred around Mediatek MT6580 system-on-chip, and came without a secure element that might have gone some way towards substantiating the bold claims made about the device.
Further investigation showed the unencrypted I2C protocol lines between the touchscreen and chipset can be eavesdropped on and (worse) it was possible to root the device and run arbitrary code. Security researchers made merry by demonstrating running the game Doom on the device.
None of this succeeded in mollifying Bitfi, still less John McAfee, who dismissed all these weaknesses as inconsequential. During a video debate, McAfee said he wanted to promote the wallet as a safe way for newbies to switch over from fiat currencies, arguing that “pissing off” the hacker community with claims the tech was unhackable were a great way to help promote the product.
The community was less than impressed. Bitfi won the PwnieAwards for “Lamest Vendor Response” at Black Hat earlier this month on the back of write-in nominations for an award it wasn’t initially nominated for.
The latest hack goes even further by demonstrating a cold boot attack, recovering passphrase and salt from memory.
on a completely unrelated note, here is a @Bitfi6 being cold boot attacked.
it turns out that rooting the device does not wipe RAM clean. who would have thought it!?
? i feel this music is very appropriate for @Bitfi6 ? pic.twitter.com/jpSnYBd9Vk
— Saleem “Unhackable” Rashid (@spudowiar) August 30, 2018
Ken Munro of Pen Test Partners told El Reg that the latest hack “shows that anyone with physical access can extract the keys required to steal coins”. Worse yet, “the keys can be recovered after a significant period of time. Even powering it off doesn’t wipe them,” he said, adding that the cold boot recover vid was done by a 16-year-old.
A variety of independent security researchers worked towards this goal but particular credit is due to Saleem Rashid (@spudowiar), Ryan Castellucci (@ryancdotorg) and Andrew Tierney (@cybergibbons).
Other contributors to the effort have included Ken Munro, Alan Woodward and others.
Professor Woodward of Surrey University confirmed Munro’s prognosis on the pwnage.
He told El Reg that the latest video “shows taking a Bitfi wallet that has been used to deal in Bitcoins, plugged into a machine via the USB and the secret passphrase and salt then recovered from the memory of the wallet. Once you have that you can steal the bitcoins as we know how the wallet generates the keys using that input.”
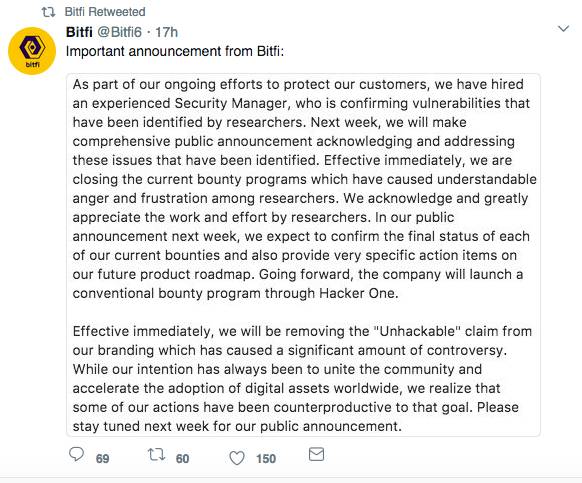
Bitfi responded to the latest blow by withdrawing its controversial $250,000 bounty and promising to drop the “unhackable” claim. It also stated that it wanted to work with bug bounty outfit Hacker One to replace its much criticised in-house offer.
Hacker One said Bitfi has yet to open a dialogue.
BitFi has not been in touch with us & there is no conversation going on. There are specific criteria and t&c for any company to qualify to run a program on our platform.
— Mårten Mickos (@martenmickos) August 31, 2018
Bounty bar
Security researchers cried sham over Bitfi’s initial bug bounty because it only covered one specific vector of attack, accessing coins on a device locked up with an unknown passphrase. This would have involved key recovery from a genuine, unaltered device. Excluded from the bounty was the possibility of modifying the device so that it records and sends the key to a malicious third party, among other possibilities.
The device failed to feature any anti-tampering measures so the possibility that units might be messed with before being returned to an intended mark isn’t implausible.
Although Bitfi seemingly wants to make peace with hackers who have criticised its bounty, it is not ready to admit its tech is vulnerable to its paying customers, as evidenced here. El Reg asked Bitfi to clarify its contradictory statement as to whether its device was vulnerable. We’ll update this story as and when more information comes to hand.
Critics, for their part, show no signs of relenting. “Bitfi can’t recall products as user keys persist in memory,” Ken Munro argued on Twitter, referencing the observations of team anti-Bitfi member @OverSoftN. ®
“This is NOT fixable by firmware, the Mediatek chipset simply was not built for this kind of device and provides features that can’t be disabled by FW,” @OverSoftN added.
Bootnote
The “unhackable” claim isn’t even original. Oracle infamously described its technology as unbreakable years ago only to be proved wrong by security researcher David Litchfield shortly afterwards.
Sponsored: Following Bottomline’s journey to the Hybrid Cloud
READ MORE HERE