Credential-Stuffing Attacks on Remote Windows Systems Took Off in 2021
Attackers have increasingly targeted remote Windows systems, fueling a surge in credential-stuffing attacks against systems running the remote desktop protocol (RDP), which jumped nearly ninefold in 2021, according to new data.
A report published by ESET this week shows password-based attacks hit European countries the hardest — particularly, Spain, Italy, France, and Germany — accounting for 116 billion of the 288 billion RDP attacks detected by ESET in 2021. While attackers mainly targeted RDP servers, they also sent billions of log-in attempts to database and file-sharing servers, according to the report.
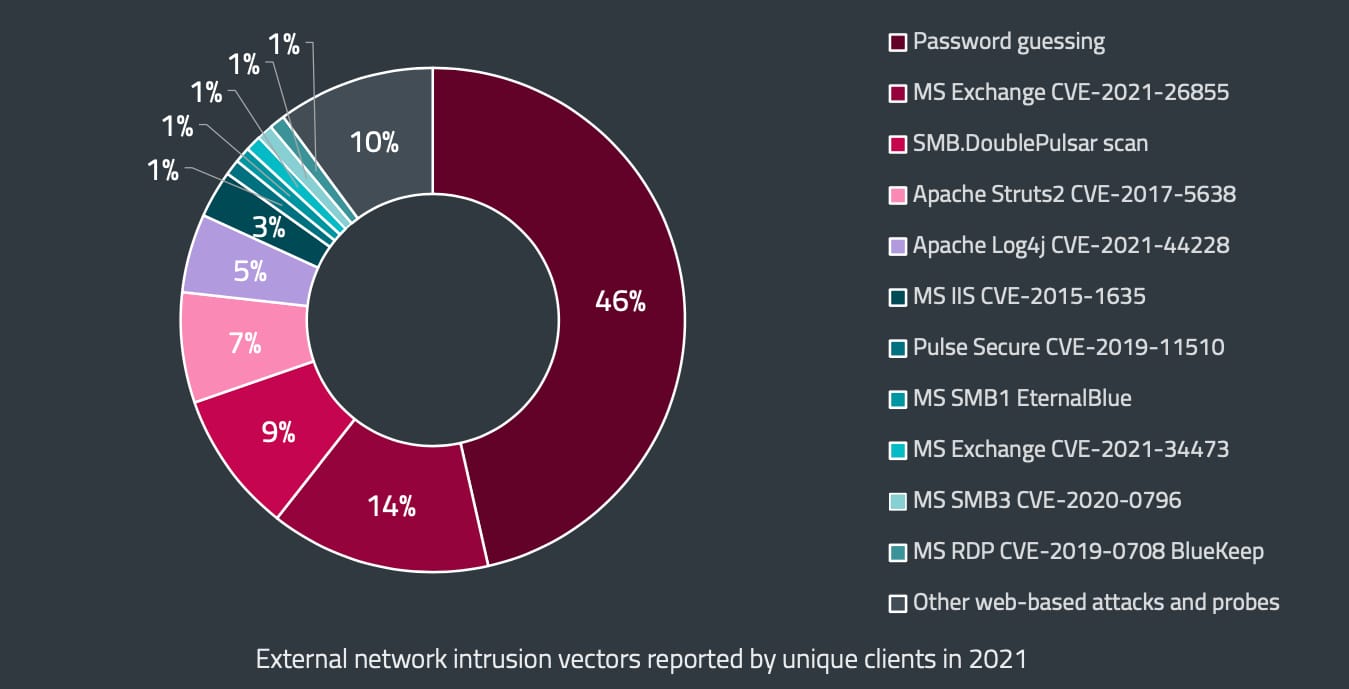
In total, credential-stuffing and other password-based attacks accounted for 46% of external network intrusion vectors.
The focus on such attacks means that companies need to ensure the proper setup and patching of any remotely accessible service and use of appropriate protective measures, such as strong passwords, multifactor authentication, and multiple layers of security products, says Ondrej Kubovič, a security research and awareness specialist at ESET.
“What changed dramatically is the scale of the password-guessing attacks,” he says. “There are groups out there — [whether] pen testers, internal security, criminals, or sophisticated threat actors — which are ramping up their password-guessing capacities and thus increasing the chance of hitting the right password-username combination and gaining the initial access.”
Remote Work Exposed Credentials
Attackers’ focus on logging into remote and cloud services using default or stolen credentials is unsurprising given that organizations’ employees moved to remote work, with many continuing to work from home.
The only good news, according to Kubovič, is that companies have improved the security around their credentials, remote services, and cloud applications.
“The number of unique devices reporting these staggering numbers of brute-force attacks stagnated throughout 2021 [and] even shrank a little in the third term,” he says. “That seems to tell us that organizations are not exposing new remotely accessible systems, yet those that are already reachable are bashed with growing force.”
Even though RDP attacks surged by a factor of nine, the volume of all threats detected in 2021 shrank by 16%, according to the report, which focuses on the latter four months of 2021 as well as summarizes information for the entire year. The volume of ransomware threats and Web threats each dropped by nearly half, while downloaders dropped by about 40%, according to the report. However, e-mail threats, such as phishing and Trojan horses, climbed 145%.
Phishing attacks used popular subjects, such as fake medication and reminders of full inboxes, inundated Japan, France, and the United States.
“Phishing, growing continuously since May, increasingly has been targeting users of popular online and cloud services — be it platforms used for remote work or various streaming and media providers,” stated Jiří Kropáč, head of ESET’s Threat Detection Labs, in the report. “In 2022, we will continue to face campaigns leveraging big brand names, as well as smaller opportunistic campaigns cropping up based on current trends.”
The report is based on data that ESET gathered from its telemetry, but the company does not always have a way to separate the benign scans from researchers and the malicious scans of attackers, says ESET researcher Mathieu Tartare. Often scans are part of an attacker’s reconnaissance and just serve to build a list of potentially vulnerable systems.
In some cases, however, such as scans against Microsoft Exchange servers using the popular ProxyShell exploit, the activity can be classified as malicious or benign.
“We [typically] have no way of knowing whether a researcher, pen tester, cybercrime group, or APT group is performing the scan,” he says. “However, if we consider exploitation attempts instead of scanning activities, in the case of ProxyShell, some blocked Web shells or first stages are used by specific APT groups, allowing us to attribute the attacks and exclude research or pen testing activities.”
Log4Shell
One concerning trend is the speed at which attackers adapt the latest vulnerabilities and exploits, says Kubovič. Attackers started using the Log4Shell exploit, for example, in a matter of weeks, which left many companies vulnerable.
“The one point that stood out in 2021 to me was how quickly cybercriminals and APT groups exploited recently published critical vulnerabilities,” he says. “So the one thing companies should focus on more in 2022 is to make sure they have visibility into every device and system in their networks and keep them all patched — very difficult, I know.”
Read More HERE
