Cyber Signals: Shifting tactics fuel surge in business email compromise
Today we released the fourth edition of Cyber Signals highlighting a surge in cybercriminal activity around business email compromise (BEC). Microsoft has observed a 38 percent increase in cybercrime as a service (CaaS) targeting business email between 2019 and 2022.1
Successful BEC attacks cost organizations hundreds of millions of dollars annually. In 2022, the FBI’s Recovery Asset Team (RAT) initiated the Financial Fraud Kill Chain (FFKC) on 2,838 BEC complaints involving domestic transactions with potential losses of more than USD590 million.2
BEC attacks stand apart in the cybercrime industry for their emphasis on social engineering and the art of deception. Between April 2022 and April 2023, Microsoft Threat Intelligence detected and investigated 35 million BEC attempts with an adjusted average of 156,000 attempts daily.
Cyber Signals
Microsoft’s Digital Crimes Unit has observed a 38 percent increase in cybercrime as a service targeting business email between 2019 and 2022.

Common BEC tactics
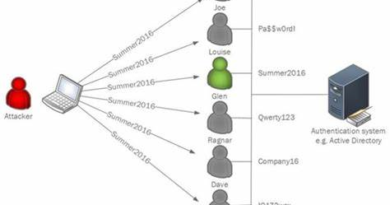
Threat actors’ BEC attempts can take many forms—including via phone calls, text messages, emails, or social media. Spoofing authentication request messages and impersonating individuals and companies are also common tactics.
Instead of exploiting vulnerabilities in unpatched devices, BEC operators seek to exploit the daily sea of email traffic and other messages to lure victims into providing financial information, or taking direct action like unknowingly sending funds to money mule accounts that help criminals perform fraudulent money transfers.
Unlike a “noisy” ransomware attack featuring disruptive extortion messages, BEC operators play a quiet confidence game using contrived deadlines and urgency to spur recipients who may be distracted or accustomed to these types of urgent requests. Instead of novel malware, BEC adversaries align their tactics to focus on tools improving the scale, plausibility, and in-box success rate of malicious messages.
Microsoft observes a significant trend in attackers’ use of platforms like BulletProftLink, a popular service for creating industrial-scale malicious mail campaigns, which sells an end-to-end service including templates, hosting, and automated services for BEC. Adversaries using this CaaS are also provided with IP addresses to help guide BEC targeting.
BulletProftLink’s decentralized gateway design, which includes Internet Computer blockchain nodes to host phishing and BEC sites, creates an even more sophisticated decentralized web offering that’s much harder to disrupt. Distributing these sites’ infrastructure across the complexity and evolving growth of public blockchains makes identifying them, and aligning takedown actions, more complex.
While there have been several high-profile attacks that take advantage of residential IP addresses, Microsoft shares law enforcement and other organizations’ concern that this trend can be rapidly scaled, making it difficult to detect activity with traditional alarms or notifications.
Although, threat actors have created specialized tools to facilitate BEC, including phishing kits and lists of verified email addresses targeting C-suite leaders, accounts payable leads, and other specific roles, there are methods that enterprises can employ to preempt attacks and mitigate risk.
BEC attacks offer a great example of why cyber risk needs to be addressed in a cross-functional way with IT, compliance, and cyber risk officers at the table alongside executives and leaders, finance employees, human resource managers, and others with access to employee records like social security numbers, tax statements, contact information, and schedules.
Recommendations to combat BEC
- Use a secure email solution: Today’s cloud platforms for email use AI capabilities like machine learning to enhance defenses, adding advanced phishing protection and suspicious forwarding detection. Cloud apps for email and productivity also offer the advantages of continuous, automatic software updates and centralized management of security policies.
- Secure Identities to prohibit lateral movement: Protecting identities is a key pillar to combating BEC. Control access to apps and data with Zero Trust and automated identity governance.
- Adopt a secure payment platform: Consider switching from emailed invoices to a system specifically designed to authenticate payments.
Learn more
Read the fourth edition of Cyber Signals today.
For more threat intelligence insights and guidance including past issues of Cyber Signals, visit Security Insider.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and Twitter (@MSFTSecurity) for the latest news and updates on cybersecurity.
End notes
1Cyber Signals, Microsoft.
2Internet Crime Complaint Center Releases 2022 Statistics, FBI.
READ MORE HERE