Cybercriminals See Allure in BEC Attacks Over Ransomware
While published trends in ransomware attacks have been contradictory — with some firms tracking more incidents and other fewer — business email compromise (BEC) attacks continue to have proven success against organizations.
BEC cases, as a share of all incident-response cases, more than doubled in the second quarter of the year, to 34% from 17% in the first quarter of 2022. That’s according to Arctic Wolf’s “1H 2022 Incident Response Insights” report, published on Sept. 29, which found that specific industries — including financial, insurance, business services, and law firms, as well as government agencies — experienced more than double their previous number of cases, the company said.
Overall, the number of BEC attacks encountered per email box has grown by 84% in the first half of 2022, according to data from cybersecurity firm Abnormal Security.
Meanwhile, so far this year, threat reports released by organizations have revealed contradictory trends for ransomware. Arctic Wolf and the Identity Theft Resource Center (ITRC) have seen drops in the number of successful ransomware attacks, while business customers seem to be encountering ransomware less often, according to security firm Trellix. At the same time, network security firm WatchGuard had a contrary take, noting that its detection of ransomware attacks skyrocketed 80% in the first quarter of 2022, compared with all of last year.
The Gleam of BEC Outshines Ransomware
The surging state of BEC landscape is unsurprising, says Daniel Thanos, vice president of Arctic Wolf Labs, because BEC attacks offer cybercriminals advantages over ransomware. Specifically, BEC gains do not rely on the value of cryptocurrency, and attacks are often more successful at escaping notice while in progress.
“Our research shows that threat actors are unfortunately very opportunistic,” he says.
For that reason, BEC — which uses social engineering and internal systems to steal funds from businesses — continues to be a stronger source of revenue for cybercriminals. In 2021, BEC attacks accounted for 35%, or $2.4 billion, of the $6.9 billion in potential losses tracked by the FBI’s Internet Crime Complaint Center (IC3), while ransomware remained a small fraction (0.7%) of the total.
In terms of revenue from individual attacks on businesses, the Arctic Wolf analysis noted that the median ransom for the first quarter was about $450,000, but the research team did not provide the average loss for victims of BEC attacks.
Shifting Financially Motivated Cyber Tactics
Abnormal Security found in its threat report earlier this year that that the vast majority of all cybercrime incidents (81%) involved external vulnerabilities in a few highly targeted products — namely, Microsoft’s Exchange server and VMware’s Horizon virtual-desktop software — as well as poorly configured remote services, such as Microsoft’s Remote Desktop Protocol (RDP).
Unpatched versions of Microsoft Exchange in particular are vulnerable to the ProxyShell exploit (and now the ProxyNotShell bugs), which uses three vulnerabilities to give attackers administrative access to an Exchange system. While Microsoft patched the issues more than a year ago, the company did not publicize the vulnerabilities until a few months later.
VMware Horizon is a popular virtual desktop and app product vulnerable to the Log4Shell attack that exploited the infamous Log4j 2.0 vulnerabilities.
Both avenues are fueling BEC campaigns specifically, researchers have noted.
In addition, many cyber gangs are using data or credentials stolen from businesses during ransomware attacks to fuel BEC campaigns.
“As organizations and employees become more aware of one tactic, threat actors will adjust their strategies in an effort to stay one step ahead of email security platforms and security awareness training,” Abnormal Security said earlier this year. “The changes noted in this research are just some of the indicators that those shifts are already occurring, and organizations should expect to see more in the future.”
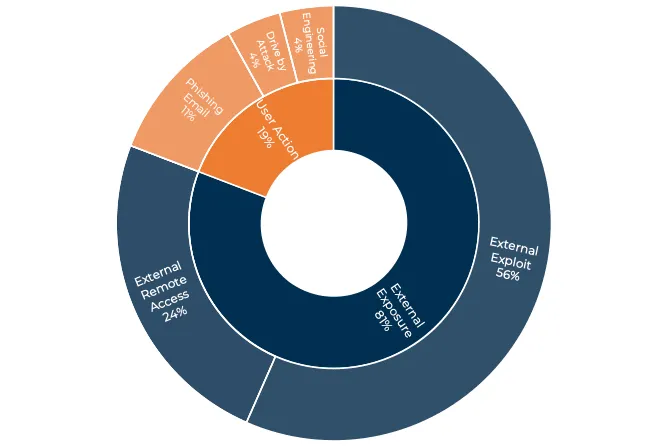
Social engineering is popular, too, as ever. While external attacks on vulnerabilities and misconfigurations are the most prevalent way that attackers gain access to systems, human users and their credentials continue to be a popular target in BEC attacks, says Arctic Wolf’s Thanos.
“BEC cases are often the result of social engineering, compared to ransomware cases, which are often caused by exploitation of unpatched vulnerabilities or remote access tools,” he says. “In our experience, threat actors are more likely to attack a company via remote exploit than dupe a human.
How to Avoid BEC Compromise
To avoid being a victim, basic security measures can go a long way, Arctic Wolf found. In fact, many companies falling prey to BEC attacks did not have security controls that potentially could have prevented damage, the company stated in its analysis.
For instance, the research found that 80% of those companies suffering a BEC incident had no multifactor authentication in place. In addition, other controls, such as network segmentation and security awareness training, could help prevent BEC attacks from being costly, even after the attacker successfully compromises an external system.
“Companies should strengthen their employee defenses through security training,” Thanos says, “but they also need to address the vulnerabilities that threat actors focus on.”
Read More HERE
