DarkSide Explained: The Ransomware Group Behind The Attack
When speaking to a cybersecurity expert concerning the Microsoft Exchange Server vulnerabilities several months ago and its impact on thousands of organizations worldwide, they asked, “What could possibly be worse this year?”
Perhaps the situation the United States found itself this week, with a major pipeline down due to ransomware, comes close.
Colonial Pipeline, which supplies 45% of the East Coast’s fuel, revealed a ransomware outbreak on the company’s systems which forced the suspension of operations and some IT systems last Friday, as previously reported by ZDNet.
Nearly a week following the May 7 attack, Colonial Pipeline restarted operations. The company said it will take “several days” for the pipeline’s deliveries to return to normal.
Data breaches and security incidents taking place at enterprise organizations are commonplace and hardly a week goes by when we don’t hear of yet another cyberattack on a well-known company — but when core, critical utilities and country infrastructure is involved, things take an even more serious turn.
Colonial Pipeline says that a system restart plan is being “developed” and some small lateral lines are back in service. However, it may be days before full functions are restored, and in the meantime, gasoline futures are rising and there is concern that some parts of the US may experience fuel shortages.
Gasoline futures jumped to their highest level in three years due to the cyberattack.
The USDOT Federal Motor Carrier Safety Administration (FMCSA) agency has issued a Regional Emergency Declaration to try and push back against the supply disruption through temporary exemptions for fuel transport on the road and the permissible hours that drivers are allowed to work for.
The FBI said on May 10 that the agency is working with Colonial to investigate the incident.
But who is responsible? According to the FBI, the DarkSide ransomware group.
“The FBI confirms that the Darkside ransomware is responsible for the compromise of the Colonial Pipeline networks,” the law enforcement agency says. “We continue to work with the company and our government partners on the investigation.”
DarkSide is a group believed to have been active since the summer of 2020. DarkSide’s malware is offered under a Ransomware-as-a-Service (RaaS) model, and once a system has been breached, ransomware payment demands can range from $200,000 to $2,000,000.
The group has previously been connected to “big game” hunting methods, in which large organizations are targeted — which would fit with the Colonial Pipeline incident.
Other cybercriminal organizations follow the same path, including Hades ransomware operators, which appear to specifically target companies with annual revenue of at least $1 billion.
DarkSide 2.0, the latest version of the ransomware, was recently released under an affiliates program. According to FireEye, affiliates are required to pay up to 25% of ransom payments under $500,000, and 10% of any successful extortion attempts over $5 million.
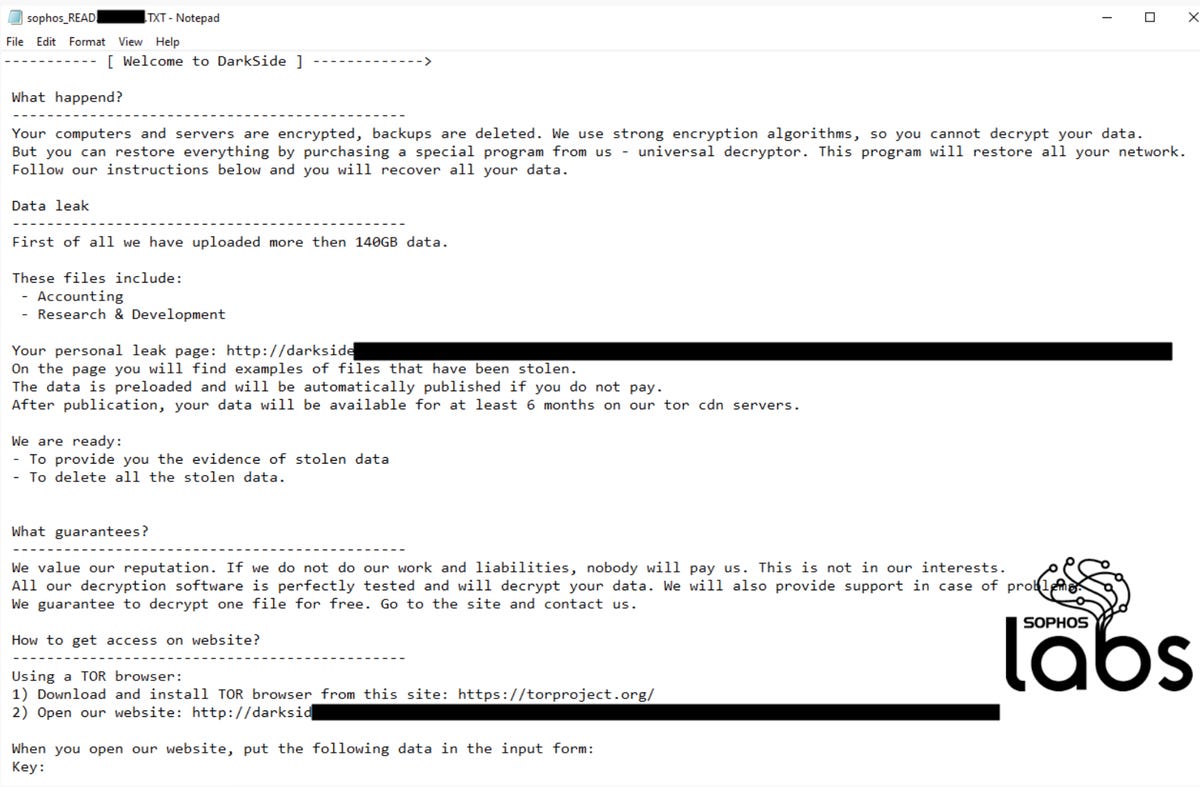
DarkSide also employs double-extortion tactics — joining the likes of Maze, Babuk, and Clop, among others — to pressure victims into paying up. At the time of a cyberattack, confidential information may be stolen and threats made to publish this data on a leak site if the victim refuses to give into blackmail.
The leak site operated by DarkSide has gone so far as to create a press corner for journalists and ‘recovery’ firms to reach them directly.
On the leak site, the ransomware group claims to have a code of conduct that prevents attacks against funeral services, hospitals, palliative care, nursing homes, and some companies involved in the distribution of the COVID-19 vaccine.
DarkSide also seems to have gone to some lengths to portray themselves as a kind of Robin Hood. As noted by Cybereason, the group claims that part of ransomware payments go to charity.
“Some of the money the companies have paid will go to charity,” DarkSide said in a forum post. “No matter how bad you think our work is, we are pleased to know that we helped change someone’s life.”
According to the researchers, however, this attempt to seem like the good guys has fallen flat, with $20,000 in stolen Bitcoin (BTC) donations rejected by charities due to their criminal sources.
See also: What is ransomware? Everything you need to know about one of the biggest menaces on the web
In direct contrast to the charity-giving group image, however, the cyberattack on Colonial Pipeline has caused intense disruption economically and socially — and this appears to be a situation the ransomware operators want to distance themselves from.
“We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined government and look for other our motives,” DarkSide said in a statement dated May 10. “Our goal is to make money, and not creating problems for society. We [will] introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
And yet, the extortion continues, with countdowns on the leak site showing the next batch of dumped, stolen files belonging to other organizations continue to be released.
It should also be noted that when victim companies refuse to pay, DarkSide is willing to share insider information ahead of the publication of stolen data.
“If the company refuses to pay, we are ready to provide information before the publication, so that it would be possible to earn in the reduction price of shares,” the group says. “Write to us in “Contact Us” and we will provide you with detailed information.”
While cybercriminals like DarkSide profit, companies like Colonial Pipeline become collateral damage — and this organization is unlikely to be the final victim on the list.
On May 10, Colonial Pipeline said the firm must take a “phased approach” in restoring supply and it is hoped that operations can fully resume by the end of the week.
“While this situation remains fluid and continues to evolve, the Colonial operations team is executing a plan that involves an incremental process that will facilitate a return to service in a phased approach. This plan is based on a number of factors with safety and compliance driving our operational decisions, and the goal of substantially restoring operational service by the end of the week. The company will provide updates as restoration efforts progress.”
Update 12/5 12.02 BST: FireEye has published research on five clusters of activity linked to DarkSide. Three of the groups are tracked as UNC2628, UNC2659, and UNC2465. Sophos, too, has provided a detailed look at a typical DarkSide ransomware attack chain.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
READ MORE HERE