Deadline Looms For Alleged LockBit Extortion Over Feds Of 33TB Of Data
Less than 24 hours remain on a threat by the LockBit ransomware group to release 33 terabytes of government data tied to an alleged breach of the Federal Reserve Board. While there has been no confirmation of the breach and the Fed remains mum, the deadline of June 25 looms.
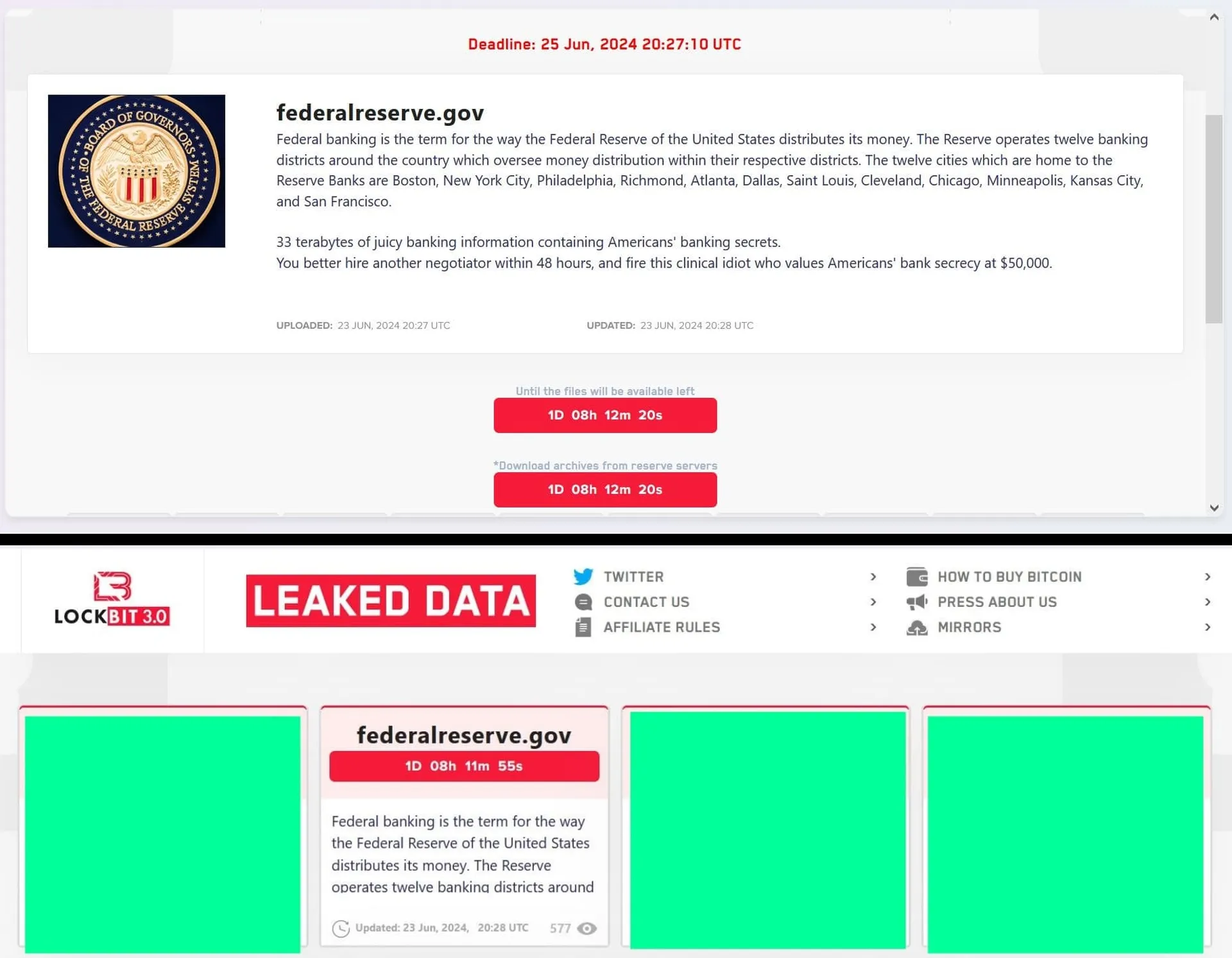
Multiple reports came out June 24 that the notorious LockBit group was negotiating with the Federal Reserve Board over a ransom payment in exchange for not making public 33 terabytes of government data.
LockBit, with believed ties to Russia, has attacked many types of organizations, including small businesses, multinational corporations, hospitals, schools, nonprofit organizations, critical infrastructure, and government and law-enforcement agencies. Some prominent targets include the Thales Group, the Toronto Hospital for Sick Children, and the U.S. subsidiary of the Chinese state-owned Industrial and Commercial Bank of China.
If reports are true that LockBit is extorting the U.S. Federal Reserve tensions are sure to be escalating between Russia and the United States. Late last week, the Biden administration banned the use of Kaspersky anti-virus software and then followed up by placing 12 Kaspersky execs on the Specially Designated National List. Also on May 7, the Treasury Department indicted Dimitry Yuryevich Khoroshev, claiming he was the mastermind behind LockBit.
Ratcheting Up Cyber Tension
Morgan Wright, chief security advisor to SentinelOne, and an SC Media columnist, said today’s new is in line with other Russian attacks, which often are in retaliation for perceived or actual actions. Wright pointed out that the BlackEnergy attack on December 23, 2015, was retaliation for a vote taken by Ukraine to join NATO, which happened on December 23, 2014.
“33 terabytes of juicy banking information containing Americans’ banking secrets. You better hire another negotiator within 48 hours, and fire this clinical idiot who values Americans’ bank secrecy at $50,000,” LockBit posted on its dark web site.
Wright underscored that if LockBit didn’t actually hack the Fed, then a provably false statement like this would hurt the criminal group’s credibility.
Despite having its infrastructure seized and the alleged leader Khoroshev exposed by law enforcement authorities, the group seems to have continued its activities, said Agnidipta Sarkar, vice president and CISO Advisory at ColorTokens.
“We will need to wait for further updates on this matter,” said Sarkar. “If this is indeed true, regulators will need to intervene to ensure that (potentially impacted) businesses are breach-ready, and banks will need to prioritize foundational cybersecurity by isolating critical operations from other systems.”
READ MORE HERE
