Defending the power grid against supply chain attacks—Part 1: The risk defined

Most people don’t think about electricity. If the internet works, their food is refrigerated, and their debit card is approved, why should they? Its ubiquity and reliability render it invisible—a bit of magic that powers much of modern life. That is, until a large storm passes through. Localized outages can be quite disruptive to those impacted, and the utility industry has learned to respond rapidly and effectively to these events. But what happens if service interruptions become more unpredictable and affect large geographical regions with huge populations?
This is a risk that utilities and their supply chain must continue to address. Nation state actors and other adversaries have demonstrated that they possess the ambition and the skills necessary to launch cyberattacks that could cause widescale and continuous power outages. Whether your organization is a utility or a supplier of the industry, you may be vulnerable.
This blog series, “Defending the power grid against supply chain attacks,” analyzes how these attacks are conducted and the steps utilities, device manufacturers, and software providers can take to better secure critical infrastructure.
Why it matters
Modern warfare is no longer conducted exclusively on the battlefield. Nation-state actors also deploy sophisticated cybercampaigns to disrupt daily life or sow confusion. The power grid is one such target. The financial system, sewer and water lines, transportation networks, computers, cellphones, kitchen appliances, and more run on electricity. Several hours of disrupted power can grind economic activity to a halt in the affected areas. An outage of days or weeks could incite greater unrest.
Accelerated adoption of the Internet of Things (IoT) compounds the risk. IoT innovations allow the utility industry to harness the power of the internet, data, and artificial intelligence to optimize its operations and deliver energy more efficiently and reliably to its customers. But these devices can introduce new vulnerabilities. Existing sensors often don’t have security or centralized management built into them. Some devices are so small, it’s difficult to place traditional protections on them. Manufacturers, who feel pressured to deliver solutions quickly, may fail to incorporate critical security controls and safeguards in their products. Bad actors are skilled at uncovering these weaknesses and exploiting them.
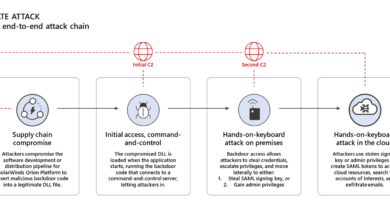
How attacks are executed
A typical cyberattack includes lengthy reconnaissance to uncover all the vendors that serve a utility and their vulnerabilities. Bad actors even go after suppliers who exist outside the software and hardware space but have vital access. A few examples:
- Software libraries and frameworks—Modern software relies on open source and industry libraries and frameworks to reduce time to market and take advantage of pre-tested solutions. This is fertile ground for hackers to insert malware that wreaks havoc once the software reaches its destination.
- Digitally signed software—Much software is digitally signed by the vendor to prove its legitimacy. Hackers who break into servers may be able to infect software before it’s digitally signed or spoof the signature after altering the software.
- Software update servers—Bad actors hack into the servers that distribute software updates. This can be very effective since many applications auto-update.
- Hardware interdiction—While hardware and parts are in-transit, a cybercriminal intercepts the shipment and inserts malicious code in the hardware or firmware.
- Hardware seeding—Cybercriminals infect IoT devices, such as phones, cameras, sensors, drones and USB drives, with malware inserted on the manufacturing floor.
- Onsite vendors—Companies that come on site to provide services may not be as security focused as software and hardware companies. Attackers exploit this vulnerability and then use the relationship to gain access to the ultimate target.
- Remote servicing vendors—Bad actors also attack the companies who provide remote support to the systems at the target organization.
Looking ahead
The next two installments of the Defending the power grid against supply chain attacks series will offer practical advice for both the utilities and their vendors.
Stay tuned for:
- Part 2: Secure the hardware and software used by utilities
- Part 3: Risk management strategies for the utilities industry
In the meantime, whether you are a utility or one its suppliers, you can begin to address these risks by inventorying your vendors. Where do you buy software, what processes do you use to select software libraries? Who builds your hardware? Where do your hardware manufacturers source parts?
Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
READ MORE HERE