Deploy Jenkins Serverless-ly in Azure Services Solution Engineer
Serverless Security
Get a how-to guide on deploying Jenkins serverless-ly and securely utilizing Microsoft® Azure®-hosted services with Azure Container Instances, Azure Files, and Azure Bastion.
Jenkins is great! Easy to setup, and great plugin support! Know what’s even greater? Choosing to run Jenkins as a container image inside Azure Container Instances! You know why? No servers to mess with! Serverless implementation for the win! Know what’s still even greater? Choosing to persist your Jenkins configuration with Azure Files. Yep, that’s right, no servers being shown today!
Today, I was doing just that and experimenting with those services.
Let’s start our fun today with setting up Jenkins in Azure Container Instances. To do this, I went ahead and pulled the official Jenkins Container Image.
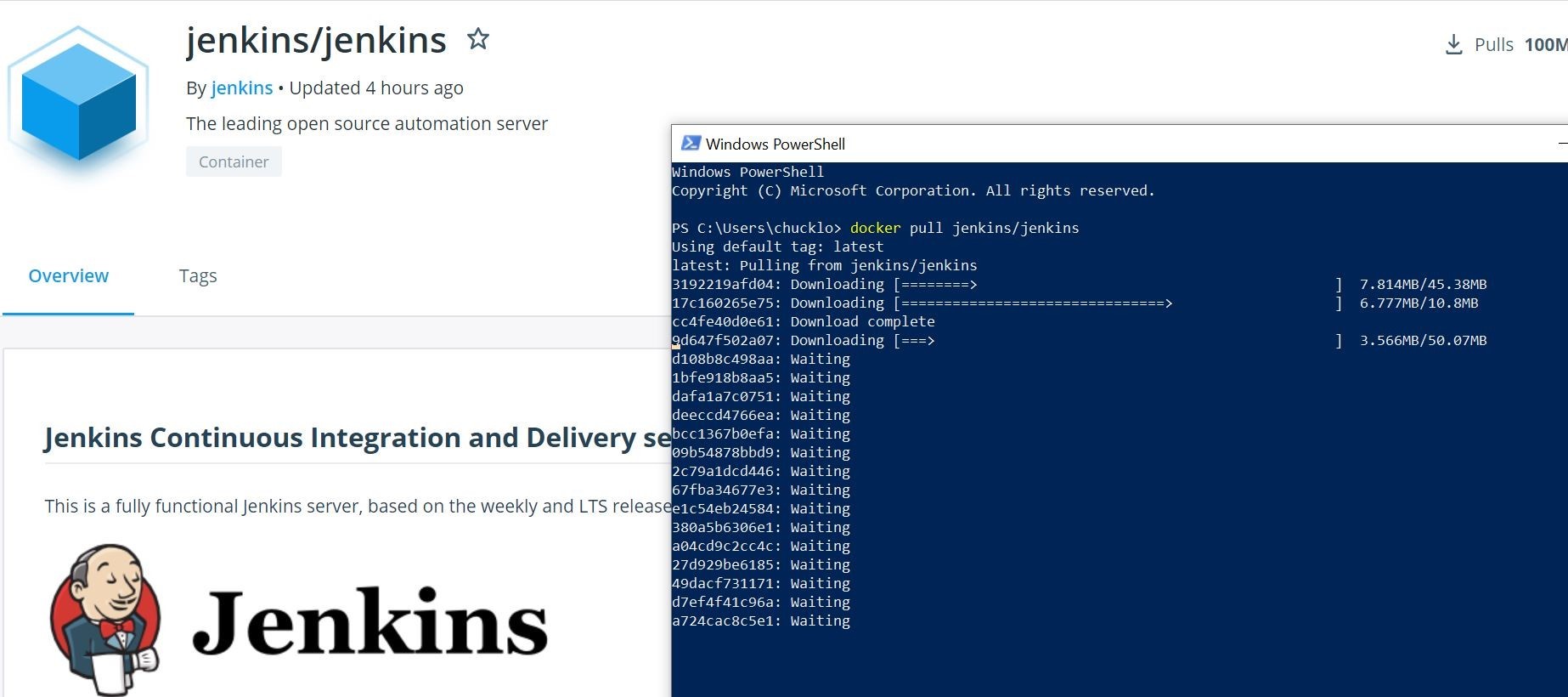
Ok, now that we have that image pulled, let’s go ahead and push it into our Azure Container Registry.
Alrighty then! That seems simple enough! So, let’s go ahead and fire that container image bad boy up in Azure Container Instances.
I am going to accomplish this programmatically with Azure CLI and add persistent serverless file storage to the container utilizing Azure Files! That way I do not lose my Jenkins configuration! Think like a docker volume, but I don’t need an underlying host or server to host it on!
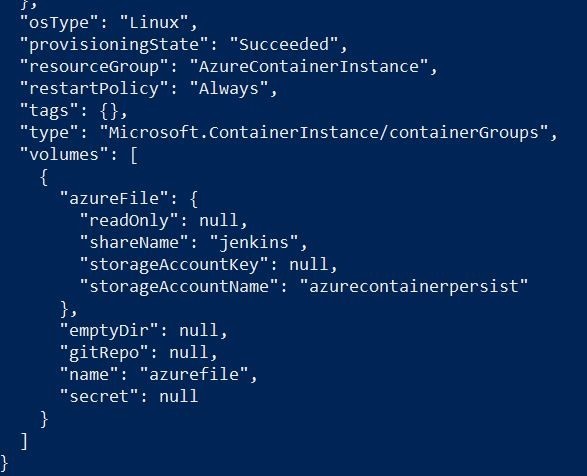
Below is the one liner command to bring it all together! First, we create the Azure Container Instance, and pull the corresponding jenkins/jenkins tagged image that I already pushed up to my Azure Container Registry. This also adds my storage account with associated server less Azure Files share, and mounts it seamlessly to the container! Off to the bonus round indeed!
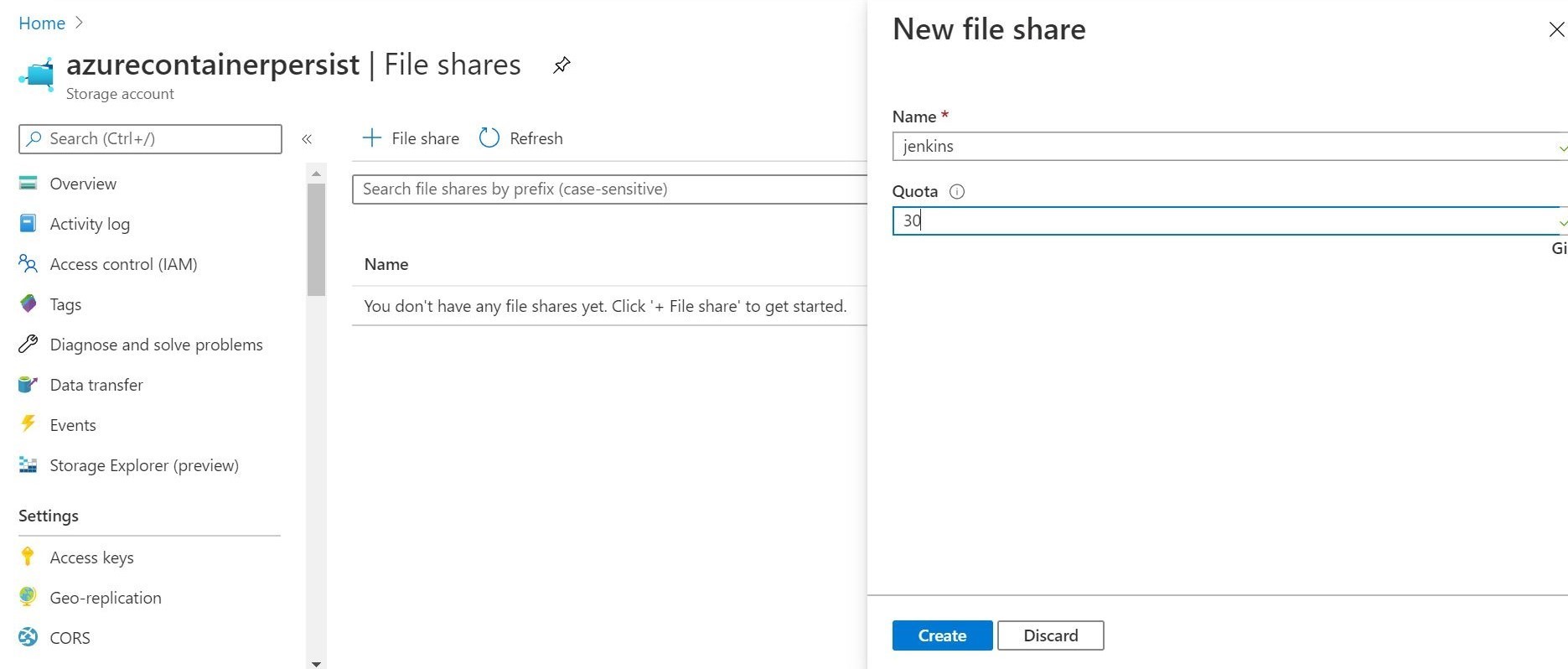
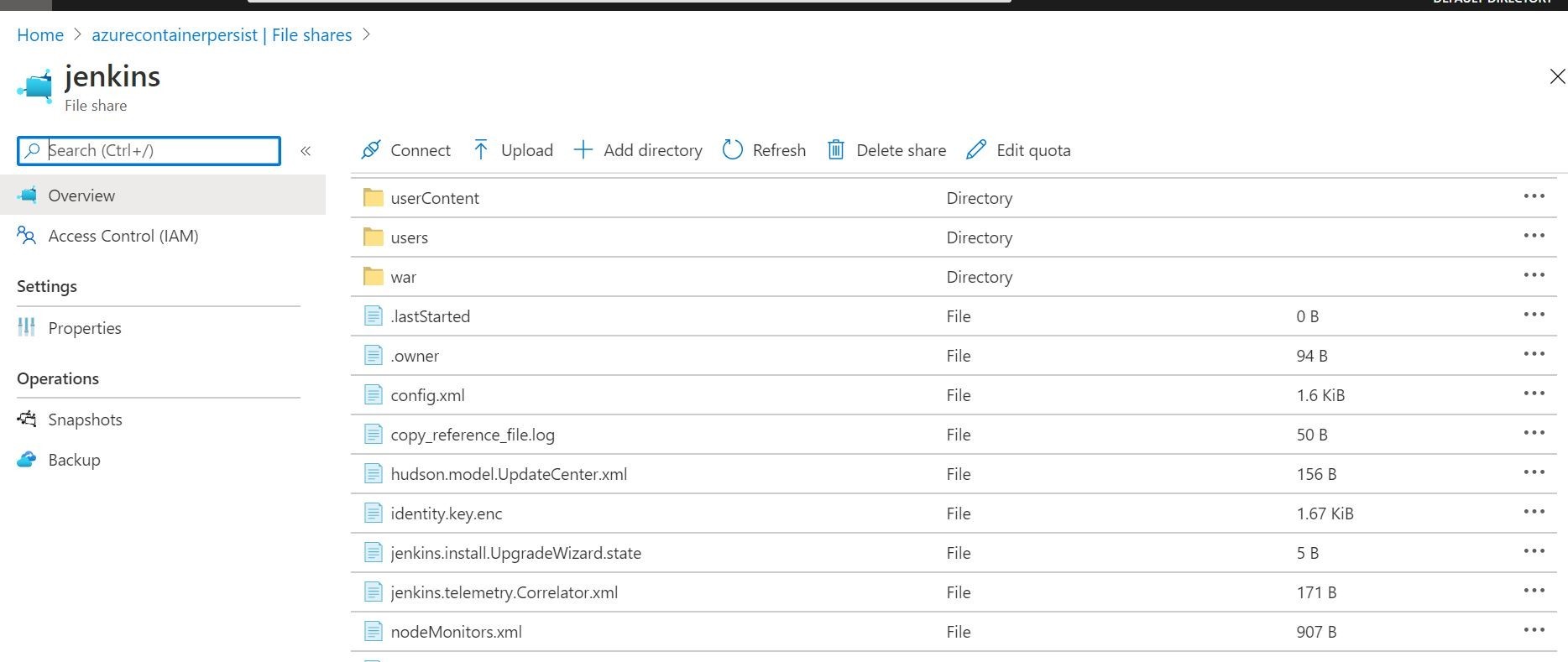
To create an Azure Files share referenced in the above Azure CLI, you can do that in an Azure Storage account with the Azure Files option. This is illustrated below. You can see where I setup the share in the storage account, and set a size quota. Once our deployment completes above, we will re-visit this file share. We will see where the Jenkins configuration has written out the configuration files and folders. Pretty cool! Serverless file storage from Microsoft Azure!
Once you get output similar to below in Microsoft Powershell, you should be able to logon to the Azure Portal to check some things out. That means that the Azure Container Instances deployment has been completed.
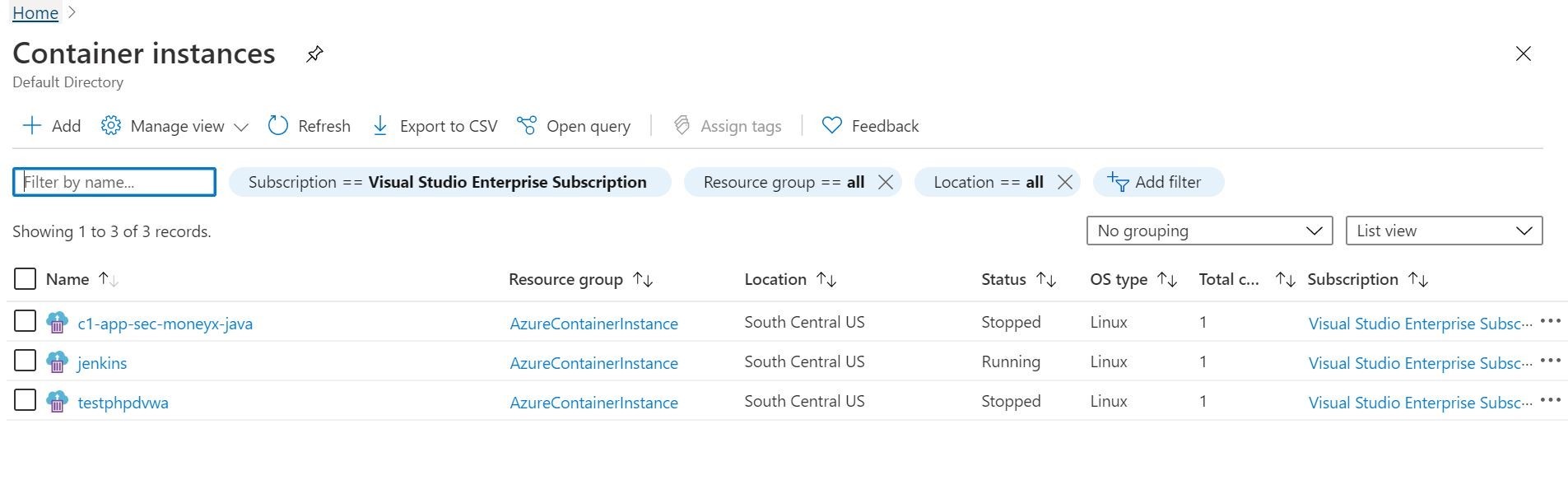
In the Azure portal, we can see under Azure Container Instances service our resulting Jenkins deployment. The status is currently running! That’s a good thing, right? Let’s select it and check out some details.
Here on the details screen, you can tail the container logs and get the Jenkins initial password and IP address that was outputted during deployment. You can also have remote console access directly to the container here shown below. You can also get remote console access via Microsoft Powershell by running the following command! Very cool, indeed!
We can also check in on our Azure Files Share, and now see the results of the install. As we configure pipelines, plugins, and configuration settings they will be auto magically auto saved to the file share acting as a persistent docker volume!
Now, what I did not show you. For security and testing purposes, I am securely accessing the Jenkins container from Azure Bastion. I am not running this test Jenkins container instance to the public internet at this time, as you can see above with the Azure CLI installation command. I only receive an private IP address. Azure Bastion allows me to securely access resources in my Azure Subscription without exposing public ports through the NSGs etc, and I can access directly from my web browser. Huzzah! Think Bastion as a Service! Deploys right in your virtual network! Pretty nifty! But, wait! There’s more! We have Jenkins to check out! I almost forgot!
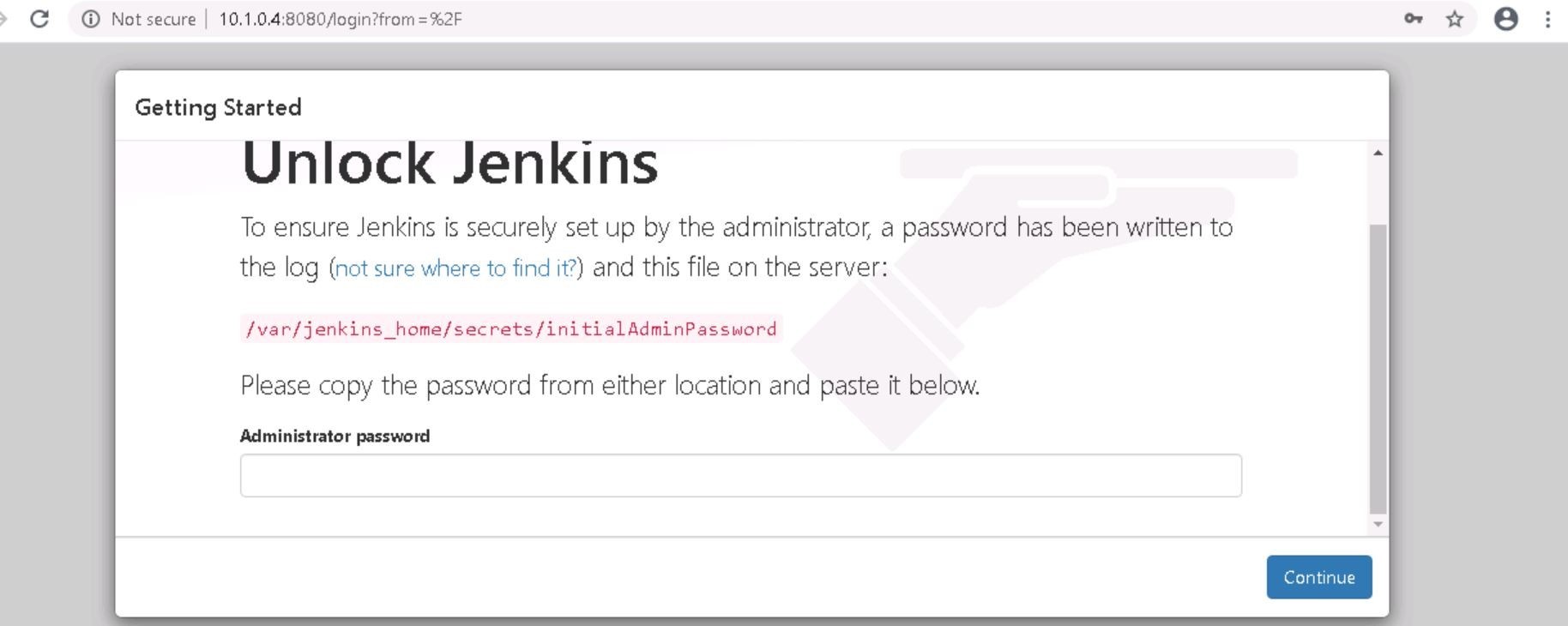
Ok, here is my Jenkins install accessed privately from behind my Azure Bastion.
After setting up some default admin credentials, and installing some plugins (namely Blue Ocean) the screen should be pretty similar to below.
Alrighty, so now I need a JenkinsFile build to put in my pipeline. I am going to quickly clone an new repository from my GitHub account.
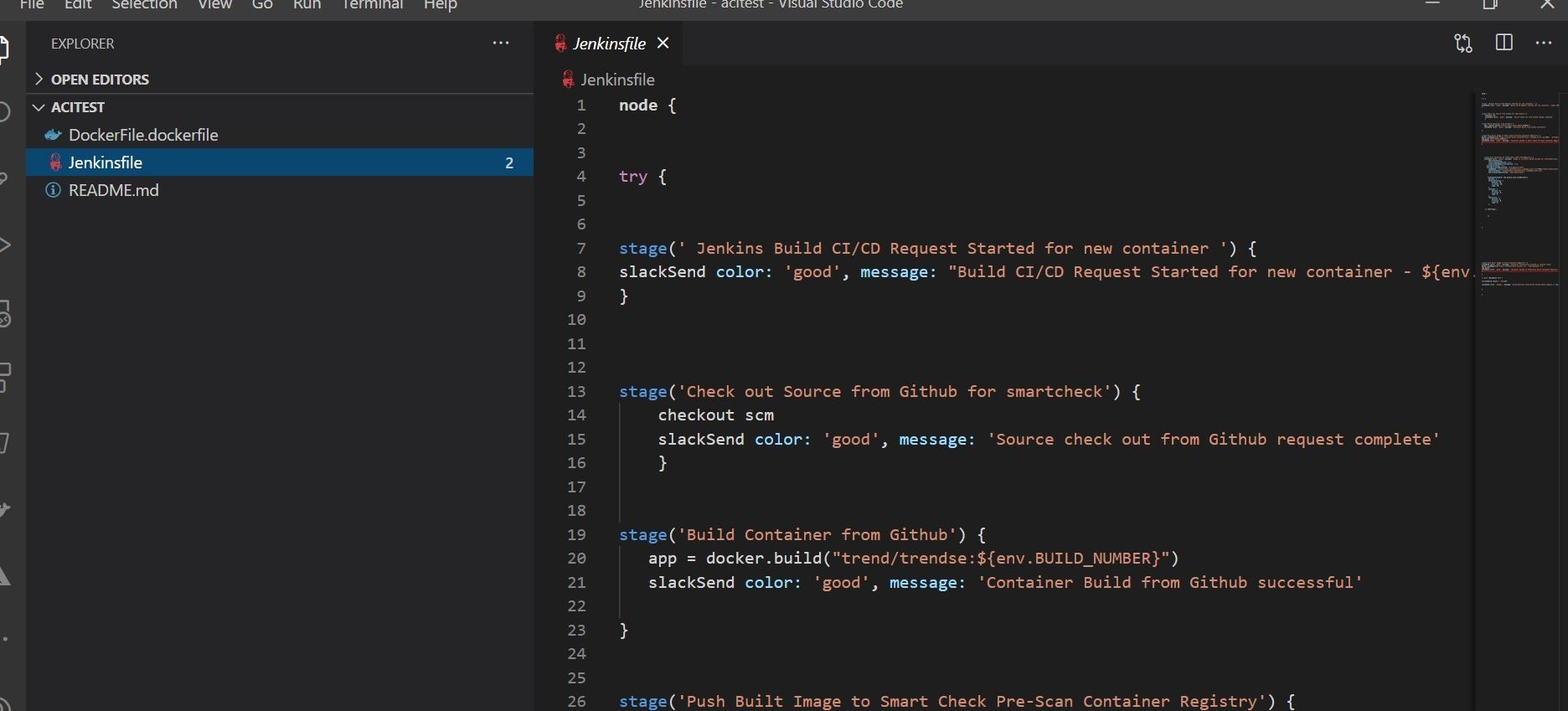
Ok, next you are going to want to configure the pipeline accordingly. This is an example JenkinsFile pipeline that I created that’s checked into GitHub source control to be used the pipeline configuration. I commit and push that back to GitHub.
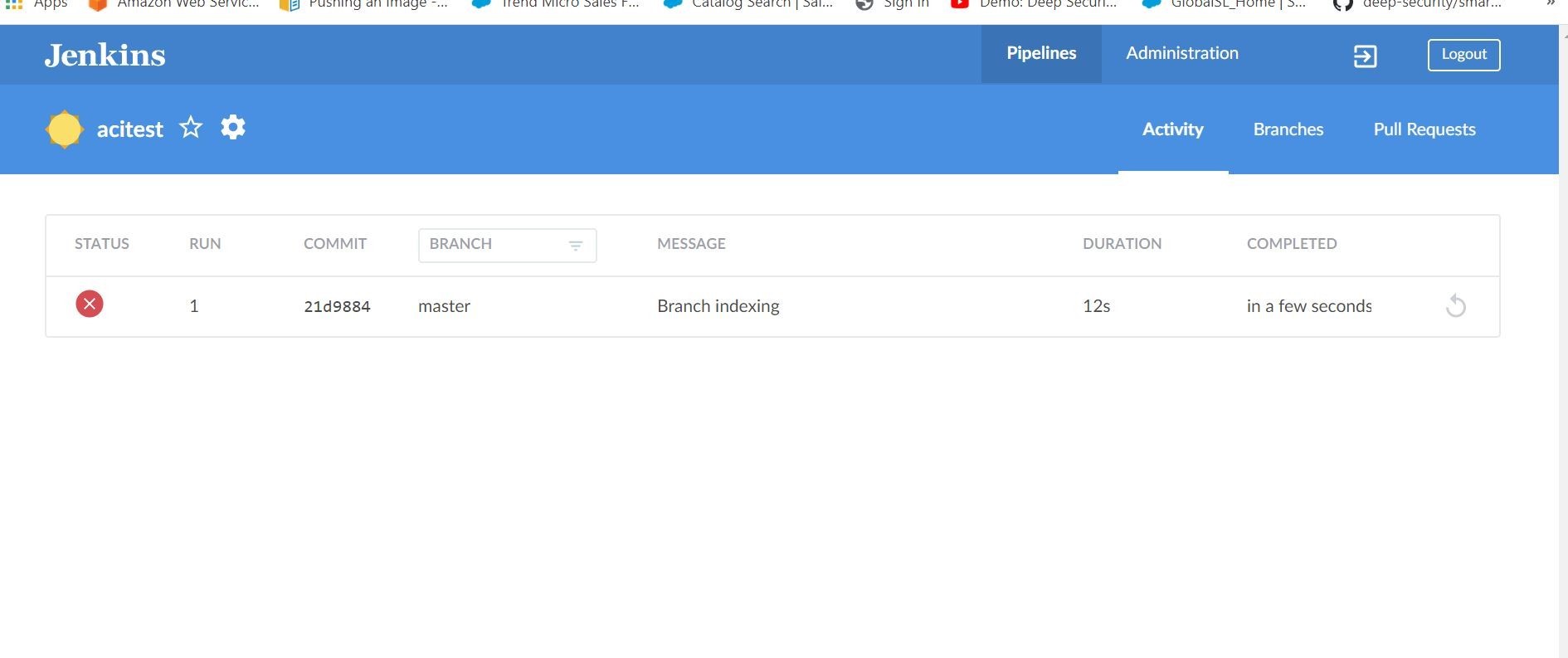
Ok, back to Jenkins. Let’s go ahead and configure a test Jenkins Pipeline.
The easiest way to do that with your GitHub source control is with the Blue Ocean Plugin.
Go ahead and launch Blue Ocean plugin from the left hand side of your Jenkins install.
You will then have a wizard/guided install on how to integrate Jenkins with your GitHub repo to create a pipeline from a respective JenkinsFile!
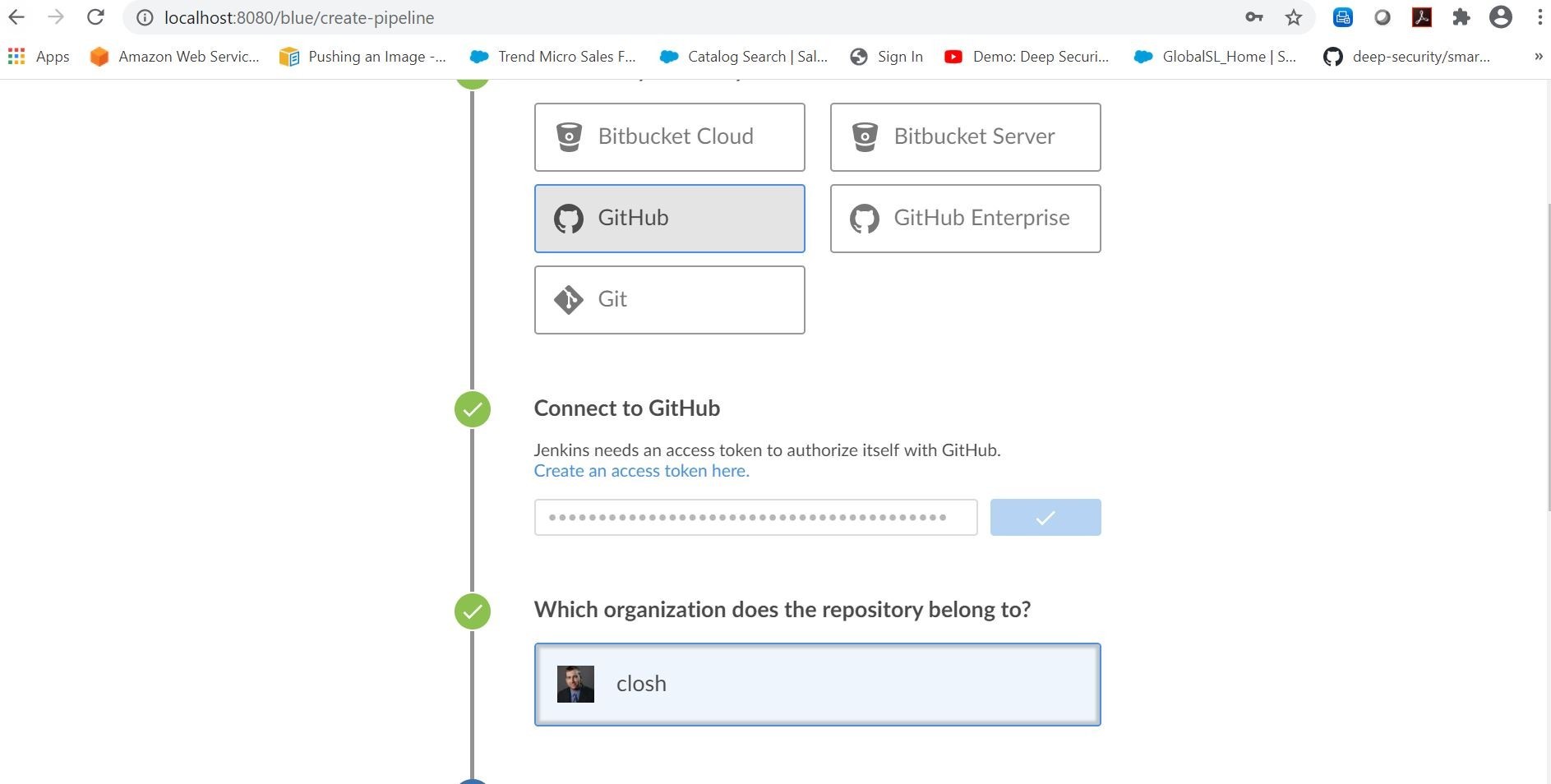
This section is where you will generate an access token in your GitHub account. That way you can access your GitHub account directly in Jenkins.
Once that integration is complete then it can build your pipeline as an example below.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE