Earth Preta Mixes Legitimate and Malicious Components to Sidestep Detection

Summary
- Researchers from Trend Micro’s Threat Hunting team discovered that Earth Preta, also known as Mustang Panda, uses the Microsoft Application Virtualization Injector to inject payloads into waitfor.exe whenever an ESET antivirus application is detected.
- They utilize Setup Factory to drop and execute the payloads for persistence and to avoid detection.
- The attack involves dropping multiple files, including legitimate executables and malicious components, and deploying a decoy PDF to distract the victim.
- Earth Preta’s malware, a variant of the TONESHELL backdoor, is sideloaded with a legitimate Electronic Arts application and communicates with a command-and-control server for data exfiltration.
Trend Micro’s Threat Hunting team has come across a new technique employed by Earth Preta, also known as Mustang Panda. Earth Preta’s attacks have been known to focus on the Asia-Pacific region: More recently, one campaign used a variant of the DOPLUGS malware to target Taiwan, Vietnam, Malaysia, among other countries. The group, which favors phishing in their campaigns and tends to target government entities, has had over 200 victims since 2022.
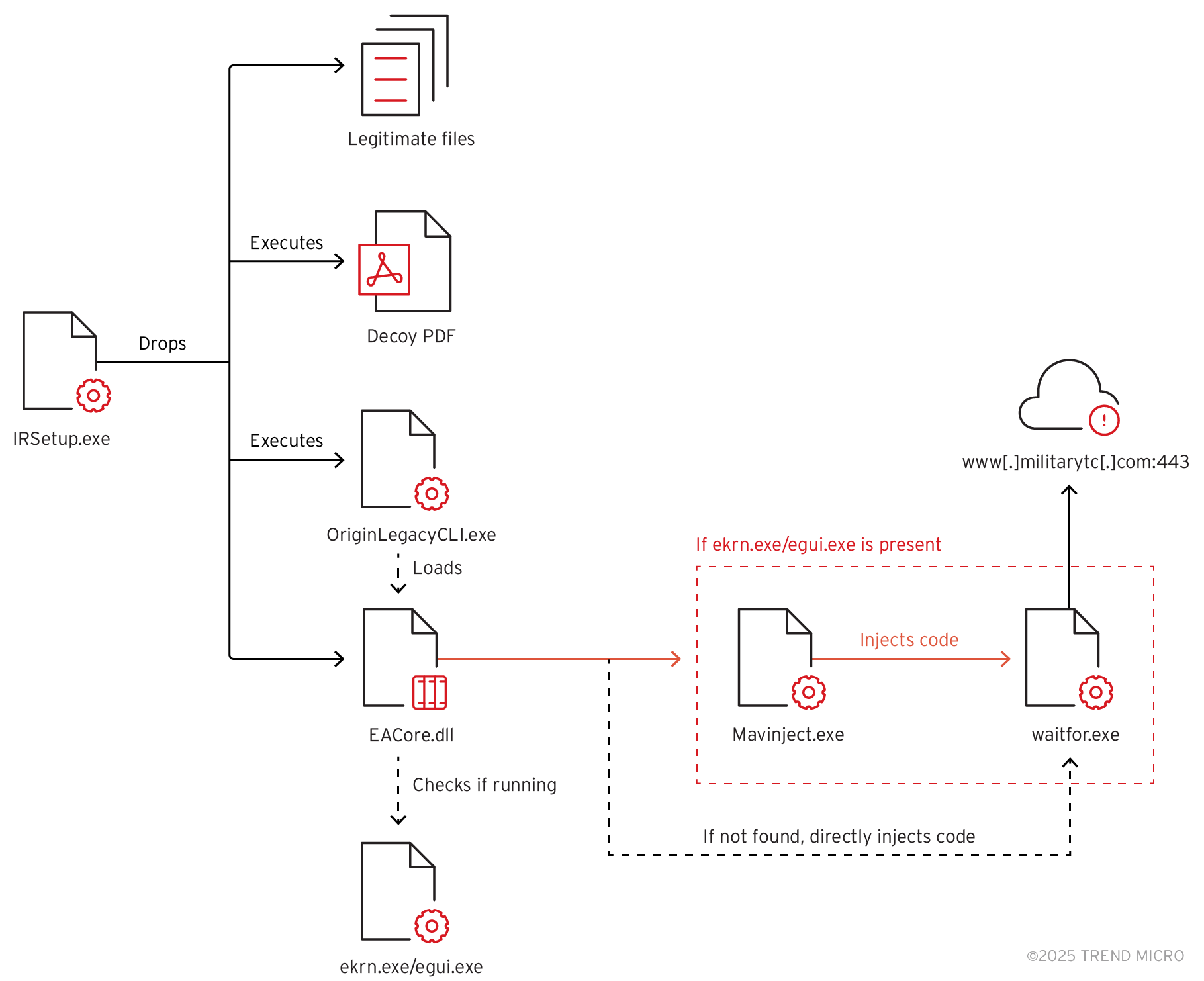
This advanced persistent threat (APT) group has been observed leveraging a Windows utility that’s able to inject code into external processes called the Microsoft Application Virtualization Injector (MAVInject.exe). This injects Earth Preta’s payload into a Windows utility that’s used to sending or waiting for signals between networked computers., waitfor.exe, when an ESET antivirus application is detected running. Additionally, Earth Preta utilizes Setup Factory, an installer builder for Windows software, to drop and execute the payload; this enables them to evade detection and maintain persistence in compromised systems.
Detailed analysis
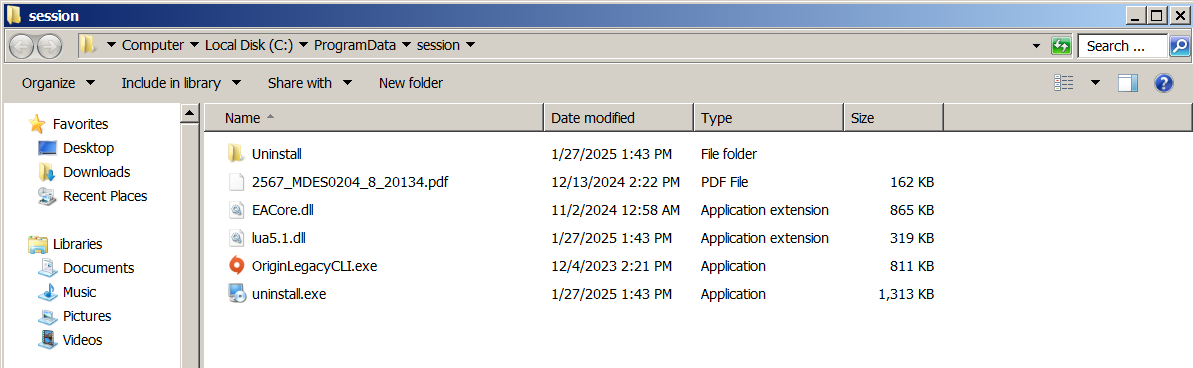
In Earth Preta’s attack chain, the first malicious file, IRSetup.exe, is used to drop multiple files into the ProgramData/session directory (Figure 1). These files include a combination of legitimate executables and malicious components (Figure 2).
A decoy PDF designed to target Thailand-based users is also executed, likely to distract the victim while the malicious payload is deployed in the background (Figure 3). The fraudulent document asks for the reader’s cooperation in creating a whitelist of phone numbers to aid in the development of an anti-crime platform, allegedly a project supported by multiple government agencies.
This technique aligns with Earth Preta’s previous campaigns, in which they used spear-phishing emails to target victims and executed a decoy PDF to divert attention while the malicious payload was deployed in the background.

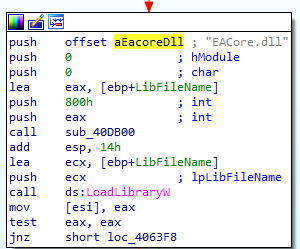
The dropper malware then executes OriginLegacyCLI.exe, a legitimate Electronic Arts (EA) application, to sideload EACore.dll, a modified variant of the TONESHELL backdoor used by Earth Preta, shown in Figure 4.
TONESHELL backdoor – EACore.dll
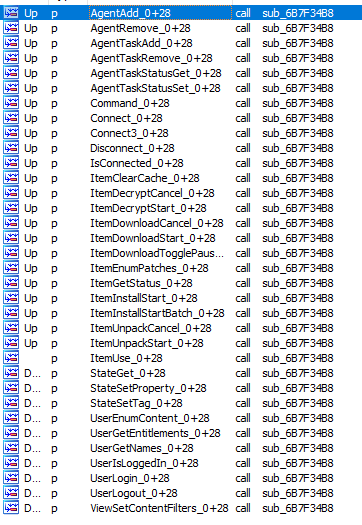
EACore.dll contains multiple export functions, as shown below in Figure 5, but all of them point to the same malicious function.
One of the functions checks if either ekrn.exe or egui.exe, both associated with ESET antivirus applications, are running on the machine (Figure 6). If either process is detected, the malware registers EACore.dll using regsvr32.exe to execute the DLLRegisterServer function (Figure 7).
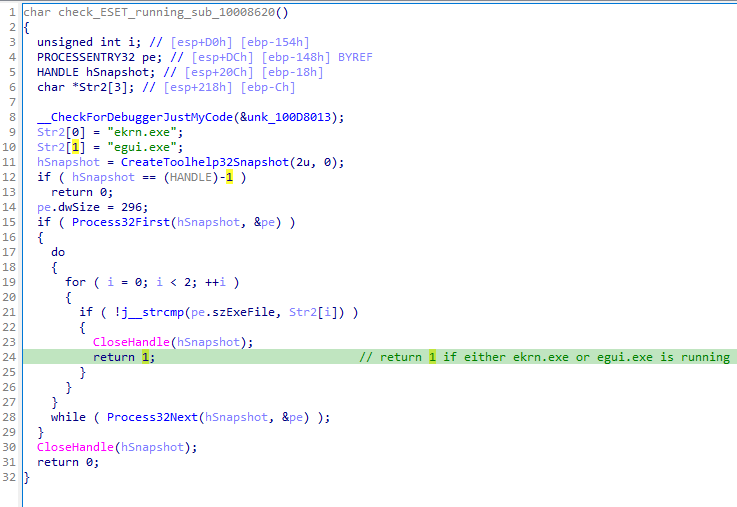
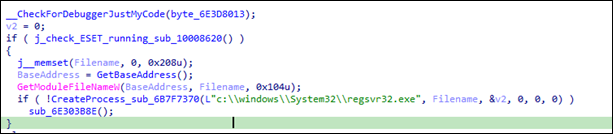
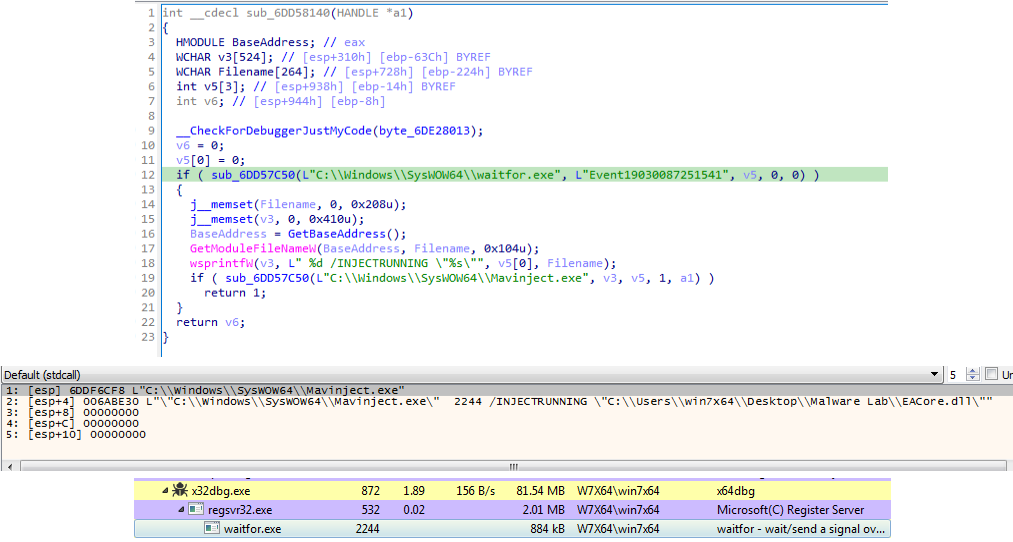
The DLLRegisterServer export will then execute waitfor.exe. MAVInject.exe, which is capable of proxy execution of malicious code by injecting to a running process as a means of bypassing ESET detection, is then used to inject the malicious code into it (Figure 8) via the following command:
Mavinject.exe <Target PID> /INJECTRUNNING <Malicious DLL>
It is possible that Earth Preta used MAVInject.exe after testing the execution of their attack on machines that used ESET software.
Exception handler
The malware also implements an exception handler (Figure 9) that activates when ESET applications are not found, allowing it to proceed with its payload. Instead of injecting the malicious code via MAVInject.exe, it directly injects its code into waitfor.exe using WriteProcessMemory and CreateRemoteThreadEx APIs (Figure 10).
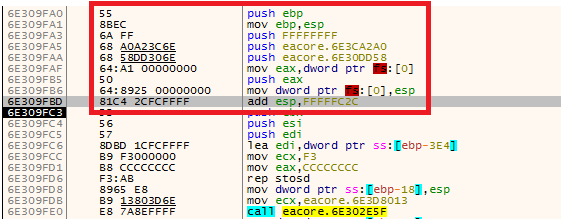
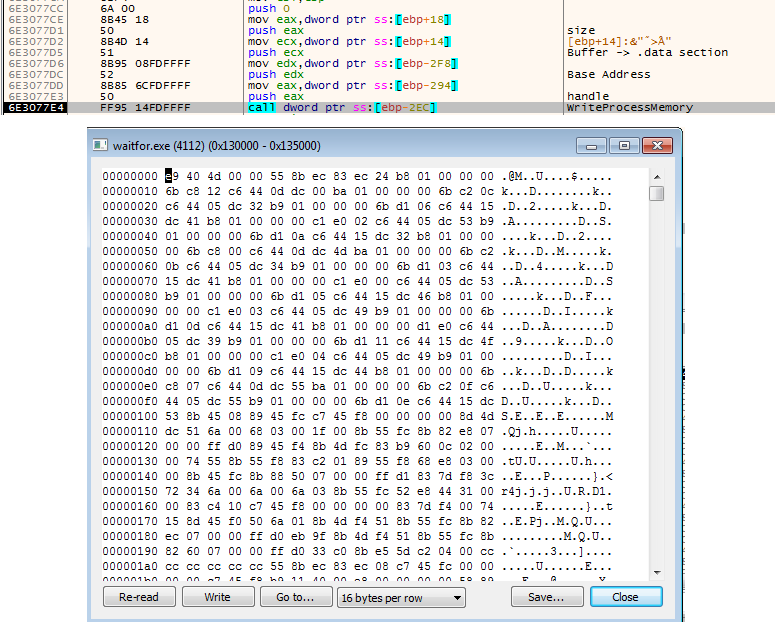
C&C communication
The malware decrypts the shellcode stored in the .data section (Figure 11), where it will contain the functions to communicate with its C&C server, www[.]militarytc[.]com:443 (Figure 12).
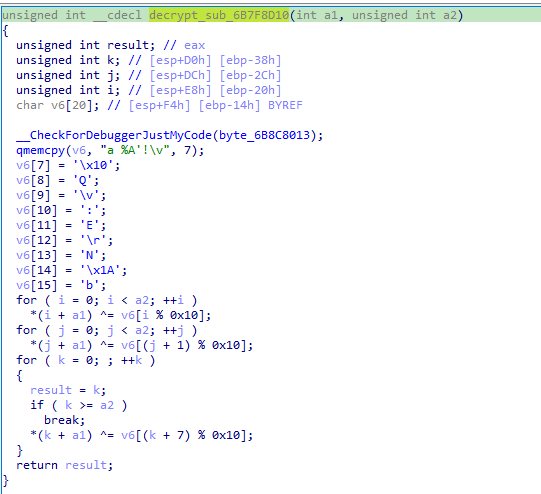
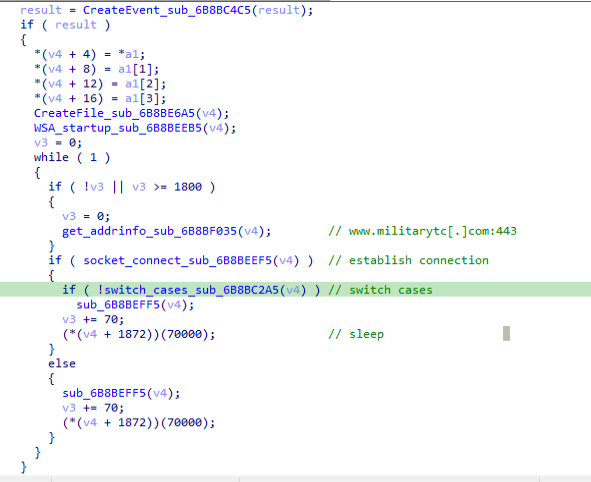
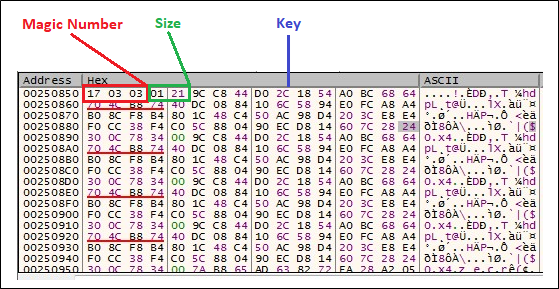
The malware communicates with the command-and-control (C&C) server through the ws2_32.send API call. It generates a random identifier, gathers the computer name, and sends this information to the C&C server. The C&C protocol is similar to that of its previous variant, as outlined in our past research. However, this variant involves some minor changes. For example, the generated victim ID is now stored to current_directory\CompressShaders for persistence. Also, the handshake packet is slightly different, as shown in Table 1.
| Offset | Size | Name | Description |
| 0x0 | 0x3 | magic | 17 03 03 |
| 0x3 | 0x2 | size | The payload size |
| 0x5 | 0x100 | key | The payload encryption key |
| 0x105 | 0x10 | victim_id | The unique victim ID (generated by CoCreateGuid) |
| 0x115 | 0x1 | reserved | |
| 0x116 | 0x4 | hostname_length | The length of the hostname |
| 0x11A | hostname_length | hostname | The hostname |
The command codes are also slightly different. In this variant, all of the debug strings are removed. It supports command codes 4 through 19 and has the following capabilities:
- Reverse shell
- Delete file
- Move file
Attribution to Earth Preta
For attribution, we believe this variant is more likely associated with Earth Preta. It was distributed using similar TTPs (spear-phishing) and works like the earlier variant mentioned in our previous entry on Earth Preta. It employs CoCreateGuid to generate a unique victim ID, which is stored in a standalone file — a behavior not observed in earlier variants. Additionally, the same C&C server was linked to another sample attributed to Earth Preta, and the shared CyberChef formula still successfully decrypts the packet being sent. Based on these factors, we attribute this variant to Earth Preta with medium confidence.
Trend Vision One
Trend Vision One™ is a cybersecurity platform that simplifies security and helps enterprises detect and stop threats faster by consolidating multiple security capabilities, enabling greater command of the enterprise’s attack surface, and providing complete visibility into its cyber risk posture. The cloud-based platform leverages AI and threat intelligence from 250 million sensors and 16 threat research centers around the globe to provide comprehensive risk insights, earlier threat detection, and automated risk and threat response options in a single solution.
Trend Vision One Threat Intelligence
To stay ahead of evolving threats, Trend Vision One customers can access a range of Intelligence Reports and Threat Insights within Vision One. Threat Insights helps customers stay ahead of cyber threats before they happen and allows them to prepare for emerging threats by offering comprehensive information on threat actors, their malicious activities, and their techniques. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and effectively respond to threats.
Trend Vision One Intelligence Reports App [IOC Sweeping]
- Earth Preta Mixes Legitimate and Malicious Components to Sidestep Detection
Trend Vision One Threat Insights App
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Project Injection to waitfor.exe with hardcoded parameter used by Earth Preta
processFilePath:*ProgramData\\session\\OriginLegacyCLI.exe AND objectCmd:*Windows\\SysWOW64\\waitfor.exe\” \”Event19030000000\” AND tags: “XSAE.F8404”
More hunting queries are available for Vision One customers with Threat Insights Entitlement enabled.
Conclusion
The recent findings of Trend Micro’s Threat Hunting team highlight the sophisticated methods employed by Earth Preta to compromise systems and evade security measures. By leveraging MAVInject.exe to inject malicious payloads into waitfor.exe, and using Setup Factory to drop and execute these payloads, Earth Preta effectively bypasses ESET antivirus detection and maintains persistence on infected systems. Its attack chain demonstrates the group’s advanced level of expertise in developing and refining their evasion techniques, with its use of legitimate applications like Setup Factory and OriginLegacyCLI.exe further complicating detection efforts. Organizations should be vigilant about enhancing their monitoring capabilities, focusing on identifying unusual activities in legitimate processes and executable files, to stay ahead of the evolving tactics of APT groups like Earth Preta.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE





