eBay users spot the online auction house port-scanning their PCs. Um… is that OK?
Users visiting eBay have spotted that the website runs port scans against their computer, using the localhost address to inspect what may be running on your machine.
Fraud is a big issue for eBay and if the purpose of scanning for remote-access ports is an attempt to detect criminals logged into a user’s computer in order to impersonate them on the tat bazaar, it could have some value. The behaviour, however, was described as “clearly malicious” by security researcher Charles Belmer.
The script attempts WebSocket connections to a number of ports, including 3389 (Microsoft remote desktop), 5931 (Ammy Admin remote desktop), 6333 (VNC remote connection), 7070 (realAudio and Apple QuickTime streaming) and more. The script is running locally so it is not testing for ports exposed to the internet, but rather for what is running on your local network. The port scanning script does not always run. We have only seen it run on Windows, and normally only on the first visit to eBay after some unspecified period.
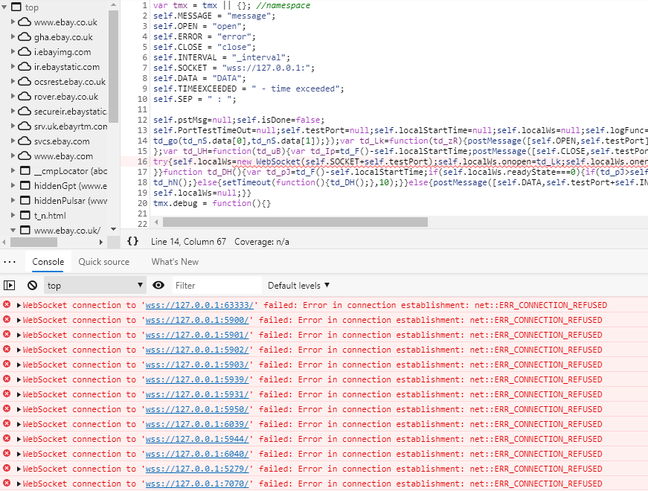
The script used by eBay, or its partner LexisNexis, to scan ports on your computer (click to enlarge)
Developer Dan Nemec used browser debugging tools to trace what is going on – a job made harder, he said, by JavaScript code that is “re-obfuscated on every page load” so that variables names change every time.
It is odd, though: not all the code is obfuscated, so if the script’s creators really wanted to cover their tracks they could have done a better job.
Nemec did discover several points of interest, however. One is that the source of the script, called check.js, is src.ebay-us.com, which is a CNAME record pointing at h-ebay.online-metrix.net, which belongs to an organisation called ThreatMetrix Inc, part of LexisNexis Risk Solutions.
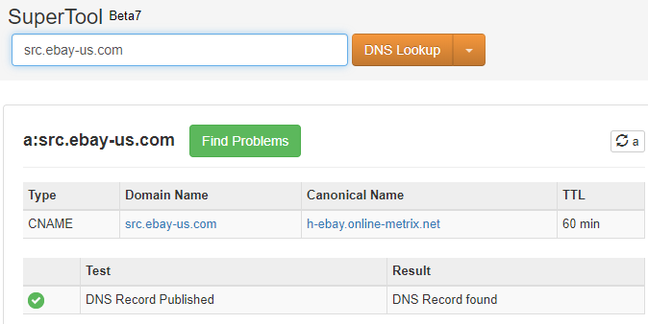
Following the trail … The script is served by online-metrix.net, which is owned by ThreatMetrix, according to tools at MXToolbox
Following the scan, Nemec observed, the web page requests images, again from the Threat Metrix domain, which return a 204 code meaning “no content”. The payload is in the argument accompanying the requests, which when decrypted contains the results of the port scan and other information, including the user agent (browser identifier), public IP address, and “other data, signatures and things I don’t recognize,” said Nemec.
LexisNexis Risk Solutions provides “powerful linking technology… to manage risk and find opportunities,” according to its home page, and promises to help companies “walking the tightrope between fraud and friction”, as they try to give the customer a smooth online experience while also minimising fraud.
In a white paper the company talks about how to “gather ample ‘trust data’ around customers and their linked devices” for which it uses techniques including “device fingerprinting and linking across devices”. This may not refer specifically to the technology in the eBay script, but it is obvious that the company is in the business of gathering data for both fraud prevention and digital marketing.

Bank on it: It’s either legal to port-scan someone without consent or it’s not, fumes researcher
There is no suggestion that eBay is trying to make use of services like VNC to connect to your computer. While it is likely eBay is using the practice to detect fraud, there are a number of issues concerning privacy, consent and security. The Register has come across ThreatMetrix before, when Halifax bank was found to be conducting port scans, with some claiming that the practice was in breach of the UK’s Computer Misuse Act. The bank retorted that it was perfectly legal and argued that the port scans helped it to pick up evidence of malware infections on customers’ systems.
The EU’s General Data Protection Regulation (GDPR) – already transposed into law in the UK – is another relevant piece of legislation, setting out the conditions for when gathering personal data is lawful and giving individuals rights to obtain and erase personal data in most circumstances.
There is also the question of under what circumstances web browsers should allow requests to services running on localhost. A year ago, the Zoom web-conferencing software was found to using a request to a local web server to open its application from a web page, with the result that “a malicious attacker is able to forcibly join anyone with the vulnerable software installed into a video call with their camera active by default”.
We have asked both eBay and LexisNexis for comment. ®
Sponsored: How to simplify data protection on Amazon Web Services
READ MORE HERE
