Enterprises Rely on Multicloud Security to Protect Cloud Workloads
As enterprises move more of their business infrastructure into the cloud, they are grappling with the challenges of managing multiple cloud environments. Security firms are tackling multicloud security through increased visibility, cross-platform implementations, or a combination of the two.
On Thursday, cloud networking firm Aviatrix announced its new Distributed Cloud Firewall security platform that combines traffic inspection and policy enforcement across multicloud environments. The firm uses native cloud platform features and its own technology to give companies a consolidated view into the security of their cloud workloads and the ability to push out the same policies to different clouds, says Rod Stuhlmuller, VP of solutions marketing at Aviatrix.
“The architecture is really what’s new, not necessarily the capabilities of each of the features,” he says. “It’s very different than having to reroute traffic to some centralized inspection point for whatever security capabilities you’re talking about — that just becomes very complex and expensive to do.”
The vast majority of companies (87%) have moved their information infrastructure to a multicloud architecture, with the lion’s share (72%) using a hybrid approach that combines both private cloud infrastructure and public cloud services, according to Flexera’s 2023 State of the Cloud report. Among the top challenges for enterprises are managing their multicloud architectures and the security of their cloud infrastructure, with 80% and 78% struggling with the issues respectively, according to Flexera.
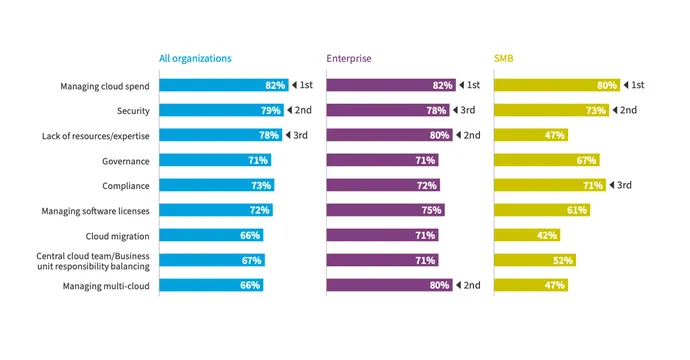
As companies deploy workloads to multiple cloud service providers (CSPs), security can suffer. Because CSPs differ in the way that they handle security policies, inspection of traffic, and deploying workloads, companies can quickly lose visibility into security of their cloud infrastructure, says Patrick Coughlin, vice president of technical go-to-market for Splunk, a data and insights cloud platform.
“Let’s say, maybe, you go to Google for your machine-learning tooling and workloads, you go to Azure for your core corporate business services, and you go to AWS for cost-efficient storage and overall data management — you may even have some homegrown applications that are legacy and highly regulated that you need to keep on prem,” he says. “But what the security team needs is visibility across all of that, and it’s a nontrivial challenge to be able to provide not just that visibility, but the ability to investigate across all of that when something goes bang in the night.”
The Multicloud Security Mess
Initially, many providers created virtual instances of their firewall appliances and set them as gateways to cloud infrastructure, but those virtual firewalls have become increasingly difficult to manage, especially across multiple cloud platforms, says John Grady, principal analyst for cybersecurity at Enterprise Strategy Group.
“Virtual firewall instances have been around for a while, but there’s been an acknowledgement over the last couple of years that these deployments can be complex and cumbersome and don’t take advantage of the key benefits the cloud offers,” he says. “So we’ve seen a general shift towards more cloud-native network security solutions.”
With more organizations using multiple infrastructure-as-a-service (IaaS) solutions from the top cloud companies — Amazon Web Services, Microsoft Azure, and Google Cloud Platform — finding a solution to the growing complexity is critical.
Aviatrix, for example, allows companies to create an abstracted policy that can be applied across all the cloud platforms using their native security groups, without the administrator needing to go to each cloud. For companies with proliferating workloads, driven by microservice-based software architecture, the number of containers and virtual machines that need to be updated can skyrocket, Stuhlmuller says.
“It’s not that we’re putting firewalls everywhere, but we’re putting the inspection and enforcement capability into the network into the natural path of traffic, with a [single management console] that allows us to do central creation of policy, but push that distributed inspection enforcement out everywhere in the network.”
Other major vendors that focus on cloud workload security, albeit with differing takes on the technologies, include Palo Alto Network, McAfee Enterprise, Trend Micro, Rapid7, and Check Point Software Technologies, according to Forrester Research, a business-analysis firm.
Saving Money Becomes Paramount
With uncertain economic times worrying the executive suites, cost savings may be the biggest argument for businesses to consolidate their view of their cloud infrastructure. A security architecture based in the cloud and representing every cloud platform in the same way helps companies more efficiently secure their cloud services, but the approach also has the real benefit of being able to save money, says Andras Cser, vice president and principal analyst at Forrester Research.
“Multicloud security cuts costs,” he says. “Organizations do not have to invest in procuring and training for multiple cloud providers’ security solutions. They can, instead, use a single provider or cloud provider to source all cloud security capabilities from one tool — this reduces errors, improves security posture, and cuts costs.”
In addition, consolidating some features leads to cost efficiencies. Distributed firewalls, for example, have the ability to run network address translation (NAT) and charge per hour, as opposed to many vendors who charge per hour and by bandwidth, according to Aviatrix’s Stuhlmuller.
Finally, a simpler approach to security in the cloud helps companies reduce the overhead of securing workloads and allows their security professionals to focus on improving the security maturity, says ESG’s Grady.
“Many organizations continue to struggle with the skills shortage and are trying to do more with less,” he says. “There’s an efficiency benefit with a ‘write-once, enforce everywhere’ model, as well as time savings from not having to deploy individual instances and the associated cloud infrastructure — such as load-balancers — to support them.”
Read More HERE
