Essential Strategies for Securing Smart Factories

Digital Transformation
With Industry 4.0, manufacturing organizations need to recognize the unique threats and risks facing them, and strategize towards addressing them.
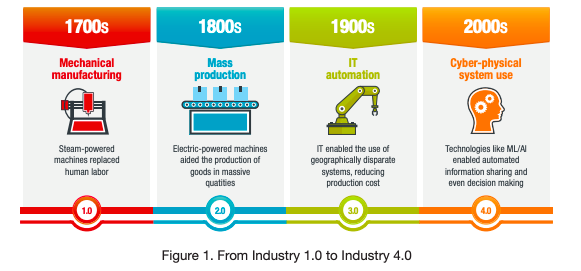
The next industrial revolution is officially upon us. The interconnected nature of Industry 4.0 drives digital transformation in manufacturing—as information technology (IT), operational technology (OT), and intellectual property (IP) all converge within “smart factories.” But like any widespread advance within the technology sector, Industry 4.0 brings forth its own set of challenges. Integrating an organization’s IT infrastructure with the OT and IP sides of the business means that the attack surface—and risk—increases significantly. Looking towards the future, Trend Micro provides a strategy for C-level IT and security executives to follow when considering the security implications, network architectures, technologies, processes, and reporting lines being ushered in alongside the deployment of these new technologies.
Implementing Industry 4.0 Securely with Foresight
Industry 4.0 requires the convergence of IT and OT networks1, centralization and specialization of manufacturing, and the integration of protocols and devices that were not designed to be part of a TCP/IP world.
Manufacturing equipment has long life cycles, with computers and related equipment lasting an average of nine years before replacement or decommissioning2. Industry 4.0 adoption—where equipment and systems in the production line are able to communicate with one another—will take years, perhaps even a decade, to be realized. In the meantime, we see an industry that is slowly evolving by replacing equipment piece by piece.
Cybersecurity features need to be integrated into the design of the equipment in order to make maintenance and protection easier in a highly connected factory network. Otherwise, the cybersecurity team will be forced to implement less than optimal workaround solutions that may cost more to implement or be difficult to set up and maintain, reducing the significant potential operational benefits of connected manufacturing.
“Cybersecurity features need to be integrated into the design of the equipment in order to make maintenance and protection easier in a highly connected factory network.”
Advanced Technologies, Advanced Threats
Although industrial cyberespionage has normally been the realm of advanced and persistent attackers, we have seen increasing cybercriminal interest in targeting the industrial and manufacturing sectors with the rise of Industrial Control Systems (ICS)/Supervisory Control and Data Acquisition (SCADA)-specific hacking tools being sold and advertised online. In fact, as a part of our research and exploration of Industry 4.0, in 2018 the Zero Day Initiative™ was the top supplier of vulnerabilities for ICS-CERT. As there are OT administrators or engineers who use these tools legitimately, the gray nature of these threat actors makes it possible for attackers to read and modify the logic of hacked programmable logic controllers (PLC). In fact, the National Police Agency of Japan issued a 2015 notification regarding an observed increase in scanning activity related to PLCs3. We predict that in a few years, industrial espionage will not only be performed by persistent attackers, but will also become commoditized with tools and services created and offered by common cybercriminals.
Get an in-depth look into IT, OT, and IP threats, alongside valuable security strategy recommendations by reading Securing Smart Factories: Threats to Manufacturing Environments in the Era of Industry 4.0 from Trend Micro.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk
Read More HERE



