ETSI Publishes IoT Testing Specs for MQTT, COAP


ETSI TS 103 596 lays out an overall test suite structure and catalogue of test proposes for CoAP, serving as a guide for both client and server test campaigns. It has three parts—part one specifies the conformance issues, while parts two and three discuss security and performance issues.
On the other hand, ETSI TS 103 597 provides an overall test suite structure and purposes for MQTT. It also has three parts, discussing conformance, security and performance testing.
Lastly, ETSI TS 103 646 specifies testing for selected security requirements as laid out in the IEC 6244-4-2 standards. According to the organization, the chosen requirements have been collected by “defining a dedicated IoT profile”. The resulting profiles then represent a general minimum level of security for IoT devices.
“These new standards fill the gaps for the quality assessment of some of the most relevant communication protocols and system requirements of today’s industrial IoT systems using standardized testing techniques from ETSI,” says Axel Rennoch, Chair of the ETSI working group Testing in TC MTS.
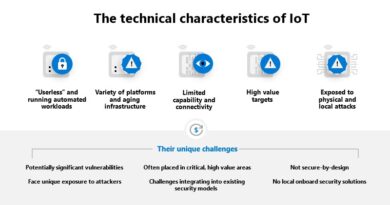
The testing specifications serve as a guide for both users and developers in security testing CoAP, MQTT and foundational security IoT-Profile to strengthen the protocols’ security. However, it is still paramount for enterprises to better understand the risks associated with such protocols.
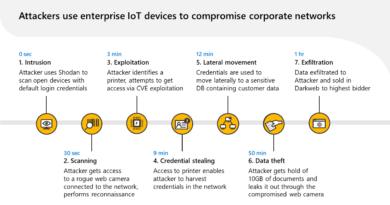
Trend Micro’s 2018 study MQTT and CoAP: Security and Privacy Issues in IoT and IIoT Communication Protocols found that hundreds of thousands of MQTT and CoAP hosts can be reached using public-facing IP addresses. It provides attackers with exposed records in the millions.
According to the study, unsecured endpoints can expose records and leak information. Moreover, vulnerable endpoints also run the risk of denial-of-service (DoS) attacks.
Organizations and manufacturers must understand and pay better attention to IoT and IIoT security. Security teams must also ensure that proper security mechanisms are in place when using protocols.
To learn more about the security implications of campus networks and blind spots in ICS security, read the following comprehensive analyses by Trend Micro experts:
Read More HERE