Europe’s digital identity system needs patching after can_we_trust_this function call ignored
Security flaws have been found in the European Union’s electronic identity system that could have been exploited by miscreants to impersonate member states’ citizens online.
The programming blunders were buried in the five-year-old eIDAS – that’s electronic IDentification, Authentication and trust Services – that was designed to act as a secure bridge between all the various bureaucracies and ID systems of the 28 countries that make up the world’s largest trading bloc.
Essentially, you can use eIDAS to sign documents, pay taxes, apply for college courses, open bank accounts, access public services, and so on, in one EU country using a digital identity issued by another EU state’s government. For example, a person in France can use their French government-issued electronic ID to access online services in Italy, using eIDAS to identify themselves. All very Brussels, and all a bit complicated.
And it could have been exploited to masquerade as others, somewhat breaking that whole trust-and-verification thing. If you’re running an eIDAS-Node installation – as many member states do – then make sure you’ve updated to version 2.3.1 or higher to avoid these security weaknesses.
The scope of these vulnerabilities, we note, is rather limited: the software is used by countries to talk to the systems of other countries. It could, therefore, potentially, be used by agents of one nation to pretend to be citizens of another nation – or by miscreants that somehow managed to impersonate or compromise an eIDAS-Node deployment, at which point, you’ve got bigger fish to fry.
The real lesson, as explained below, is: check the issuer of cryptographic certificates, and do not ignore return values of functions, especially ones checking whether or not a crypto-key source can be trusted.
We’re told that Wolfgang Ettlinger of infosec biz SEC Consult found and reported the bugs: “During a short crash test SEC Consult identified critical vulnerabilities in the eIDAS-Node software component (EU cross-border authentication). These vulnerabilities could allow an attacker to impersonate any EU citizen,” the firm explained in an advisory on Tuesday.
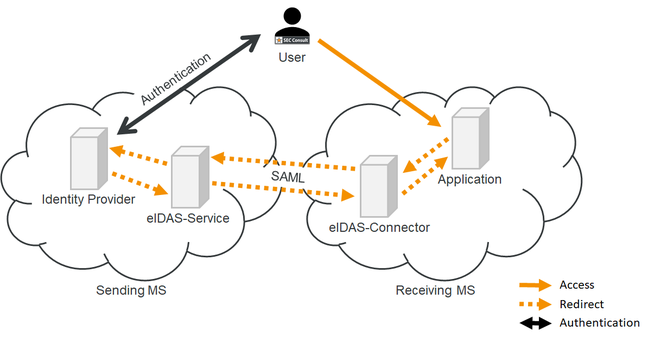
The security house has this example and diagram to illustrate the authentication process:
The holes lurked in eIDAS code that insecurely handled cryptographic certificates passed during the process. The issuer of an entity cert was not validated, and the return value of a validate() function call in the OpenSAML ExplicitKeyTrustEvaluator class to determine whether a certificate should be trusted – true for yes, false for no – was ignored, and the software progressed regardless.
The end result: it was possible to fake security certificates, and thus impersonate strangers.
“SEC Consult recommends to immediately apply the patch provided by the vendor, if this has not happened yet,” it went on. “Moreover, SEC Consult recommends operators of eIDAS-Node installations to conduct a forensic investigation into whether this vulnerability has already been abused.”
The hole, privately reported in July, should have been open for less than a year, the bug hunters reckon, since in 2018 the Ruhr University Bochum in Germany conducted a test on the system that would most likely have spotted the blunder. So it was probably, hopefully, introduced between that audit last year and June this year, when SEC Consult started poking around the source code.
The EU has now released a fix, and a reminder to national administrators to get patching. ®
Sponsored: How to get more from MicroStrategy by optimising your data stack
READ MORE HERE